Panera Bread has shut down a massive data leak that revealed the information of potentially millions of customers via its website. The data was exposed for up to eight months after the company was first notified of the security threat.
The incident has shed light on how organizations handle security threats, as well as what role the media and security experts have in holding companies accountable for transparency around security breaches.
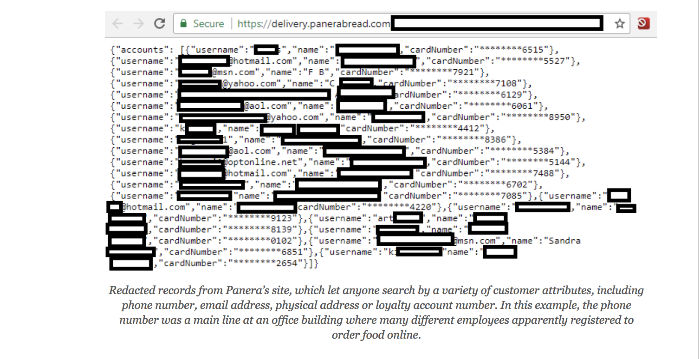
Security journalist Brian Krebs highlighted the data leaks in a post on Monday evening, saying that the data – including names, email and physical addresses, birthdays and the last four digits of credit card numbers – was available in plain text on Panera’s site.
“The data available in plain text from Panera’s site appeared to include records for any customer who has signed up for an account to order food online via panerabread.com,” said Krebs in his post.
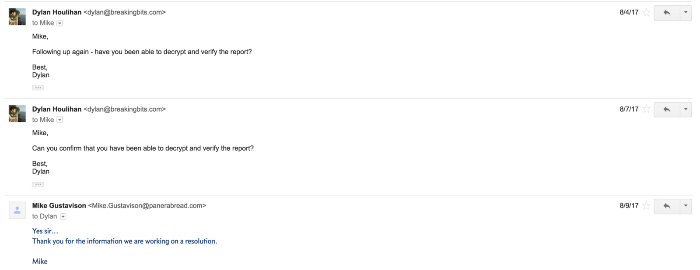
Krebs learned of the breach after being contacted by security researcher Dylan Houlihan, who said he initially notified Panera about customer data leaking from the site back on August 2, 2017.
Houlihan, for his part, said in a recent post that in his initial August exchange with Panera’s director of information security Mike Gustavison, the executive said Panera was working on a response.
However, after eight months and no change, Houlihan reached out to Krebs, who spoke with Panera’s CIO John Meister on Monday. The company then briefly took the website offline while it worked on a fix for the data leak.
“As of this publication, the site is back online but the data referenced above no longer appears to be reachable,” said Krebs in the post.
Panera, which owns 2,000 stores, didn’t respond to multiple inquiries from Threatpost about the timeline, breadth and scope of its website data leak.
However, the company told Fox News on Monday in a statement that “fewer than 10,000 consumers” have been affected by the issue. That number has been disputed by both Krebs and Houlihan.
Krebs told Threatpost that the impacted number of customers that Panera gave seemed low – particularly because when he saw the original URL link, it looked like there were an estimated 7.4 million incremental numbers on record. These records could easily be indexed and crawled by automated tools, said Krebs.
“Only Panera really knows that number but they seemed to be at a loss at estimating the size, so I was taken aback,” Krebs told Threatpost. “It really doesn’t end well for any organization that tries to downplay the breach before they have a handle on the scope.”
On Monday evening, Krebs called out Panera for downplaying the breach in media outlets on Twitter.
I should point out that my tweets of righteous indignation over the last hour were made possible by @HoldSecurity, which jumped to my defense when they saw @panerabread trying to massively downplay this breach on Foxnews. Thank you.
— briankrebs (@briankrebs) April 3, 2018
Furthermore, while Panera took down the original plain text data leak from its main website, Krebs said he has identified data has continued to sit on other parts of the site, such as a Panera’s website for catering.
“My guess is that some of the data is still accessible on the site,” he said. “This could stop if they went and hired someone who knows how to find and fix these problems.”
Hey @panerabread : before making half-baked statements to the press to downplay the size of a breach, perhaps you should make sure the problem doesn't extend to all other parts of your business, like https://t.co/rSpkwc3y1v, etc. Only proper response is to deep six entire site
— briankrebs (@briankrebs) April 2, 2018
“At the end of the day in a lot of ways these breach incidents come down to transparency on the part of the victim organization,” Krebs told Threatpost.
The incident has thrown data security policies around transparency into the spotlight, with multiple angry consumers and security researchers taking to social media to bash the restaurant chain, such as researcher Troy Hunt, who said in a Tweet regulators need to focus on Panera’s situation.
“Panera takes data security very seriously” – Bull. Shit.
This is the sort of incident regulators need to throw the book at. It’s one thing to have a vulnerability, but it’s quite another to ignore it *and* claim you’re taking it seriously. https://t.co/1FRWE3tndP
— Troy Hunt (@troyhunt) April 2, 2018
Others bashed Panera’s public relations team for downplaying the data leak after the security issue became public.
This Panera bread story shows how their security department didn't rise to the occasion. Panera's security team let this vulnerability bake for way too long and ended up getting burned. https://t.co/Ffa7HWLHaH
— Jake Williams (@MalwareJake) April 3, 2018
Terry Rey, CTO of Imperva, said that at a minimum, Panera failed to “either believe and test the first finding of the breach in August.
“They certainly appear capable of fixing the issue as they did quickly today, so why didn’t it happen in August when they were first alerted,” he said. “Panera appears to have had an application security practice in place, so any investigation will likely spend time understanding what Panera monitored of normal versus abnormal activity, did they have a regularly scheduled security assessment run against their public websites, and did they correct poor coding practices once found.”
Houlihan said in a post that until the security industry starts holding companies more accountable for their public statements and transparency when it comes to data leaks, situations like that of Panera’s will continue to occur.
“We could collectively afford to be more critical of companies when they issue reactionary statements to do damage control,” he wrote. “We need to hold them to a higher standard of accountability. I honestly don’t know what that looks like for the media, but there has to be a better way to do thorough, comprehensive reporting on this.”