Researchers have uncovered a complex espionage platform reminiscent of Duqu that has been used since at least 2008 not only to spy on and extract email and documents from government agencies, research institutions and banks, but also one that targets GSM network operators in order to launch additional attacks.
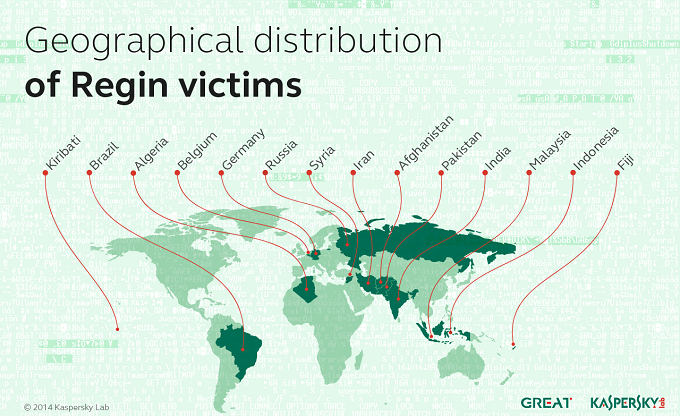
Kaspersky Lab published a report this morning that explains this aspect of the Regin attack platform, which has been detected on the Windows computers of 27 victimized organizations in 14 countries, most of those in Asia and the Middle East. In addition to political targets, Kaspersky Lab researchers identified Belgian cryptographer Jean Jacques Quisquater as one of its specific victims, along with an unnamed research institution that was also infected with other dangerous espionage malware including Mask/Careto, Turla, Itaduke and Animal Farm.
Initial infection vectors are unknown, but Kaspersky Lab speculates that in a few instances, the attackers used a browser zero-day exploit in order to sit in a man-in-the-middle position and siphon traffic from a victim.
“For some of the victims we observed tools and modules designed for lateral movement. So far we have not encountered any exploits. The replication modules are copied to remote computers using Windows administrative shares and then executed,” researchers wrote. “Obviously this technique requires administrative privileges inside the victim’s network. In several cases the infected machines were also Windows domain controllers. Targeting of system administrators via web-based exploits is a simple way of achieving immediate administrative access to the entire network.”
APT-style attacks are characterized by their persistence and ability to quietly steal electronic documents, spread laterally on a network and launch additional attacks on command. The GSM aspect to Regin makes it particularly noteworthy and dangerous, researchers said.
“In today’s world, we have become too dependent on mobile phone networks which rely on ancient communication protocols with little or no security available for the end user,” said Costin Raiu, Director of Global Research and Analysis Team at Kaspersky Lab. “Although all GSM networks have mechanisms embedded which allow entities such as law enforcement to track suspects, other parties can hijack this ability and abuse it to launch different attacks against mobile users.”
GSM is short for Global System for Mobile Communications and is the default standard for mobile networks used by most of the world’s telecoms. The attackers were able to steal credentials from a internal GSM Base Station Controller belonging to a large telecom operator that gave them access to GSM cells in that particular network, Kaspersky Lab said. Base Station Controllers manage calls as they move along a mobile network, allocating resources and mobile data transfers.
“This means that they could have had access to information about which calls are processed by a particular cell, redirect these calls to other cells, activate neighbor cells and perform other offensive activities,” Kaspersky Lab researchers wrote. “At the present time, the attackers behind Regin are the only ones known to have been capable of doing such operations.”
Kaspersky researchers published excerpts from a Base Station Controller log dating back to 2008 that contained commands that would allow a third party to manipulate call forwarding settings, activate or stop cells in a GSM network and add cell neighbors to a network among other commands. The log also contained credentials belonging to engineering accounts.
Backdoors were also established with the attackers’ command infrastructure; communication was heavily encrypted and complex, lessening the chances it would be observed. Machines on a network edge act as a bridge between victims inside the network and the command infrastructure.
“Most victims communicate with another machine in their own internal network through various protocols as specified in the config file. These include HTTP and Windows network pipes,” the Kaspersky report says. “The purpose of such a complex infrastructure is to achieve two goals: to give attackers access deep into the network, potentially bypassing air gaps; and to restrict as much as possible the traffic to the C&C.”
Regin is deployed in five stages giving the attackers deep access to a victimized network with each stage loading subsequent parts of the attack. Modules in the first stage are the only executable stored on the victim’s computer, and they’re all signed with phony digital certificates purporting to be from Microsoft and Broadcom. Details on each stage, as well as indicators of compromise were published by Kaspersky Lab in its report.