An Adobe Flash Player zero-day exploit has been spotted in the wild as part of a widespread campaign, researchers said on Wednesday.
Adobe has just issued a patch for the previously unknown critical flaw.
The vulnerability, CVE-2018-15982, is a use-after-free flaw enabling arbitrary code execution in Flash. Researchers with Gigamon Applied Threat Research said the zero-day in Flash was being exploited via a Microsoft Office document dubbed “22.docx.”
Researchers said the document was submitted to VirusTotal from a Ukranian IP address, and purports to be an employment application for a Russian state healthcare clinic, containing seven pages of personal questions that would typically be part of that kind of application.
In reality, “the vulnerability allows for a maliciously crafted Flash object to execute code on a victim’s computer, which enables an attacker to gain command line access to the system,” researchers with Gigamon said in a Wednesday analysis.
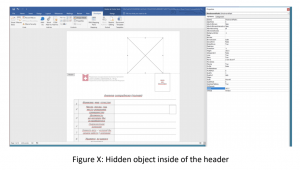
The documents, spread via spear-phishing attacks, contain an embedded Flash Active X control in the header, which renders when the document is open and exploits Flash Player in Office.
After the document opens, a malicious command attempts to extract and execute an accompanying payload.
“Although the death of Flash has been widely reported thanks to industry efforts to deprecate and remove Flash from web browsers, vectors such as Microsoft Office remain able to load and execute Flash content,” researchers said. “As such, exploits against zero-day vulnerabilities that allow for command execution using relatively stock enterprise software are valuable. Flash exploitation can be expected to continue as long as there are valid weaponization vectors that permit reliable execution.”
The payload, dubbed “backup.exe,” is a Windows executable file with metadata that helps it masquerade as an NVIDIA Control Panel, complete with matching icon and manifest details. Upon execution, the payload collects system information, establishes persistence, and communicates with a remote server via HTTP POST.
The payload is protected with VMProtect, a mechanism meant to block efforts at reverse engineering and analysis.
 Interestingly, researchers said they sniffed out a few clues that link the campaign to tools used by Italian offensive security company Hacking Team (which sells surveillance tools and remote access-as-a-service). Hacking Team was breached in 2015, and its internal data – including email, source code to backdoors, and exploits, have since been utilized by threat actors globally, such as APT3, APT18 and Callisto Group.
Interestingly, researchers said they sniffed out a few clues that link the campaign to tools used by Italian offensive security company Hacking Team (which sells surveillance tools and remote access-as-a-service). Hacking Team was breached in 2015, and its internal data – including email, source code to backdoors, and exploits, have since been utilized by threat actors globally, such as APT3, APT18 and Callisto Group.
This most recent exploit utilized a similar method to tools used by Hacking Team in how it used VMProtect to protect follow-on payloads, as well as similar use of digitally signed payloads. These characteristics led researchers to link the attack to tools used by Hacking Team or from the HackingTeam breach.
Regardless, researchers hesitated in attributing the attack. “While attribution is going to be difficult in this scenario, it is really not needed for analysis and detection purposes,” they said. “At best, it could aid the victim’s organization in determining intent and guiding response actions, but in reality, whether it is Hacking Team, a impersonator, or completely unrelated, the fact remains a valid zero-day could have been used to accomplish tactical objectives.”
Gigamon reported the zero-day exploit to Adobe on Nov. 29.
Adobe said in its release Wednesday that impacted products include Adobe Flash Player Desktop Runtime, Adobe Flash Player for Google Chrome; Adobe Flash Player for Microsoft Edge and Internet Explorer 11; all for versions 31.0.0.153 and earlier. Adobe Flash Player Installer versions 31.0.0.108 and earlier is also affected.
“Adobe has released security updates for Adobe Flash Player for Windows, macOS, Linux and Chrome OS,” Adobe said. “These updates address one critical vulnerability in Adobe Flash Player and one important vulnerability in Adobe Flash Player installer. Successful exploitation could lead to Arbitrary Code Execution and privilege escalation in the context of the current user respectively.”
Users of these impacted products can update to version 32.0.0.101, according to Adobe. Users of Adobe Flash Player Installer can update to version 31.0.0.122.
Adobe also patched an “important” Insecure Library Loading (via DLL hijacking) vulnerability, CVE-2018-15983 that could lead to privilege escalation via Adobe Flash.











