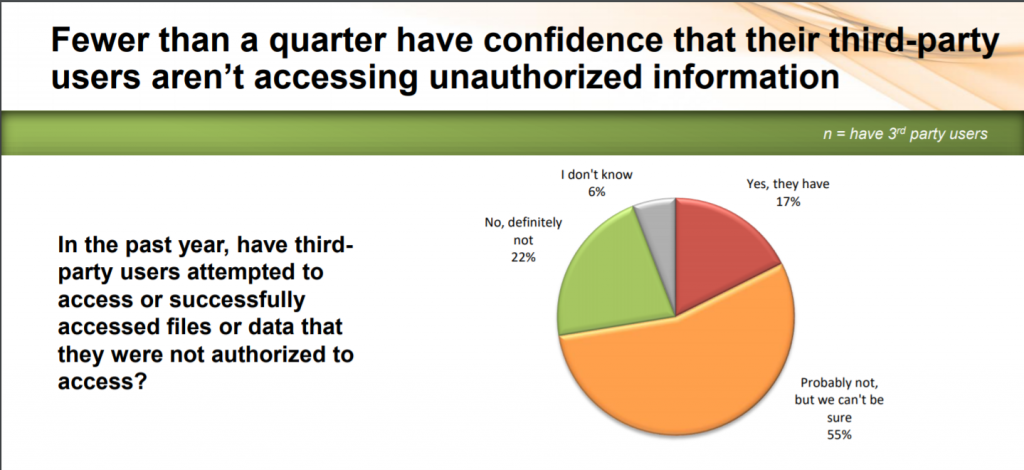
Organizations are continuing to fall down on the job when it comes to addressing cybersecurity risk around third parties; in fact, 61 percent of respondents in a recent survey said they’re unsure if partners, contractors, suppliers and others are accessing or attempting to access unauthorized data.
In an increasingly connected world, businesses are relying on an increasing number of third parties for business services. The survey of more than 1,000 IT security professionals, from One Identity, shows that this lack of visibility comes despite a full 94 percent of respondents giving third-party users access to their networks. Further, the majority (72 percent) of organizations grant these users privileged or superuser permissions, giving them administrative access to sensitive information.
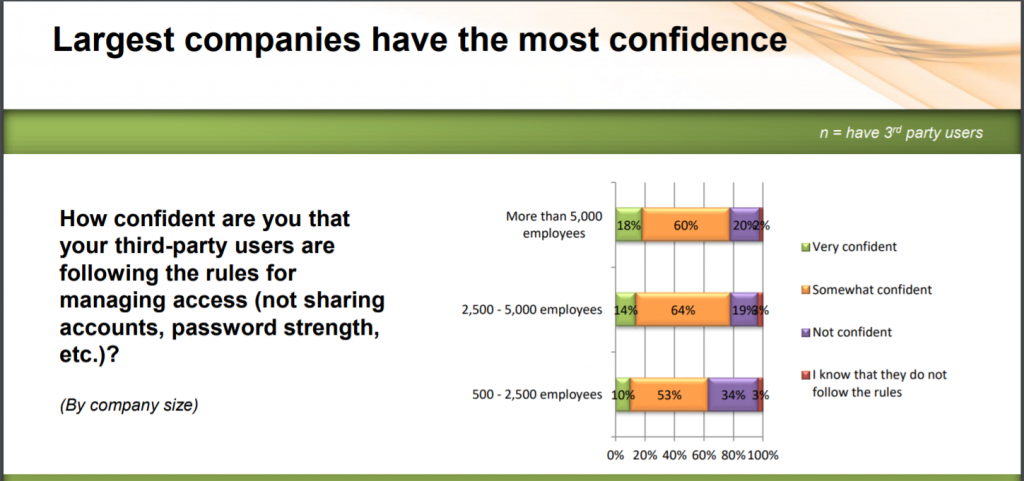
This expands the cybersecurity risk surface, according to One Identity’s report – yet only 15 percent of the respondents said they’re “very confident” that third-party users follow the same access rules as their internal users, such as ensuring password strength.
