Microsoft announced a cloud-based fuzz testing service called Project Springfield that identifies software bugs in applications that could turn into vulnerabilities.
The service, announced at this week’s Microsoft 2016 Ignite technology conference in Atlanta, combines artificial intelligence and fuzz testing tools to examine Windows binaries, Microsoft said. Code is run through the service which is meant to stress the software into crashing. Examining the cause of the crash could root out a security issue.
Fuzz code tools are not new and date back to the 1980s, but Microsoft hopes to simplify the process and make it fast. By hosting its tools on its Azure cloud platform, Microsoft said a typical developer will have 20 times the scale than server-side testing.
Microsoft Principal Researcher Patrice Godefroid led the development of the fuzzing component, called SAGE. He said that the tool has been in use at Microsoft for nearly a decade helping to identify bugs in Windows and Office. According to Microsoft, Project Springfield was used during the development of Windows 8. In one Windows 8 example, Microsoft said Project Springfield was able to consider about 3 billion scenarios in one-tenth of a second.
SAGE is the centerpiece of Project Springfield, which has been available for about six months through a program that includes a select few customers including OSIsoft, an independent software developer.
“From a software development point of view, fuzz analysis of our code base has helped us tremendously. (SAGE) never stops getting more intelligent. Our code may not change, but threats do. And running our EXEs through Project Springfield continuously helps us stay one step ahead of bugs, crashes and security holes,” said Prabal Acharyya, worldwide director for IoT for OSIsoft.
Sometimes called “whitebox fuzzing,” in a nutshell the technology is a way of discovering bugs in software by providing randomised inputs to programs to find test cases that cause a crash. “Once a crash is detected, if you have the source code, it should become much easier to fix,” writes MWR InfoSecurity in a critical analysis of the technology.
However, MWR notes, that while fuzz testing can eliminate the “data janitor” dilemma of laboriously bug hunting code, fuzzing may “be less likely to trigger bugs that are only triggered in highly specific circumstances.”
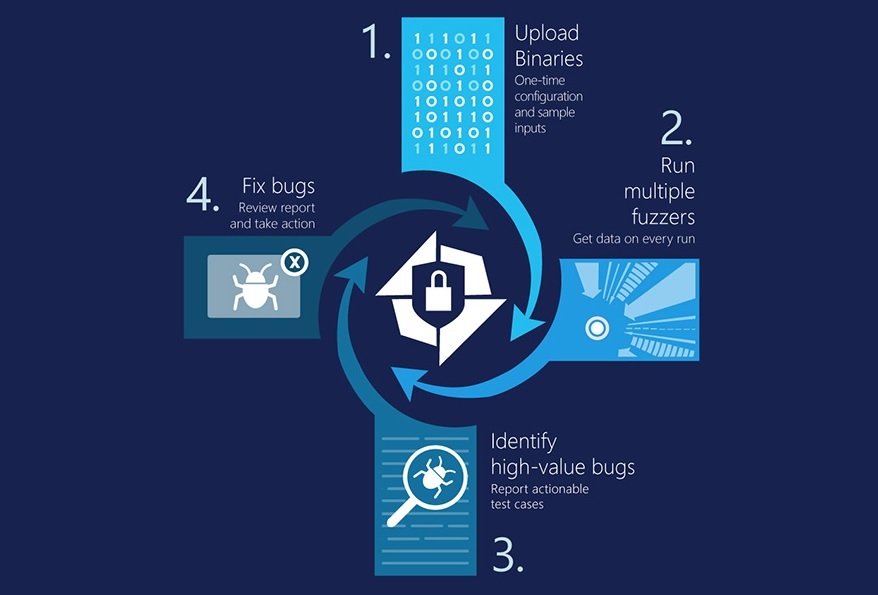
In the case of Project Springfield, the SAGE tool just works on binaries – no source code needed. The software is installed on a virtual machine that runs in the Azure cloud. Next, a “test driver” sets sample inputs, creating test cases that exercise the software.
“Project Springfield will continuously fuzz test using multiple methods, including Microsoft whitebox fuzzing technology,” Microsoft said. “Project Springfield reports security vulnerabilities in real time on the secure web portal… Customer can prioritize and fix bugs. Then re-test to ensure the effectiveness of the fix.”
Project Springfield is still in limited preview and is currently screening for new customers.