Researchers are warning that the websites of eight U.S. cities – across three states – have been compromised with payment card-stealing Magecart skimmers. The websites all utilize Click2Gov municipality payment software, which was previously involved in data breaches.
Unlike other skimmers, which grab data on various types of payment forms on websites, the skimmer in this incident appears to only target website payment forms by Click2Gov. Click2Gov software is used in self-service bill-paying portals used by utilities and community development organizations for things such as paying parking tickets online.
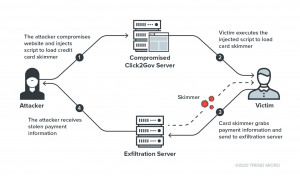
“The attack occurs when victims make an online payment on the compromised Click2Gov website,” said researchers with Trend Micro in a Friday analysis. “JavaScript code was injected into the payment page which loads a credit card skimmer when victims browse the payment page.”
The skimmer is extremely simple; no obfuscation or anti-debugging techniques were used. It hooks the “submit” event of the payment form, so that when a victim clicks the button to submit their payment information, the skimmer will grab the information from the selected columns inside the payment form and immediately send the collected information to a remote server via a HTTP POST request.
Cybercriminals targeted the credit-card information (including card number, expiration date and CVV), name and contact address for the website users.
“We were able to identify two of the exfiltration servers used in the attack,” said researchers. “Both hosted the actual JavaScript skimmer, as well as a .JSP file used to receive the exfiltrated data. One of the servers was used for three sites, while the other server used for the remaining five sites. The two skimmers used are identical, save for the change in the hostname of the exfiltration servers.”
When asked if any of the skimmers have been removed from the websites, researchers told Threatpost, “We don’t have access to that information.” However, they believe that these attacks started on April 10 of this year, and are still active.
When asked which city websites were affected in this incident, researchers told Threatpost, “We can’t say,” adding that Trend Micro “prioritizes responsible disclosure of security incidents and chooses not to ‘name and shame’ victims. Our primary goal is to help organizations identify and mitigate these incidents. We have notified the breached parties who will be responsible for handling the situation within each city.”
Previous Click2Gov Breaches
Click2Gov was previously afflicted by a vulnerability (rooted in a compromised Click2Gov webserver) that led to two different data breaches of the websites of several towns and cities using the software.
The flaw was first discovered in December 2018 after continual breaches of it led to the compromise of at least 294,929 payment cards across the country. Overall, 46 confirmed impacted local governments were caught up in this first breach – including Saint Petersburg, Fla. (on October 2) Bakersfield, Calif. (November 14), and Ames, Iowa (December 2).
Then in 2019, the vulnerable municipality payment software was targeted once again, this time part of a breach involving of eight cities in August. Those cities were: Coral Springs, Deerfield Beach, Milton and Palm Bay, Fla.; Bakersfield Calif.; Pocatello, Idaho; Broken Arrow, Okla.; and Ames, Iowa.
Though they did not name the affected cities in this most recent security incident, researchers said that five of the eight cities were also affected in the previous breaches.
A patch was issued for the Click2Gov vulnerability in 2017, but researchers said that the 2018 and 2019 breaches may have stemmed from municipalities not updating their systems.
 However, researchers say, based on an analysis of both the skimmer and the infrastructure, they could not find any connections between this most recent breach and the incidents in 2018 and 2019.
However, researchers say, based on an analysis of both the skimmer and the infrastructure, they could not find any connections between this most recent breach and the incidents in 2018 and 2019.
“It is not clear at this time if this attack which we identified is connected to the earlier breaches, since nothing about their technical details indicate a connection,” said researchers. “The only connection is that five of the affected cities in the current incident were also affected in 2018; while two were included in the 2019 incident.”
The Click2Gov software was developed by Superion, which has since merged with other companies to form a new company called CentralSquare Technologies in July 2018. According to Risk Based Security, there appears to be between 600 to 6,000 installations of Click2Gov indexed.
CentralSquare Technologies did not return a request for comment from Threatpost.
Regardless, the incident show that credit card skimming attacks are still a major threat to online merchants. Magecart in particular has targeted various websites, from the Nutribullet website to an Olympics ticket reseller. And in April, researchers observed a new skimmer from the Magecart Group actively harvesting payment-card data from 19 different victim websites, mainly belonging to small- and medium-sized businesses (SMBs), for several months.
“During 2019, we also saw that academic institutions and hotel chains were targeted by similar attacks. This time, the attacker targeted the websites of various local governments,” said Trend Micro researchers.
BEC and enterprise email fraud is surging, but DMARC can help – if it’s done right. On July 15 at 2 p.m. ET, join Valimail Global Technical Director Steve Whittle and Threatpost for a FREE webinar, “DMARC: 7 Common Business Email Mistakes.” This technical “best practices” session will cover constructing, configuring, and managing email authentication protocols to ensure your organization is protected. Click here to register for this Threatpost webinar, sponsored by Valimail.











