The market for credential stuffing software and services is thriving thanks in large part to an epidemic of breaches of usernames and passwords.
Digital Shadows said today in a new report that credential leaks, such as this past month’s Anti Public Combo List and others, have buoyed the market for credential stuffing and made it a lucrative part of the black market economy.
Credential stuffing is the automated process of verifying that breached pairs of usernames and passwords work for not only the services that they originated from, but also other services. Popular credential stuffing tools include Sentry MBA, Vertex and Account Hitman, according to Digital Shadows in a report released this week.
“Cybercriminals are increasingly turning to credential stuffing tools to automate attempts at account takeover,” according to the report. Sentry MBA, research said, has a wide online presence and is frequently discussed on criminal forums and marketplaces. “The tool exploits the use of weak passwords and password reuse, as it uses previously leaked credential combinations as part of its attacks.”
Digital Shadows researchers say password reuse is fueling the problem. With one breach, one password could crack open dozens of accounts owned by the same person. Nearly 97 percent of the world’s 1,000 largest companies have had corporate credentials exposed, researchers said.
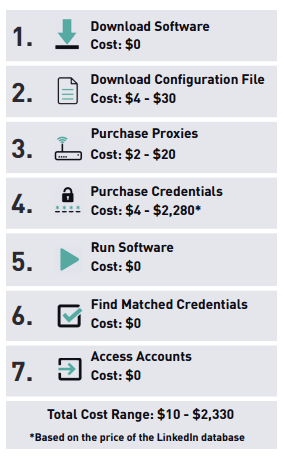 “Downloading of the software itself is free, but there are some associated costs… A credential stuffing attempt can cost anything from $10 to $2,330,” researchers said. Those costs include first and foremost credentials. “One of the most comprehensive (credential) packages cost $2,999, claiming to give you 3,825,302,948 credentials from 1,074 databases,” Digital Shadows said.
“Downloading of the software itself is free, but there are some associated costs… A credential stuffing attempt can cost anything from $10 to $2,330,” researchers said. Those costs include first and foremost credentials. “One of the most comprehensive (credential) packages cost $2,999, claiming to give you 3,825,302,948 credentials from 1,074 databases,” Digital Shadows said.
Next, in order to make the software work, users are required to have a configuration file. The configuration files map out the specific aspects of a target site so the software knows where to attempt logins. Different credential stuffing software also offer different features. For example, SentryMBA claims to have the ability to bypass CAPTCHA protections while Vertex and Account Hitman don’t.
“As you can see, the barrier to entry can be quite low and with these elements in place attackers can be just clicks away from launching account takeover attacks,” Digital Shadows said.
There are a number of mitigation efforts against future attacks that users and business can adopt. Researchers recommend raising user awareness, monitoring for leaked credentials on services such as the Have I Been Pwned website, or deploying an inline web application firewall that can identify and block credential stuffing attacks.
Interestingly, researchers say multifactor authentication (MFA) is no silver bullet in preventing attacks. “There are several instances of threat actors bypassing mechanisms that rely on SMS messages to deliver temporary tokens,” researchers said.
Citing an examples, researchers said banking Trojans Marcher, Retefe and Dridex have been frequently known to employed SMS MFA bypass methods.
“Many organizations are suffering breach fatigue due to the huge numbers of credentials exposed via not only high profile incidents like those suffered by Myspace, LinkedIn and Dropbox, but also from tens of thousands of smaller breaches,” said Rick Holland, VP strategy at Digital Shadows in a statement. “But it is critical that businesses arm themselves with the necessary intelligence and insight to manage their digital risk and prevent this problem credential exposure from escalating into an even more severe problem.”










