 Android devices have remained a constant target of attacks over the last quarter thanks in part to new variants from the FakeInst and OpFake families of malware. According to the latest version of the F-Secure Mobile Threat Report, the firm found 5033 malicious Android application packages (APKs), a 64 percent increase over the 3063 the firm identified in the first quarter of 2012.
Android devices have remained a constant target of attacks over the last quarter thanks in part to new variants from the FakeInst and OpFake families of malware. According to the latest version of the F-Secure Mobile Threat Report, the firm found 5033 malicious Android application packages (APKs), a 64 percent increase over the 3063 the firm identified in the first quarter of 2012.
The report (.PDF) says that out of the 5000+ APKs analyzed, 19 new families of malware and 21 new variants of previously known families were found. Much like Q1, when 84 percent of the malware found was a Trojan, 81 percent of the variants found in Q2 were Trojans.
One of those variants, a new version of OpFake, a strain of Android malware that sends SMS texts to premium numbers, was found last month fully integrated with a copy of Opera’s Mini browser. Another SMS Trojan, FakeInst, infects systems in a similar way and according to F-Secure can be classified as being in the same family as OpFake due in part to the way they avoid detection. Over the last few months the malware strains have become harder to detect, according to this graphic from the report:
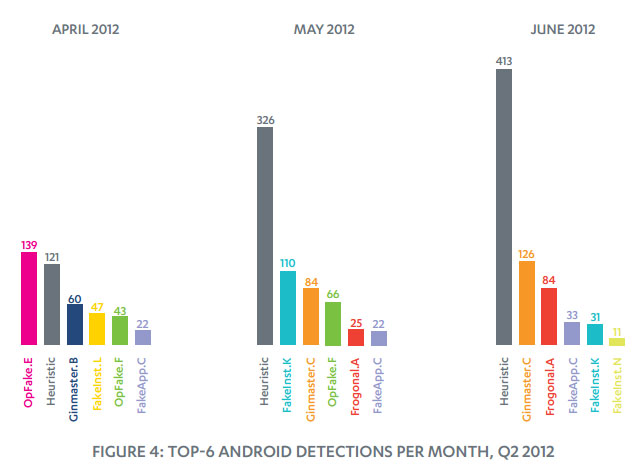
The report also discloses several new methods of infection Android malware has employed over the last several months, including instances where malware is triggered by a drive by download and uses Twitter as a bot.
For more Android malware statistics from the last three months, find F-Secure’s full report here. (.PDF)









