Google has removed a phony WhatsApp download from Google Play and suspended the developer’s account, but not before the ad-spewing app was downloaded more than one million times.
The unwanted app, called Update WhatsApp Messenger, was disclosed by a handful of Redditors over the weekend who said the adware was also calling out to the internet for additional Android APK downloads to their devices.
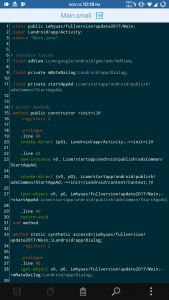
“I’ve also installed the app and decompiled it (at right). The app itself has minimal permissions (internet access) but it’s basically an ad-loaded wrapper which has some code to download a second apk, also called ‘whatsapp.apk,” said a Reddit user with the handle Dextersgenius. “The app also tries to hide itself by not having a title and having a blank icon.”
Google confirmed the app was removed and the developer’s account suspended for program policy violations.
Despite Google’s documented success at catching malicious and unwanted mobile apps on Google Play and removing them from user’s devices, this one snuck through. Like other recent spammy and adware-laden campaigns, the developer used a hidden Unicode character to make this app look legitimate.
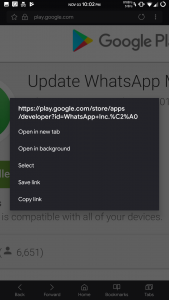
One Redditor with the handle rookie_e pointed out that the listing for this app included an extra space after the name: “WhatsApp Inc. ” The space was instead a Unicode character that looked like a space with a hex code C2A0 allowing it to slip past Google’s malware scanners for its marketplace.
Android apps that are submitted to Google Play are first scanned for malware and behaviors that would classify it as a potentially unwanted app before they are published. Google has taken steps as well to catch malicious apps earlier in the process while still facilitating legitimate app developers.
In May, Google introduced Play Protect, a new security feature that maintains some oversight on content downloaded to Android devices. For example, previously downloaded apps can be continually scanned for malicious behaviors as a counter to developers who push benign apps to Google Play that later connect and download malicious components. This also helps provide a line of defense against apps downloaded from third-party stores that aren’t subject to Google’s malware scanners. Google said in May that Play Protect will be capable of scanning and verifying up to 50 billion apps on a daily basis.
Unicode, meanwhile, remains an apparently solid strategic option for unscrupulous developers who want to slip these types of unwanted apps and even extensions onto Google Play and the Chrome Store, respectively.
Three weeks ago, Google removed a malicious Chrome extension posing as Ad Block Plus that had been downloaded more than 38,000 times. The popular Swift on Security Twitter account exposed the issue about this and two other extensions, one falsely claiming 10 million downloads. The developer used Cyrillic Unicode characters in the extension name allowing the malicious plugins to again sidestep Google’s malware filters.
Attackers have also used Unicode characters to falsify domain names, creating the potential for phishing attacks at scale. Google patched weakenesses in Chrome in April that facilitated this type of abuse. The flaw, known as Punycode, relies on tricking Chrome into bringing users to sites that appear legitimate. The sites could then convince victims to enter personal login or financial credentials.