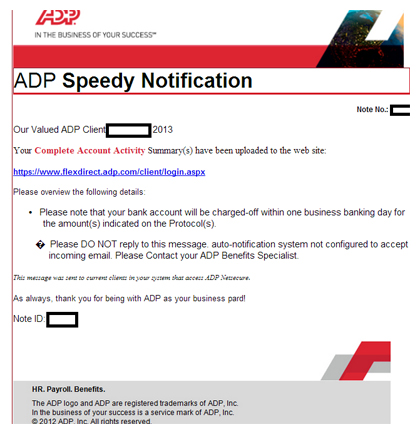
Scammers are spamming out malicious emails purporting to come from payroll processing company ADP, according Dancho Danchev of Webroot.
The emails arrive under the subject line “ADP Immediate Notifications” and contain links to compromised websites hosting the latest iteration of the Blackhole exploit kit. The kit is serving CVE-2013-0422 Java exploit, which Danchev claimed was still active when he published his report. However, Oracle appears to have patched the bug sometime yesterday.
The exploit is dropping the ‘Win32/Cridex.E’ and ‘Win32/Farei’ Trojans, which are detected by 12 and eight out of 46 antivirus scanners respectively. After exploitation, the malware is phoning home to command and control servers at the following IP addresses: 173.201.177.77, 132.248.49.112, 95.142.167.193, and 81.93.250.157.
The campaign makes use of a healthy list of suspicious looking URLs that you can check out along with Danchev’s write-up. It’s fairly commonplace for social engineers to mimic ADP in their phishing campaigns because of the vastness of the company’s payroll operation.