 SAN FRANCISCO – Down goes Kelihos—again.
SAN FRANCISCO – Down goes Kelihos—again.
The third version of the prolific peer-to-peer botnet responsible for volumes of pharmaceutical spam, Bitcoin wallet theft and credential harvesting was shut down before a live audience today at RSA Conference 2013.
With the execution of a few commands that culminated weeks of intelligence gathering and coding, a CrowdStrike researcher was able to sinkhole thousands of bots before a packed session hall. A heat map of the world lit up like a stoplight with red dots representing bots connecting to the sinkhole rather than to their P2P proxies—a real-time illustration of a successful takedown.
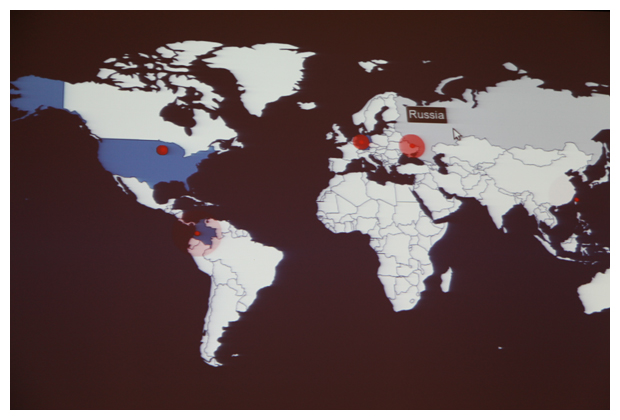
“Every peer that checks into the sinkhole should never talk to the botnet again,” said Tillmann Werner, senior security researcher with CrowdStrike, who had done extensive work with the previous two versions of the botnet.
The cybercrime gang behind Kelihos has been turning a profit with botnets going back to the Storm worm in 2005 and then the Waledec botnet. Kelihos A was disabled in September 2011 after infecting more than 50,000 machines, Werner said. Within three weeks, version B surfaced, this time with 120,000 bots in tow; it was taken down in February 2012. The next version, however, was up and running within 20 minutes, indicating the gang had refined its processes and had replacements ready should a takedown occur. Werner said major changes were made to the protocols powering Kelihos C, forcing him to start reverse engineering from scratch.
Werner said he did not know how many bots made up version C, but that the rate of bots doing their pre-determined check-ins at 30-minute intervals to the sinkhole rather than to the proxies making up the command infrastructure were significant.
In addition to coordinating efforts with law enforcement, including the FBI, as well as with the Shadowserver organization, which hosted some of the infrastructure behind the sinkhole, Werner said previous efforts to shut down version A and B gave him a head start on what he had to do in this instance.
The key effort here was a peer-to-peer poisoning attack that would divert the bots from communicating with the botmaster’s peer-to-peer network. Unlike traditional botnets, there is no direct communication with a command and control infrastructure with a peer-to-peer botnet, making takedowns a little more challenging. Rather than tearing down a massive C&C server, Werner instead focused on an intermediate layer of proxy servers that communicate with a central server hidden somewhere on the Internet.
Werner said he dug deep into understanding the network protocols in play with Kelihos C and determined there were six different message types that ranged from data harvesting and collection to requests for instructions. The key message type was a peer list exchange which told bots which of their peers were recently active, when and for how long. Recently active peers were favored while those that were not active were blacklisted within the botnet.
Werner was able to write a sinkhole daemon that acted like a bot, but instead would send poisoned peer lists to other bots. Once machines would check in with a proxy on the half hour looking for more jobs, they were sent a blacklisted set of IP addresses that included the command and control proxies. The bots, instead, were then pointed toward the sinkhole, and the once blank world heat map began lighting up, symbolic of a mission accomplished.
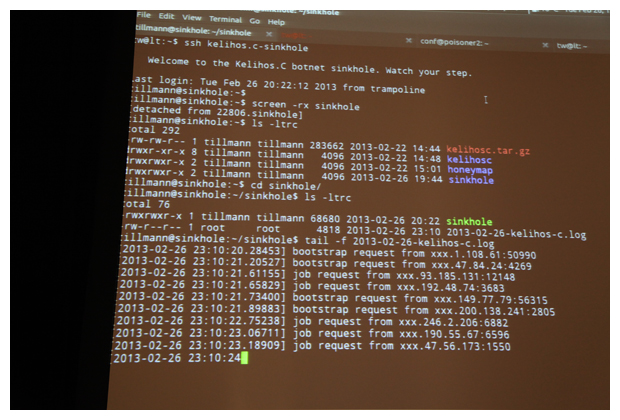
“We wanted it to serve specially crafted jobs that prevent bots from talking to the real command and control infrastructure,” Werner said. “We want to send back our own special jobs so that bots talk to our sinkhole, which records and then drops the traffic.”
Werner said Microsoft would be adding detection signatures to its Malicious Software Removal Tool (MSRT) and that would be pushed out to users during the March Patch Tuesday security update cycle.
“Hopefully that will reduce infections significantly,” he said.










