A new malware campaign has been hitting Pakistan hard over the last few months and after a little e-sleuthing, it appears the not-so-stealthy attacks have been originating from nearby India and exploiting a certificate to run its binaries.
Security firm Eset has a full rundown of the campaign today on its WeliveSecurity.com blog by malware researcher Jean-Ian Boutin, including an array of details involving how the attack has been executed and the types of payloads being deployed on unsuspecting Pakistanis’ computers.
This campaign relies on the exploitation of a bogus, digitally signed certificate from the Indian company Technical and Commercial Consulting Pvt. Ltd. Initially issued in 2011 and revoked for files used after March 2012. Still though the cert was still used to sign more than 70 different malicious binaries on and off from that March until September of that year.
The malware uses two vectors – the first is a well-known Word document vulnerability, CVE-2012-0158, that’s been used in everything from the Red October campaign to a bevy of attacks against Tibetan and Uyghur users as of late. The other vector spread Word and PDF files that once opened, “downloads and executes additional malicious binaries.” Some of those files are disguised as “pakistandefencetoindiantopmiltrysecreat.exe” and “pakterrisiomforindian.exe,” according to the blog post.
Payloads are set up to glean data – screenshots, keystrokes, documents in the computer’s trash – from users’ computers and in turn send them to the attackers’ servers. Interestingly enough, as Boutin notes, the information is being uploaded to the attacker’s computer unencrypted, so it’s easy to see what exactly is being transferred.
The blog also notes a number of Indian connections, including the mysterious Indian code signing certificate, references to Indian culture in the binaries and signing timestamps between 5:06 and 13:45, consistent with eight hour shifts worked in India.
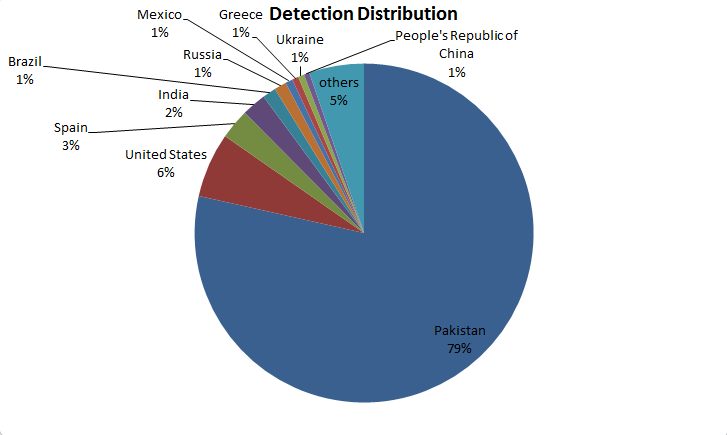
An accompanying graph in the blog entry suggests that while other nations are being hit by the campaign, it’s largely affecting Pakistan, with 79 percent of the targets affecting that South Asian country.
A similar type of malware, Redpill, was found hijacking users in India last month. That campaign also stole screenshots, in addition to bank account credentials and email information and was the second coming of a malware strain that made its first appearance in 2008.
Boutin’s full research on the malware targeting Pakistan is being presented at the Caro Workshop, a security conference in Bratislava, Slovakia tomorrow. For more on his research, head to ESET’s blog.