A full 70 percent of applications being used today have at least one security flaw stemming from the use of an open-source library.
According to Veracode’s annual State of Software Security report, these open-source libraries – free, centralized code repositories that provide ready-made application “building blocks” for developers – are not only ubiquitous but also risky.
The analysis examined 351,000 external libraries in 85,000 applications, and found that open-source libraries are extremely, extremely common. For instance, most JavaScript applications contain hundreds of open-source libraries – some have more than 1,000 different libraries. In addition, most languages feature the same set of core libraries.
“JavaScript and PHP in particular have several core libraries that are in just about every application,” according to the report.
These libraries, like other software, have bugs. The issue is that thanks to code re-use, a single bug can affect hundreds of applications.
“Prominent in almost every application today, open-source libraries allow developers to move faster by quickly adding basic functionality,” according to Veracode. “In fact, it would be nearly impossible to innovate with software without these libraries. However, lack of awareness about where and how open source libraries are being used and their risk factors is a problematic practice.”
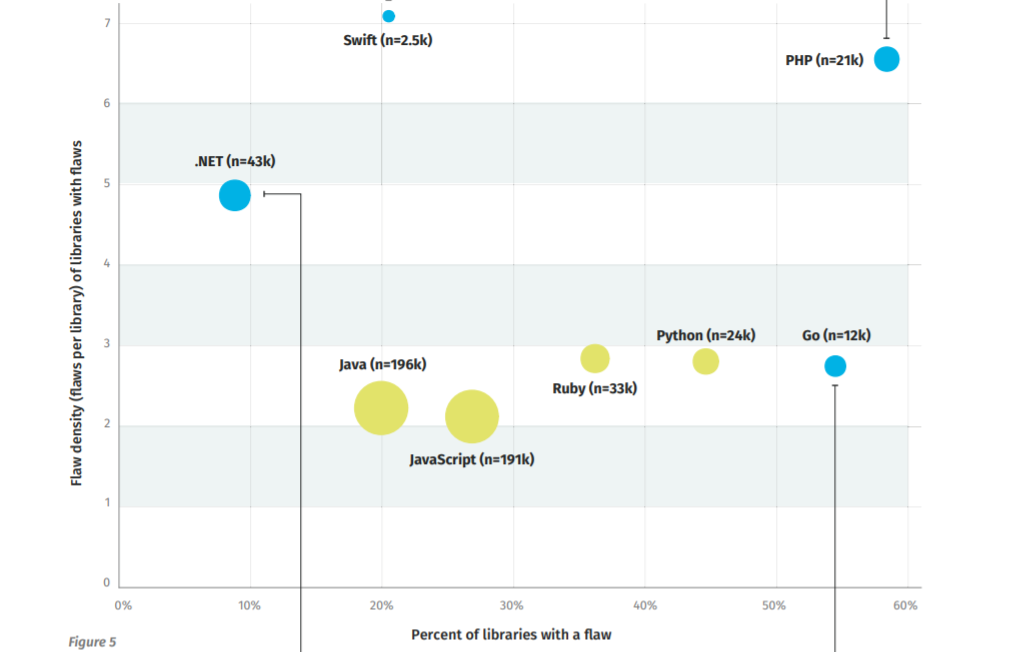
Four main libraries represent the majority of the open-source bugs found in applications: Swift, .NET, Go and PHP.
Swift has specialized use in the Apple ecosystem, and has the highest density of flaws, according to Veracode. However, it also has an overall low percentage of flawed libraries in terms of volume.
.NET meanwhile has the lowest percentage of flawed libraries out of the four, and on a population that is more than 17 times larger than Swift.
Go has a high percentage of libraries with flaws, but an overall low number of flaws per individual library. And PHP has a higher rate of flawed libraries than Go – but more double the density of flaws in a given library.
The firm also found that cross-site scripting (XSS) is the most common vulnerability category found in open-source libraries – present in 30 percent of them. This is followed by insecure deserialization (23.5 percent) and broken access control (20.3 percent).
“We found insecure deserialization was a relatively rare flaw among in-house applications (ranking eighth out of 10),” according to the report. “Having such a high ranking when looking at libraries is troubling as this category of flaws can result in unexpected code paths being executed, which means that portions of libraries that we are not even intending to use may be inserted into the execution path of their hosting applications through use of this flaw.”

Percentage of bug types found stemming from open-source. Click to enlarge.
The data also showed that most flawed libraries end up in code indirectly – thanks to cascading interdependencies. Developers might use one library – but unbeknownst to them, the library that they’re using has pulled in code from an entirely different open-source library to underpin it.
“Forty-seven percent of the flawed libraries in applications are transitive – in other words, they are not pulled in directly by developers, but are being pulled in by the first library (42 percent are pulled in directly, 12 percent are both). This means that developers are introducing much more code, and often flawed code, than they might be anticipating.”
The good news is that addressing security flaws in these libraries is not a huge lift.
“Most library-introduced flaws (nearly 75 percent) in applications can be addressed with only a minor version update; major library upgrades are not usually required,” according to the Veracode report. “This data point suggests that this problem is one of discovery and tracking, not huge refactoring of code.”
Concerned about the IoT security challenges businesses face as more connected devices run our enterprises, drive our manufacturing lines, track and deliver healthcare to patients, and more? On June 3 at 2 p.m. ET, join renowned security technologist Bruce Schneier, Armis CISO Curtis Simpson and Threatpost for a FREE webinar, Taming the Unmanaged and IoT Device Tsunami. Get exclusive insights on how to manage this new and growing attack surface. Please register here for this sponsored webinar.











