Adobe has released patches addressing a wave of critical flaws in its Framemaker and Flash Player products, which, if exploited, could lead to arbitrary code-execution.
Overall, Adobe stomped out flaws tied to 42 CVEs for its regularly scheduled February updates, with 35 of those flaws being critical in severity. That trumps Adobe’s January security update, which addressed nine vulnerabilities overall, including ones in Adobe Illustrator CC and Adobe Experience Manager.
Adobe Framemaker, a document processor designed for writing and editing large or complex documents, including structured documents, took the brunt of this month’s patches with the most (21) critical flaws.
“This update addresses multiple critical vulnerabilities,” according to Adobe in its Tuesday update. “Successful exploitation could lead to arbitrary code-execution in the context of the current user.”
The Framemaker flaws stem from buffer errors, or improper restrictions of operations within the bounds of a memory buffer (CVE-2020-3734); heap overflows, which is a type of buffer overflow that occurs in the heap data area (CVE-2020-3731, CVE-2020-3735); memory-corruption glitches that stem from an unexpected change in the contents of a memory location (CVE-2020-3739, CVE-2020-3740); and out-of-bounds (OOB) write flaws, which are write operations that then produce undefined or unexpected results (CVE-2020-3720, CVE-2020-3721, CVE-2020-3722, CVE-2020-3723, CVE-2020-3724, CVE-2020-3725, CVE-2020-3726, CVE-2020-3727, CVE-2020-3728, CVE-2020-3729, CVE-2020-3730, CVE-2020-3732, CVE-2020-3733, CVE-2020-3736, CVE-2020-3737, CVE-2020-3738).
Adobe Framemaker versions 2019.0.4 and below (for Windows) are affected; a patch exists in version 2019.0.5.
Adobe Flash Player, meanwhile, has a critical type confusion flaw (CVE-2020-3757) that could enable arbitrary code-execution “in the context of the current user.” Affected products include Adobe Flash Player desktop runtime (for Windows, macOS and Linux), Flash Player for Google Chrome (Windows, macOS, Linux and Chrome OS) and Flash Player for Microsoft Edge and IE 11 (for Windows 10 and 8.1).
Users are urged to update to version 32.0.0.330 in a “priority 2” update, which means the update resolves vulnerabilities in a product that has historically been at elevated risk. This priority level makes sense as Flash is known to be a favorite target for cyberattacks, particularly for exploit kits, zero-day attacks and phishing schemes. Adobe for its part announced in July 2017 that it will no longer update or distribute Flash Player as of the end of 2020, leading to browsers to turn off Flash Player default support. For instance, Mozilla announced it will kill default support for Adobe Flash in Firefox 69, while Google dumped default Flash support in Chrome 76.
Adobe Acrobat and Reader, Adobe’s application software and Web services, had critical flaws tied to 12 CVEs, which included a heap overflow flaw enabling arbitrary code execution (CVE-2020-3742), a buffer error glitch allowing arbitrary code execution (CVE-2020-3752 and CVE-2020-3754), use after free errors (which occur when a program continues to use a pointer after it has been freed) enabling arbitrary code execution (CVE-2020-3743, CVE-2020-3745, CVE-2020-3746, CVE-2020-3748, CVE-2020-3749, CVE-2020-3750, CVE-2020-3751) and privilege escalation flaws that could allow for arbitrary file system write (CVE-2020-3762 and CVE-2020-3763).
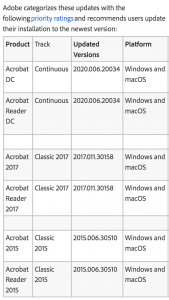 Acrobat and Reader also had three important-rated information disclosure flaws and two moderate-rated memory leak vulnerabilities. Users are urged to update to the patched versions (see chart to left for updated versions).
Acrobat and Reader also had three important-rated information disclosure flaws and two moderate-rated memory leak vulnerabilities. Users are urged to update to the patched versions (see chart to left for updated versions).
Adobe Digital Editions, Adobe’s eBook reader software program, also has a critical and an important flaw in versions 4.5.10 and below. The critical flaw stems from a command-injection glitch (CVE-2020-3760) opening affected systems up to arbitrary code execution. Command-injection attacks are possible when an application passes unsafe user supplied data (such as forms or HTTP headers) to a system shell.
The important flaw is a buffer error (CVE-2020-3759) enabling information disclosure. Users are urged to update to version 4.5.11 for Windows.
Finally, Adobe Experience Manager (AEM), its content management solution for building websites, has an important-level uncontrolled resource consumption vulnerability (CVE-2020-3741) that could result in a denial-of-service condition.
Adobe said that it’s not aware of any exploits in the wild for patched flaws this month.
Learn how Operational Technology and Information Technology systems are merging and changing security playbooks in this free Threatpost Webinar. Join us Wednesday, Feb. 19 at 2 p.m. ET when a panel of OT and IT security experts will discuss how this growing trend is shaping security approaches for IoT and 5G rollouts. This webinar is for security and DevOps engineers, IoT edge developers and security executives.











