More than half of global airlines do not have DMARC policies in place, opening their customers up to email fraud attacks, a new report found.
DMARC (Domain-based Message Authentication, Reporting & Conformance) is considered the industry standard for email authentication to prevent attackers from sending mails with counterfeit addresses. It does so by authenticating the sender’s identity before allowing the message to reach its intended designation – and verifying that the purported domain of the sender has not been impersonated.
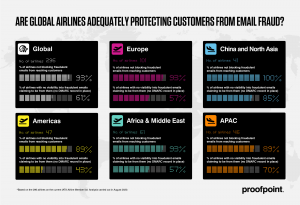
In a study of 296 member airlines of the International Air Transport Association (IATA), researchers with Proofpoint found that 61 percent have no published DMARC record in place, meaning they have no visibility into unauthorized use of their domains – and therefore into fraudulent emails claiming to be from them.
“Overall, major global carriers are failing to implement adequate email protection – leaving themselves open to phishing, impersonation attacks and other unauthorized use of corporate domains. This is despite email remaining the number one threat vector for cybercriminals,” according to Adenike Cosgrove with Proofpoint in a Tuesday report.
Even out of those who do have DMARC records in place, most are not using the strictest DMARC settings, according to Proofpoint. They said, up to 93 percent of global airlines do not have the “recommended” level of DMARC protection policies in place, known as the “Reject” policy.
There are three levels of DMARC policies. In the strictest “Reject” policy, companies can blocks all fraudulent emails from reaching their intended target. As part of the second level, the “Quarantine” policy, companies tell email receivers to put the potentially spoofed emails into spam or junk folders. With the third level, “Monitor,” companies do not tell the email receiver to do anything with emails sent, but they instead analyze who is sending emails on their behalf.
“This means that only 7 percent are proactively blocking fraudulent emails from reaching their customers’ inboxes,” Cosgrove said.
IATA is a trade association of the world’s airlines across 120 countries and represents 82 percent of total air traffic – including airlines like Delta Airlines, JetBlue and British Airways. IATA supports airline activity and helps formulate industry policy and standards.
Researchers did not pinpoint specific airlines in the report. However, Threatpost independently confirmed (using DMARC deployment lookup tools) that several top airlines have varying levels of DMARC policies implemented. For instance, Delta Airlines uses the “Monitor” policy; while British Airways, Southwest and JetBlue use the “Reject” policy.
DMARC adoption for airlines levels differ from region to region. Researchers said that out of the regions classified by IATA, the China and North Asia region has the lowest level of DMARC adoption, with 85 percent having no published policy at all.
Out of the 47 airlines from the Americas region, meanwhile, 89 percent are not blocking fraudulent emails from reaching customers with the highest level of DMARC protections, while 42 percent have no DMARC record in place.
The study of airline’s DMARC policies come as adoption of the email security protocol is actually ticking upwards, with the number of domains deploying DMARC records surpassing 1 million in the last two years — a 2.5 times greater total than in 2018.
However, some industries – including higher education – continue to lag behind in adoption. Worse, with COVID-19 causing a flurry of cancelled flights and changed schedules, the travel sector has “offered new grounds for the targeting of travellers globally” – and that extends to email communications, said Cosgrove.
“It is critically important that the communication methods used by airlines and every other industry is secure. We recommend implementing robust email defences and inbound threat blocking capabilities (including deploying DMARC email authentication protocols),” said Cosgrove.
Airlines have faced criticism over the years from the security industry. In 2019, security researchers discovered that multiple airline e-ticketing systems do not encrypt check-in links. The security faux pas could allow bad actors on the same network as the victim to view – and in some cases even change – their flight booking details or boarding passes. Also in 2019, a security bug discovered in British Airways’ e-ticketing system had the potential to expose passengers’ data, including their flight booking details and personal information. As recently as 2020, both European budget airline EasyJet and the San Francisco International Airport (SFO) were hacked.
It’s the age of remote working, and businesses are facing new and bigger cyber-risks – whether it’s collaboration platforms in the crosshairs, evolving insider threats or issues with locking down a much broader footprint. Find out how to address these new cybersecurity realities with our complimentary Threatpost eBook, 2020 in Security: Four Stories from the New Threat Landscape, presented in conjunction with Forcepoint. We redefine “secure” in a work-from-home world and offer compelling real-world best practices. Click here to download our eBook now.