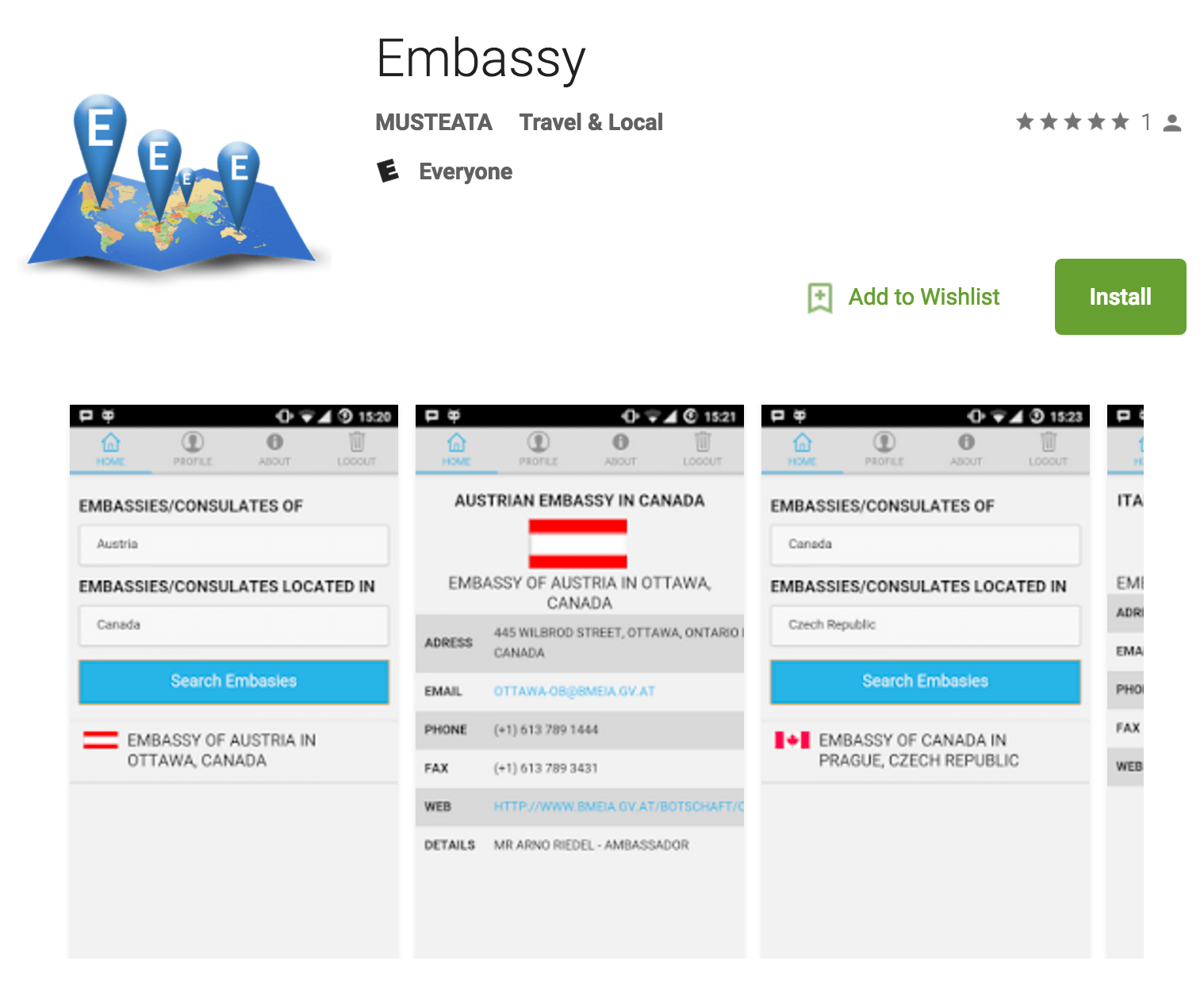
Google booted four spyware-laced apps from Google Play that targeted oversees travelers seeking embassy information and news for specific European countries.
The apps gathered user information from Android phones including: contacts, email, GPS data, phone type, device ID and identified if the phone had been rooted, according to Lookout’s Security Research and Response Team which made the discovery.
Lookout researchers identified the new malware as Overseer and said it discovered the rogue apps in late July. On Aug. 4, Lookout notified Google, which removed the apps from Google Play the same day. The apps were downloaded 10,000 times via Google Play. The apps went by the name Embassy, European News, Russian News and a fourth Russian-language app that used Cyrillic script.
“The legitimate functionality of the Embassy application aimed to provide a user with the ability to search for the addresses of specific embassies in any geographic location. At the time of analysis, the legitimate functionality was not working, however the command-and-control server was active,” said Michael Flossman, a security analyst at Lookout told Threatpost.
An analysis of the apps revealed command-and-control servers located on Facebook’s Parse Server, hosted on Amazon Web Services. “By using the Facebook and Amazon services, the spyware makes use of HTTPS and a C&C residing in the United States on a popular cloud service. This allows it to remain hidden because it doesn’t cause Overseer’s network traffic to stand out and could potentially present a challenge for traditional network-based IDS solutions to detect,” wrote Kristy Edwards and Flossman in a blog post outlining the discovery.
Once the Overseer malware was on a targeted Android device, it would assess what type of additional malware or exploits it might want to download to the phone for the remainder of the attack. “The first stage is profiling the device. The second phase is improving the attacker’s capabilities by downloading additional malicious components,” Flossman said.
Overseer’s ability to sneak onto Google Play, Flossman theorizes, was by virtue of its ability to cloak the malware’s C2 communication via a HTTPS connection to what appeared to be a trusted Facebook Parse Server.
“Google does a great job of identifying if apps are doing malicious things before they are posted on Google Play. However, there are a few known ways to essentially trick Google’s dynamic detection malware analysis system into not raising any red flags.”
In the case of Overseer, the malware polls the api.parse.com server every 15 minutes and looking for instructions. During Lookout’s testing there were no instructions being issued and carried out.
“Nothing malicious was happening on our devices even though we could see through code analysis that this was possible,” Flossman said. He suspects Overseer malware authors had plans to activate malicious code in the future or only target people in specific geographical regions. “Attackers might have code that recognizes a specific location of a victim and under the right conditions they issue instructions to target just those devices. That would evade Google’s malware detection,” Flossman said.