APT groups covet secrets, and one in particular has chosen to target users intent on protecting theirs.
The group is known as StrongPity, and it’s been a characteristic APT outfit using its share of zero days and modular attack tools to infiltrate victims and conduct espionage.
This summer, however, the group took a left turn and began using watering hole attacks to steer its targets toward sites hosting malware-laced versions of WinRAR and TrueCrypt, two free encryption utilities long popular with security and privacy conscious users.
The group was especially active during the summer, Kaspersky Lab researcher Kurt Baumgartner said, hitting many victims in Belgium and Italy primarily, as well as others in Europe, North Africa and the Middle East. Kaspersky Lab released a report today chronicling StrongPity’s activities this summer.
The use of watering hole attacks, where hackers set up on popular sites its targets are likely to visit frequently, malware or redirects to attacker-controlled downloads, is a new one for StrongPity, Baumgartner said. The attackers are hoping to snare users needing to encrypt with WinRAR or TrueCrypt with Trojanized versions of those tools that allow the attackers to spy on data at rest and on the move.
“The problem with people depending on tools like this isn’t the strength of the crypto, but more about how it’s distributed,” Baumgartner said. “This is that problem that StrongPity is taking advantage of.”
WinRAR is a packer utility, encrypting files with AES-256 crypto, while TrueCrypt has had a rocky time the last two years since its developers suddenly closed up shop in 2014 with an ominous warning that the software was no longer safe to use. TrueCrypt, which does full disk encryption, has since been audited twice, including cryptanalysis, and while a handful of vulnerabilities were discovered, no backdoors were discovered as feared.
Nonetheless, TrueCrypt is no longer updated and is still available on Sourceforge and other sources for download. Baumgartner said in his report that many may still opt to use both tools in concert, offering a “poor man’s end-to-end encryption,” especially when used with free file-sharing services such as Filezilla, Putty, Winscp and Windows Remote Desktop Protocol—all of which are targeted by StrongPity’s malware.
“These tools, WinRAR and TrueCrypt are very effective crypto technologies,” Baumgartner said. “What StrongPity is doing is going after low-hanging fruit. They are installing malware so as to observe data encrypted by these apps. They’re hoping to get visibility before encryption happens.”
StrongPity isn’t the first APT to use watering hole attacks to spread its malware; the Crouching Yeti team used Trojanized installers for legitimate ICS and SCADA software to infect critical infrastructure operations worldwide in 2014.
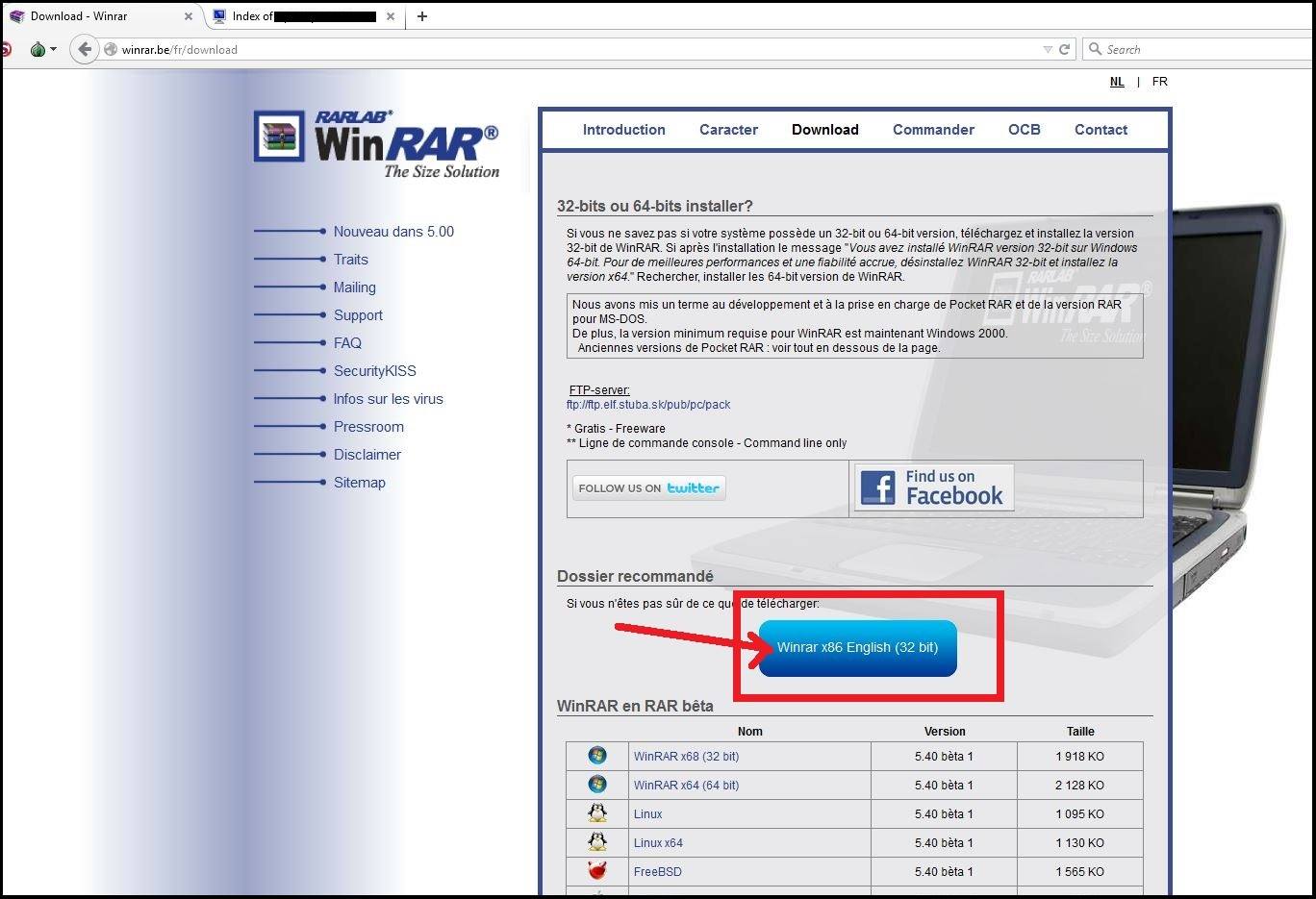
StrongPity’s approach was to set up a domain called ralrab[.]com, which is similar to a legitimate WinRAR distribution site called rarlab[.]com. Baumgartner said the group was able to put links on a distributor site in Europe that would send victims to their Trojanized download rather than to the legitimate software.
