The sting of mobile ransomware grew more painful in 2017 with attacks increasing a whopping 3.5 times in the first quarter compared to the same time a year ago. Behind those attacks were a quarter million Trojan installation packages targeting Android devices that sought to extort between $100 to $500 from victims.
German smartphone users have been targeted the most, however United States users are rapidly becoming attractive targets, according to a report released Monday by Kaspersky Lab titled Ransomware in 2016-2017.
The sharp increase in mobile ransomware in the first quarter of 2017 is an anomaly when considering an overall downturn in attacks between 2015 and 2016. Over that two-year period, mobile attacks fell 4.6 percent from 136,532 users to 130,232.
“The number of users attacked with mobile ransomware in the observed period fell. This could be a sign of successful collaboration between vendors of security solutions, various law enforcement agencies, and other actors,” according to the report.
The spike in attacks during the first quarter of 2017 is attributed to a peak in December 2016 of the Svpeng family of ransomware. Researchers said attacks grew more than threefold.
Unlike PC-based ransomware installed via exploit kits and booby-trapped email attachments, mobile ransomware was chiefly distributed via malicious mobile app downloads of fake mobile video players for viewing adult content or as part of a fake mobile Adobe Flash player download, researchers said.
“Mobile ransomware does not use any vulnerabilities in most cases,” said Roman Unuchek one of the report’s authors and senior malware analyst with Kaspersky Lab. He said purveyors of mobile malware depend on the gullibility of the user and on older Android OS versions. “With newer Android versions there are more security features, so ransomware has to be more shifty on such devices,” he said.
In its analysis, Kaspersky Lab singled out two malware families, Svpeng and Fusob, as dominating the mobile ransomware space. It was the Fusob malware that made up the bulk of ransomware activity. Fusob typically tricks users by pretending to be a multimedia player, called xxxPlayer. Once downloaded, the ransomware blocks users from accessing the device until between $100 and $200 is paid.
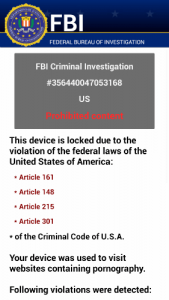 The mobile malware Svpeng was identified in 2013 by Kaspersky Lab as a banking Trojan. Since then it has been modified with ransomware capabilities a number of times. Past social engineering campaigns have been SMS-based and tricked users into downloading the malware. Once installed, Svpeng displays a screen that pretends to be a scanning program. Upon completion it displays a fake FBI penalty notification for downloading “illegal” content. A ransom of about $200 is demanded to unlock the device.
The mobile malware Svpeng was identified in 2013 by Kaspersky Lab as a banking Trojan. Since then it has been modified with ransomware capabilities a number of times. Past social engineering campaigns have been SMS-based and tricked users into downloading the malware. Once installed, Svpeng displays a screen that pretends to be a scanning program. Upon completion it displays a fake FBI penalty notification for downloading “illegal” content. A ransom of about $200 is demanded to unlock the device.
According to the report, countries hit the hardest by mobile ransomware are Germany (23 percent), Canada (20 percent), United Kingdom (16 percent) and the United States (15.5 percent).
The report also revealed that responsibility for most of the mobile attacks rests with just a few groups of malware, most of them spread via affiliate programs.
When compared to mobile, PC ransomware grew 11.4 percent from the previous year. “Among those who encountered ransomware, the proportion who encountered cryptors rose by 13.6 percentage points, from 31 percent in 2015-2016 to 44.6 percent in 2016-2017,” according to the report.
Kaspersky Lab also found the growth of targeted ransomware attacks is on the rise as is the prevalence of ransomware-as-a-service.
“Ransomware is growing in sophistication and diversity, offering a lot of ready-to-go solutions to those with fewer skills, resources or time – through a growing and increasingly efficient underground ecosystem,” according to the report.
On a positive note, Kaspersky Lab said it believes global initiatives, such has The No More Ransom Project, that protect users from encryption ransomware will keep gaining momentum and lesson the sting of both mobile and PC-based ransomware.










