 There’s a new attack technique in use right now that enables attackers to inject Trojan code onto victims’ machines by disguising it as a Windows input method editor (IME).
There’s a new attack technique in use right now that enables attackers to inject Trojan code onto victims’ machines by disguising it as a Windows input method editor (IME).
The technique is a twist on the classic attack vector of making malicious code look like something benign. In this case, the attack code is being disguised as an IME, which is a component of Windows that’s designed to allow users with one type of keyboard to input characters from other alphabets. The payload in the new attack is a Trojan.
This specific Trojan, when run on a victim’s machine, creates a new file in the System folder, named winnea.ime, according to an analysis by Websense researchers. Once it’s running on the PC, the Trojan then disables any antimalware software that’s present and attempts to delete the executable files associated with the antimalware product, as well.
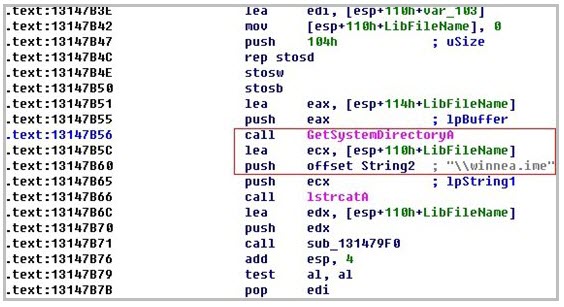
The winnea.ime file itself is a DLL, but in the sample analyzed by Websense it is presented as an IME file and is installed that way, as well. The Trojan also changes the user’s profile in order to set the default IME type to the malicious code. Once the user runs the IME file, the Trojan loads a file that looks for any running AV processes.
From there, the malware loads another file as a driver process and then calls it in an attempt to stop the antimalware software.