In Belgium, StrongPity dropped its redirects on the winrar[.]be distribution page, below, and the first redirects were spotted by Kaspersky Lab on May 28. In Italy, StrongPity infected another distributor site, except this time it was directly infecting users rather than redirecting them to ralrab[.]com. Those attacks started May 24, Baumgartner said.
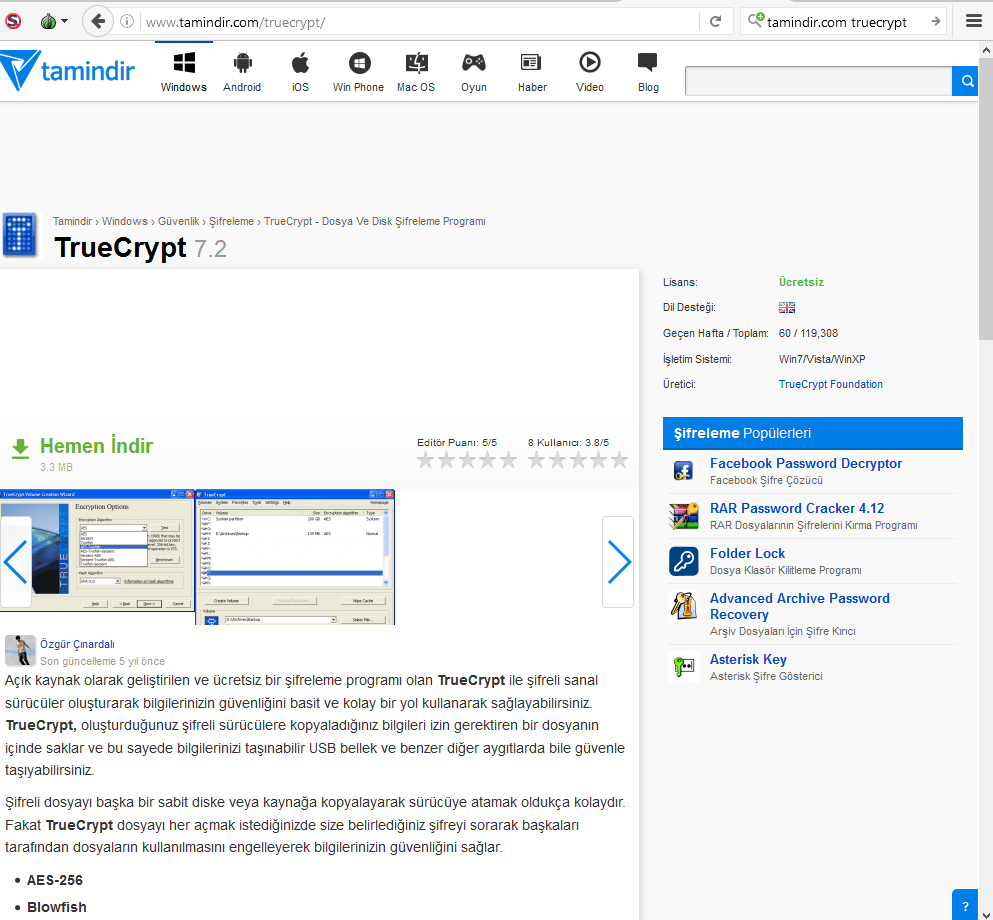
StrongPity also hit localized software sharing sites as recently as last month, redirecting visitors from tamindir[.]com, below, to a domain it controlled called true-crypt[.] where it was serving up Trojanized versions of TrueCrypt.
The APT’s dropper malware was signed with “unusual digital certificates,” Baumgartner said. It downloaded components that not only gave the attackers control of the system, but also allowed them to steal disk contents and download other attacks that would steal communication and contact information.
Among those components was a backdoor that would allow for the attackers to communicate instructions and upload information while the other kept an encrypted list of programs that communicated over encrypted connections, incluing the putty SSH client, the filezilla FTP client, the Winscp secure file transfer program and remote desktop clients.