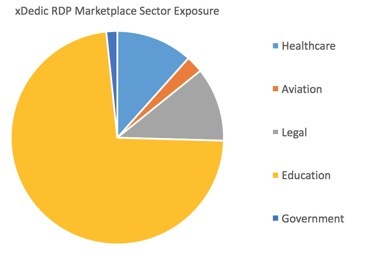
Nearly two-thirds of servers and PCs peddled on the xDedic underground marketplace belong to schools and universities, and most are based in the United States.
In a recent analysis of xDedic, Flashpoint found that besides the education sector, PC and servers tied to healthcare and legal firms make up the bulk of the available vulnerable systems.
XDedic is the largest of many platforms cybercriminals use to buy access to compromised servers and PCs that use the Microsoft protocol Remote Desktop Protocol (RDP). Using brute-force password attacks, the xDedic gang has grown the number of available servers and PCs available for access to 85,000, up 10 percent from a year ago, according to Flashpoint.
Criminals charge $50 to access the marketplace via Tor. Once in, criminals can browse thousands of compromised servers and PCs that can be accessed via a remote desktop session. Typically, access to a PC or server can range between $7 to $15, according to Flashpoint.
 Once a hacker accesses a remote system they can steal data, move laterally within a corporate network or install malware.
Once a hacker accesses a remote system they can steal data, move laterally within a corporate network or install malware.
“XDedic is the most prolific of these cybercriminal gangs. They have their own proprietary tools and techniques and have been prospering over the past year,” said Vitali Kremez, senior intelligence analyst at Flashpoint.
In its research, Flashpoint said the United States, Germany, and Ukraine appear to be the most frequently targeted countries. The most exploited sectors are education, followed by healthcare, legal, aviation, and government. Least vulnerable to these types of attacks are the financial and telecom sectors.
“Schools appear to be the hardest hit because they have the least mature security departments and just can’t effectively mitigate against these type of attacks,” Kremez said. “Schools also sometimes have large banks of RDP systems for students to access and play with.”
When it comes to being targeted by these types of attacks, Kremez said, the leading factors are a lack of computer hygiene, the number of external RDP servers available and systems that have notoriously bad passwords.
Over the past year, the xDedic market has had its ups and downs. XDedic’s original domain (xdedic[.]biz) disappeared shortly after a Kaspersky Lab report (PDF) published in June described how xDedic provided a platform for the sale of compromised RDP servers. A month later in July, the xDedic market resurfaced, this time on a Tor domain, where it remains today.
“Microsoft Windows is the most popular of the platforms targeted by these type attacks,” Kremez said. “Simply put, Windows is the most prolific system out there. When a criminal is looking to find the biggest easiest target with the highest probability of a successful infiltration, Windows is it,” he said.
As for Microsoft, Kremez said, it is constantly updating its RDP software to thwart bad guys. “The weakest link isn’t software. It’s the human factor and a failure to secure servers and client PCs to begin with. Often times people misconfigure their RDP server or give them passwords that are just not adequate.”










