Adobe has issued patches for critical vulnerabilities in Flash Player which, if exploited, could lead to arbitrary code execution.
Overall, as part of its September Security Bulletin, Adobe patched three vulnerabilities, including two critical-severity flaws in Flash Player and one “important” glitch in Adobe Application Manager. At this point, Adobe said that it is not aware of any exploits in the wild for any of the patched vulnerabilities.
Adobe’s Flash Player flaws are the most severe, both ranking critical in severity. Those two vulnerabilities include a use-after-free flaw (CVE-2019-8070) and a same origin method execution glitch (CVE-2019-8069), both of which could enable arbitrary code-execution in the context of the current user.
Dustin Childs, manager with Trend Micro’s Zero Day Initiative, told Threatpost that CVE-2019-8069 exists in the navigateToURL function (used to open a URL in a web browser or other application) in the ActionScript programming language for Flash Player. Meanwhile CVE-2019-8070 exists within the handling of objects in the PSDK namespace.
In order to exploit the flaws, “an attacker would need to get someone to view a specially crafted Flash file with an affected version of Flash,” Childs told Threatpost. “This would be visiting a specially crafted webpage or opening a crafted file.”
Once the flaw is exploited, “an attacker could use CVE-2019-8069 to execute their code on a target system at the level of the logged on user. The other bug would need to be paired with a sandbox escape to do the same,” he said.
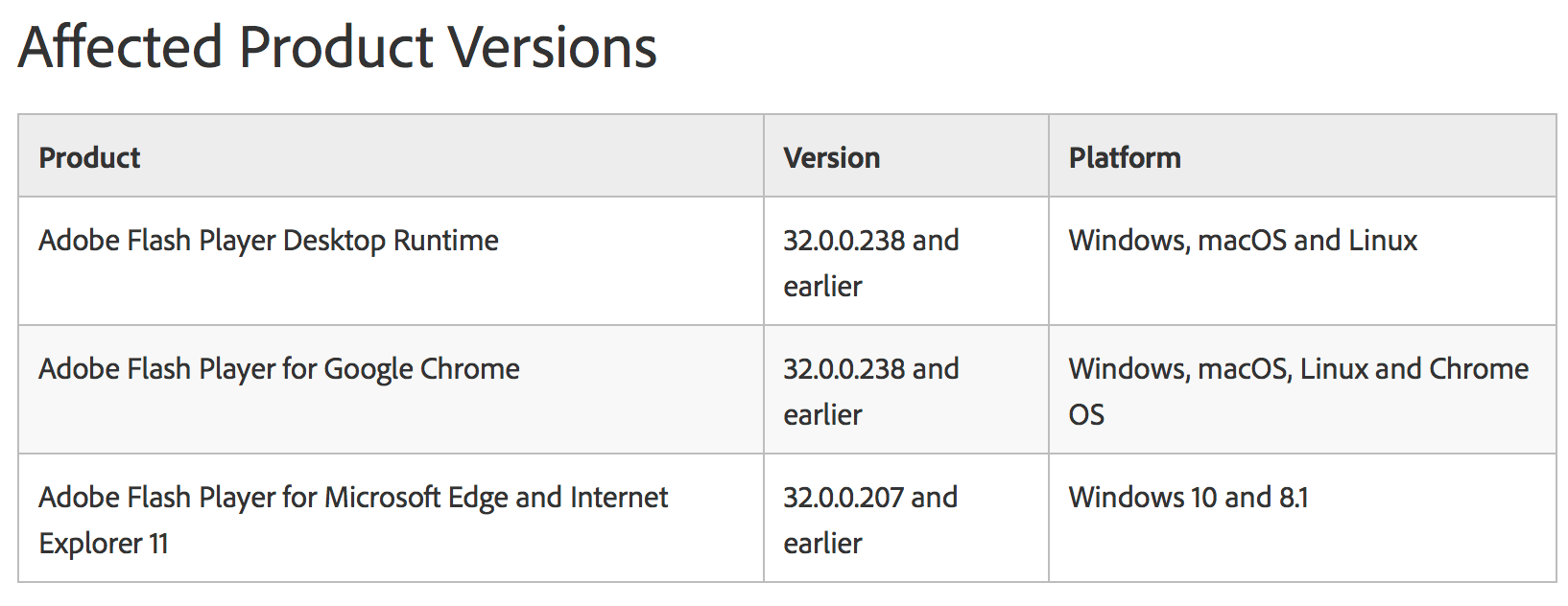
Specifically impacted is Adobe Flash Player Desktop Runtime versions 32.0.0.238 and earlier (for Windows, macOS and Linux); Flash Player for Google Chrome versions 32.0.0.238 and earlier (for Windows, macOS, Linux and Chrome OS) and Flash Player for Microsoft Edge and Internet Explorer 11 versions 32.0.0.238 (for Windows 10 and 8.1).
Users for all impacted platforms are urged to update to version 32.0.0.255. All fixes (with the exception of that for Adobe Flash Player Desktop Runtime) have a priority rating of 2, which means that the “update resolves vulnerabilities in a product that has historically been at elevated risk,” according to Adobe.
Eduardo Braun Prado and one other anonymous researcher working with Trend Micro Zero Day Initiative were credited with discovering the Flash Player flaws. Users can update by visiting the Adobe Flash Player Download Center.
Flash is known to be a favorite target for cyberattacks, particularly for exploit kits, zero-day attacks and phishing schemes. Adobe for its part announced in July 2017 that it will no longer update or distribute Flash Player as of the end of 2020, leading to browsers to turn off Flash Player default support. For instance, Mozilla announced it will kill default support for Adobe Flash in Firefox 69, while Google dumped default Flash support in Chrome 76.
Adobe also issued a patch for a vulnerability in Adobe Application Manager (installer) for Windows, which is an application used to manage the installation of various Adobe products. The flaw (CVE-2019-8076), ranked “important” in severity, is an insecure library loading (DLL hijacking) vulnerability that could enable arbitrary code-execution.
“This vulnerability exclusively impacts the installer used with the Adobe Application Manager,” according to Adobe. “CVE-2019-8076 does not impact the existing Application Manager, and there is no action for customer running earlier versions.”
Specifically impacted is version 10.0 of Adobe Application Manager; users are urged to update to the 2019 release. Security researcher Hamdi Maamri was credited with reporting the issue.
The three flaws patched in Adobe’s September update are far fewer than the number addressed in the company’s August update, which fixed 119 important and critical vulnerabilities. Those flaws included 25 critical bugs across several platforms with the majority of the critical flaws existing in Adobe Photoshop CC.
Interested in more on the internet of things (IoT)? Don’t miss our on-demand Threatpost webinar, IoT: Implementing Security in a 5G World. Join experts from Nokia, iboss and Sectigo as they offer enterprises and other organizations insights about how to approach security for the next wave of IoT deployments. Click here to listen to the recorded webinar.