Check Point has ramped down its projections on the impact of the recently disclosed Fireball malware after Microsoft called its initial numbers into question.
Details on Fireball were published June 1 by Check Point, which said the malware was the work of a Chinese digital marketing agency called Rafotech and that it hijacked browsers for the purpose of ad revenue generation.
Today, Microsoft countered Check Point’s initial analysis that 250 million computers and 20 percent of corporate networks were infected with Fireball.
“While the threat is real, the reported magnitude of its reach might have been overblown,” said Hamish O’Dea of the Windows Defender research team. Check Point said today that it has been working with Microsoft since being notified of the new analysis.
“We tried to reassess the number of infections, and from recent data we know for sure that numbers are at least 40 million, but could be much more,” said Maya Horowitz, Group Manager, Check Point Threat Intelligence.
Microsoft said it has been tracking Fireball infections since 2015 and that the malware has been consistently bundled with programs users are downloading when looking for apps, media, pirated games, or keygens that would activate certain software. The malware arrives in these “clean programs,” Microsoft said, which are used as host processes to load the malware and evade detection by security software.
“In almost three years of tracking this group of threats and the additional malware they install, we have observed that its components are designed to either persist on an infected machine, monetize via advertising, or hijack browser search and home page settings,” O’Dea wrote in a report published today.
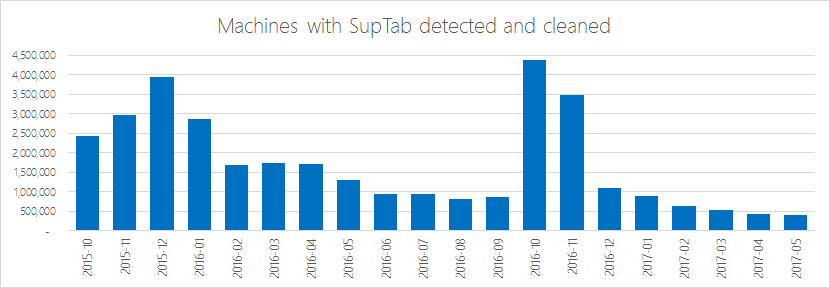
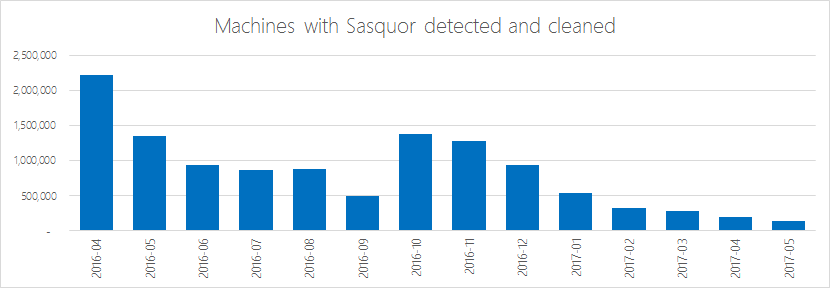
Microsoft detects two malware samples under the Fireball family, SupTab and Sasquor. The payload hijacks a browser homepage and default search settings, modifying browser settings or by changing shortcuts used to launch the browser. The malware’s search page loads without the user’s consent, Microsoft said, and generates revenue from searches for the attacker.
Microsoft said in its report that Check Point arrived at its number of 250 million infections based on the number of visits to search pages, rather than by collecting endpoint device data. With Windows Defender and the Microsoft Software Removal Tool, Microsoft said it is in position to collect what it believes is more accurate data.
It says, based on monthly scans of more than 500 million machines since October when detection for Fireball was added, Microsoft security tools have detected and cleaned 4.9 million SupTab infections and 1.3 million Sasquor infections. Xadupi and Ghokswa infections, two other malware samples dropped in Fireball infections, have been detected and cleaned a collective 4.9 million times.
“Not every machine that visits one of these sites is infected with malware. The search pages earn revenue regardless of how a user arrives at the page. Some may be loaded by users who are not infected during normal web browsing, for example, via advertisements or domain parking,” Microsoft said.
“[Check Point’s] estimates were made from analyzing Alexa ranking data, which are estimates of visitor numbers based on a small percentage of Internet users. Alexa’s estimates are based on normal web browsing,” Microsoft said. “They are not the kind of traffic produced by malware infections, like the Fireball threats, which only target Google Chrome and Mozilla Firefox. The Alexa traffic estimates for the Fireball domains, for example, differ from Alexa competitor SimilarWeb.”
Rafotech denies any wrongdoing, Check Point said in its June 1 report, adding the caveat that Fireball could be tweaked for more than browser hijacking and revenue generation.
“Fireball has the ability to spy on victims, perform efficient malware dropping, and execute any malicious code in the infected machines, this creates a massive security flaw in targeted machines and networks,” researchers said.
According to Check Point, victims are infected with Fireball via stealth installs bundled with desirable Rafotech apps such as Deal Wifi, Mustang Browser, Soso Desktop and FVP Imageviewer. Additionally, it has been distributed via third-party freeware and spam campaigns.