Attackers have taken a liking to a content-injection vulnerability disclosed last week and patched in WordPress 4.7.2 that experts say has been exploited to deface 1.5M sites so far.
The issue has evolved into “one of the worst WordPress related vulnerabilities to emerge in some time,” researchers with WordFence, a Seattle-based firm that makes a WordPress security plugin, said Thursday.
WordPress silently patched the issue, an unauthenticated privilege escalation vulnerability in a REST API endpoint, when it pushed version 4.7.2 on Jan. 26. A core developer with the CMS said the following week that it waited to disclose the vulnerability to ensure that millions of additional sites could deploy the update. WordPress has a feature that automatically updates the CMS on the majority of sites, but some users elect not to use it, instead test updates before pushing them.
Mark Maunder, WordFence’s Chief Executive Officer, said researchers saw the biggest spike in attacks on Tuesday this week when the company blocked roughly 13,000 attacks from 20 different campaigns.
That’s a significant uptick from earlier this week, on Monday, when researchers with Sucuri, the firm that first reported the issue to WordPress, said they had initially seen more than 66,000 webpage defacements from four different campaigns.
The reason for the influx, Maunder said, is because at the beginning of the week attackers refined their attacks to bypass a rule that WordFence and other companies had implemented. While WordFence was quick to engineer a new rule to prevent the bypass, attackers were still able to succeed in infecting a slew of sites–more than 800,000 over a 48-hour period from Tuesday to Wednesday–he said.
In some instances, hackers are competing to compromise sites that haven’t yet applied the fix. WordFence researchers claim they’ve come across some sites where multiple hackers attempt to take credit on multiple pages for hacking them. The defacing and re-defacing will likely continue until those sites apply the 4.7.2 fix, Maunder says.
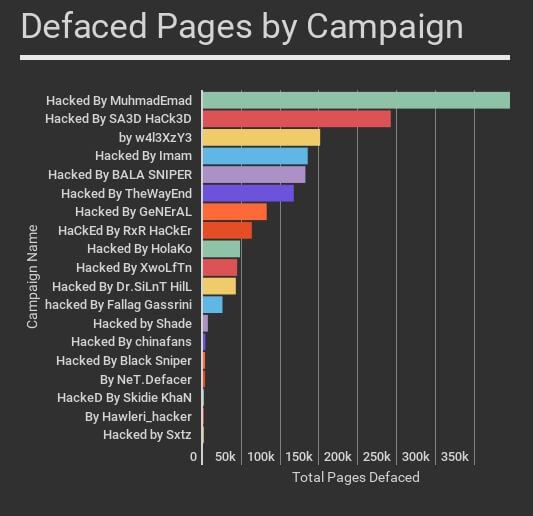
More than 350,000 pages have been defaced by one campaign alone according to Maunder. The campaign, dubbed MuhmadEmad, drops a file, krd.html, on the site and in most instances, defaces the homepage to display the flag of Kurdistan. Beneath the flag, in Comic Sans, reads the text “KurDish HaCk3rS WaS Here.”
Sucuri said on Monday that the largest campaign that it had seen to that point had defaced just 66,000 webpages running vulnerable versions of WordPress.
Sucuri researcher Daniel Cid said Thursday that attackers may soon stop defacing sites and attempt to monetize the vulnerability.
Cid said in a blog post that researchers had recently observed remote command execution attempts trying to exploit the REST API vulnerability in the wild. Attackers in particular are trying to exploit sites that run plugins such as Insert PHP and Exec-PHP which allow users to insert PHP code directly into posts. By combining the two vulnerabilities, an attacker can execute PHP code while injecting content into the database.
There’s not a lot of money in defacing sites, but Cid believes that by trying to execute commands on vulnerable sites, attackers likely are trying to cash in on the vulnerability. Once an attacker has access to a site they can manipulate it through SEO, affiliate links, and ad injections, he wrote.
“Defacements don’t offer economic returns, so that will likely die soon. What will remain are attempts to execute commands (RCE) as it gives the attackers full control of a site – and offers multiple ways to monetize – and SPAM SEO / affiliate link / ad injections,” Cid wrote Thursday. “We are starting to see them being attempted on a few sites, and that will likely be the direction this vulnerability will be misused in the coming days, weeks and possibly months.”
Both firms are encouraging WordPress users, especially those running the vulnerable 4.7 and 4.7.1 versions, to update to 4.7.2.