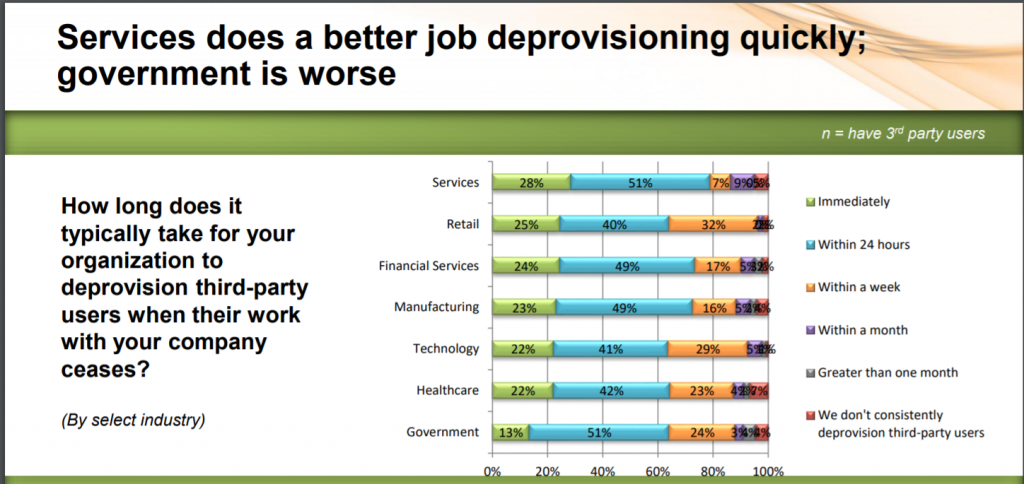
The survey also found that ineffective third-party user lifecycle management practices are widespread, which puts organizations at even more increased risk. For instance, only 21 percent of organizations immediately revoke access for third-party users when the work they do for the company ceases. And about a third (33 percent) of organizations take more than 24 hours to deprovision third-party users.
In terms of verticals, retail is the most at-risk industry when it comes to third-party access: About 28 percent of retail organizations admit third-party users have successfully accessed or attempted to access files or data that they were not authorized to access.
A fifth (20 percent) of financial services organizations, 17 percent of technology organizations and 14 percent of healthcare organizations have experienced the same.
Also, a quarter (25 percent) of respondents from retail organizations say they give all or most of their third-party users privileged access. By comparison, the same holds true for 18 percent of technology organizations, just 10 percent of healthcare organizations and only 10 percent of manufacturing organizations.
“Third-party users are necessary in the day-to-day operations of most modern organizations; however, if third-party access is improperly managed, the security risk associated with these users is detrimental,” said Darrell Long, vice president of product management, One Identity, in a media statement. “Organizations must recognize that their security posture is only as strong as its weakest link (typically third parties connected to their network), making it absolutely vital that they manage third-party identities and access just as they would their own employees.”
Third parties are an increasingly popular target for cybercriminals – they infiltrate the weaker defenses of a partner, contractor or supplier, and then pivot to use that third party’s access to reach their real target. This has been seen time and time again: For instance, Delta and Sears were both compromised last year by attackers who targeted a weakness in a third-party customer-service chatbot platform. And in the case of the infamous Target breach, which impacted 70 million people, the attackers first compromised a HVAC contractor who had a data connection to the giant retailer for electronic billing. More recently, IT systems consulting behemoth Wipro Ltd. earlier this year confirmed that its network was hacked and used for mounting attacks on its customers; and just this week a nationwide chain of veterinary clinics was hit with the Ryuk ransomware after a compromise of external, third-party accounts with network access.
Is MFA enough to protect modern enterprises in the peak era of data breaches? How can you truly secure consumer accounts? Prevent account takeover? Find out: Catch our free, on-demand Threatpost webinar, “Trends in Fortune 1000 Breach Exposure” to hear advice from breach expert Chip Witt of SpyCloud. Click here to register.