A recently uncovered phishing campaign, targeting PayPal users, pulls out all the stops and asks victims for the complete spectrum of personal data – even going so far as to ask for social security numbers and uploaded photos of their passports.
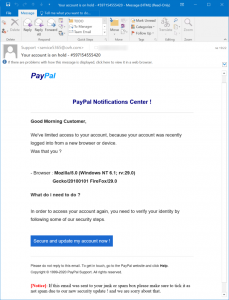
The campaign starts with a fairly run-of-the-mill phishing email, purporting to be from the online payment company’s notifications center, which warns victims that their account has been limited because it was logged into from a new browser or device. The email recipient must verify his or her identity by clicking on a button, which is a bit.ly address that then redirects the browser to an attacker-owned landing page, which asks for a complete rundown of personal data.
The ongoing campaign showcases “the current ‘let’s take all that we can get’ mentality of the attackers quite well,” Jan Kopriva, with the Computer Security Incident Response team at information tech company ALEF NULA, said in a Monday SANS ISC InfoSec Forum post. “Over the years, phishing authors seem to have learned that once they hook a phish, they should try to get all the information they can from them. This is the reason why many current campaigns don’t stop after getting the usual credit card information, but go further.”
Like other phishing campaigns, this particular scam comes with some major red flags. While the initial email sender shows up under the name “Support,” a closer look at the email address shows it is from [service53659(at)ovh.com], rather than a legitimate PayPal email address. Some parts of the phishing email make strange use of exclamation points – For instance, the top of the email says “PayPal Notifications Center !” and the phishing link button reads, “Secure and update my account now !”
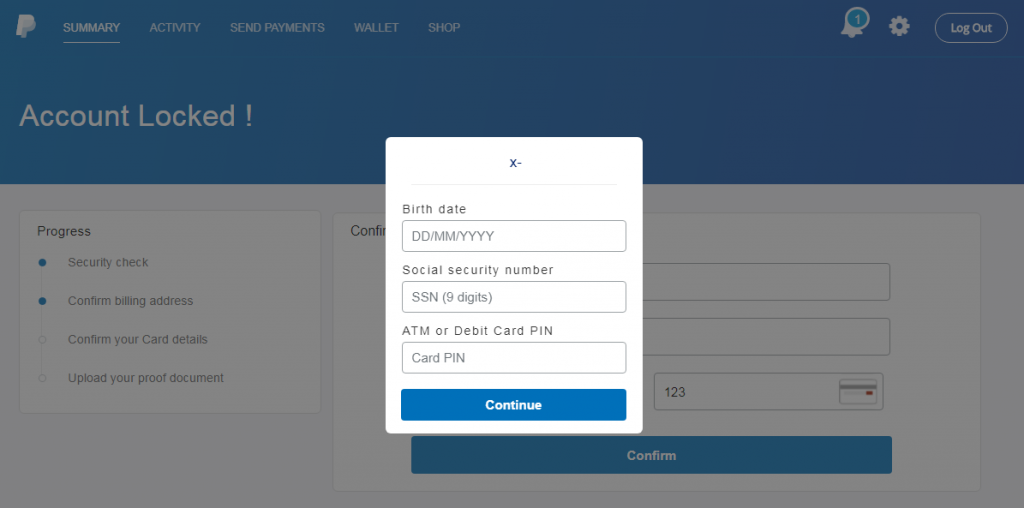
 Also, while the landing page pretends to be a legitimate PayPal login screen with the PayPal brand at the top, the phishing page (https://www[.]leemou[.]com/files/selector/) is clearly not a PayPal domain.
Also, while the landing page pretends to be a legitimate PayPal login screen with the PayPal brand at the top, the phishing page (https://www[.]leemou[.]com/files/selector/) is clearly not a PayPal domain.
However, if victims are gullible enough to enter their credentials, a general information gathering form is then displayed. The landing page at first asks for the victims’ billing information and credit card details, but later takes the campaign a step further and asks victims to fill in a social security number and card PIN number.
If they manage to collect that information, attackers take the scam to the next level, on the last page asking victims to upload photos of their valid government issued photo ID, passport, driving license or credit card.
“What might be a bit unfortunate from the standpoint of a potential victim is that after the user uploads a file, the page is refreshed but no confirmation is displayed,” said Kopriva. “This means that a less vigilant user might upload multiple photos of documents while thinking that their previous attempts were invalid for some reason.”
It’s far from the first scam to involve PayPal. In November, a Utah eye clinic informed 20,000 patients that they were the victims of a data breach that happened a year and a half ago and linked patients to a scam involving PayPal. Recently, the prolific phishing gang known as 16Shop has also added PayPal customers to its target set. Kopriva said he has reported the phishing scam to PayPal. PayPal has said that legitimate emails will always come from a PayPal.com address and will also address customers by their first and last names. Emails will also never ask users for sensitive information like their bank account or password, or contain any attachments, PayPal said in a post about scams on its website.
“Though verifying a correct sender address is important, it’s not enough. It’s important to look at the entire email,” according to PayPal. “When you check your account, always enter “www.PayPal.com” into your browser instead of clicking a link in an email.”
Phishing campaigns continue to hit businesses and personal consumers, usually using updated, tricky tactics to avoid detection or luring victims with trending themes like coronavirus, sporting events like the World Cup and more.
Learn how Operational Technology and Information Technology systems are merging and changing security playbooks in this free Threatpost Webinar. Join us Wednesday, Feb. 19 at 2 p.m. ET when a panel of OT and IT security experts will discuss how this growing trend is shaping security approaches for IoT and 5G rollouts. This webinar is for security and DevOps engineers, IoT edge developers and security executives.