A newly-discovered spam campaign is spreading the Adwind 3.0 remote-access tool (RAT) – and using a fresh take on the Dynamic Data Exchange (DDE) code-injection technique for anti-virus evasion.
The spam campaign features two types of droppers that leverage a new variant to the already-known DDE code-injection attack on Microsoft Excel – enabling them to bypass AV software.
DDE is a legitimate method for transferring data between applications – so for Excel, the process could update contents of a spreadsheet cell with information from an external application or file with a specific extension. Thus, one can craft a weaponized file containing a DDE formula, which, when opened, will prompt Excel to try to execute the external application.
“The DDE variant used by the droppers in this campaign is a good example on how signature-based anti-virus can be tricked,” Cisco Talos researchers said in a Monday blog post. “It is also a warning sign regarding the file extension-scanning configurations. This kind of injection is known for years, however this actor found a way to modify it in order to have an extremely low detection ratio.”
The spam emails in the campaign feature an attached malicious .CSV or .XLT file, which are both opened by default by Microsoft Excel and contain one of two types of droppers, both of which use the DDE code injection.
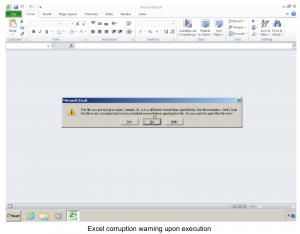
The start of the dropper file has no header that can be checked, confusing AV software so that it believes the file is corrupt, as opposed to being malicious. Excel then gives the user three warnings that the file may be corrupt; should the user choose to proceed, the dropper will be executed.
The payload is a well-known multiplatform RAT, Adwind v3.0, with a wide range of capabilities. Researchers said it’s a “field-proven” RAT that ensured to work as designed and will have a low detection ratio due to the packer used.
The RAT “is used by several malicious groups,” researchers said. “It gives its operators the ability to execute any kind of commands on its victims: log keystrokes, take screenshots, take pictures or transfer files. In the past, it has been seen used to run cryptomining campaigns or to target the aviation industry.”
From there, the files connect to the RAT’s command-and-control server and download additional payloads, as well as steal and transfer data.
The campaign has impacted Linux, Windows and Mac OSX systems, mainly located in Turkey (75 percent of the request were made from there). Additional groups of victims were found in Germany. The campaign was discovered by researchers at Cisco Talos and ReversingLabs on Sept. 10; the researchers found that the campaign started Aug. 26 and peaked on Aug. 28.
Cisco Talos researchers said that sandboxing and behavior-based solutions should be able to detect and stop the spam campaign: “Although both the generic method and the payload are known, this campaign shows how some variance into well-known artifacts can trick anti-virus.”