Mozilla addressed 29 vulnerabilities, three rated critical, when it released the latest iteration of its flagship browser, Firefox 50 and Firefox ESR 45.5, on Tuesday.
Firefox developers said this week that it might take some effort, but at least two of the critical bugs could be exploited to run arbitrary code. Both bugs stemmed from memory safety issues in Firefox 49, released in mid-September.
According to a security advisory published by Mozilla, both issues showed evidence of memory corruption and were discovered by Mozilla developers and community members.
The other critical bug, a heap-buffer-overflow in Cairo, a programming library that handles 2D rendering for the browser could have resulted in an exploitable crash. Abhishek Arya of Google’s Chrome Security Team is credited for discovering the bug, which Mozilla claims could have been triggered when processing SVG, or Scalable Vector Graphics, content caused by compiler optimization.
Several of the bugs Mozilla fixed that were marked high could have also resulted in potentially exploitable crashes, including two use-after-free vulnerabilities dug up by researcher Nils.
Other issues could have allowed for timing attacks if images were loaded from a third-party location, the installation of extensions without user permission, and in Firefox for Android, the spoofing of a location bar.
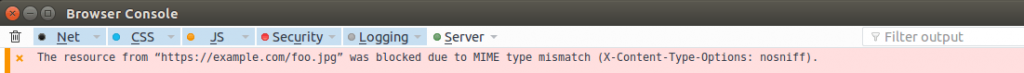
As Mozilla said it would do in August, Firefox now rejects stylesheets, images, or scripts if their MIME type doesn’t match the context in which files are loaded. MIME types, or Multipurpose Internet Mail Extensions types, classify media types.
Doing so reduces the likeliness of the browser being exploited by a MIME confusion attack, according to Christoph Kerschbaumer, a Security and Privacy Engineer with the company at the time. Through a MIME confusion attack, an attacker could craft and upload images that on the surface appear to be image files but actually contain scripting content. Now the browser will display a warning, informing users when files are blocked due to a “MIME type mismatch.”
Two months ago, when Mozilla pushed Firefox 49 it patched a flaw tied to its automated update process for add-ons that stretched to the Tor Browser as well. To exploit the vulnerability an attacker would have had to stolen or forged a TLS certificate and inserted themselves into traffic, something experts speculated would have been a challenge.
The 50th iteration of the browser boasts a host of non-security fixes as well. The new version has a handful of new keyboard shortcuts, download protection for executable file types, and improved video and SDK extension capabilities.