Researchers on Tuesday said they found several critical security vulnerabilities in various AMD chips, allegedly opening them up to attackers who want to steal sensitive data and install malware on AMD servers, workstations and laptops.
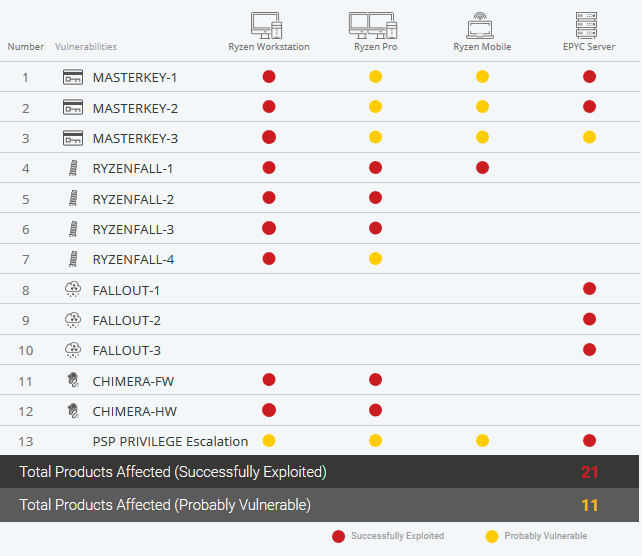
Israel-based CTS-Labs said that it has discovered 13 critical vulnerabilities and exploitable backdoors that impact AMD’s EPYC server, Ryzen workstation, Ryzen Pro and Ryzen mobile lineups. CTS-Labs said it has shared this information with AMD, Microsoft and “a small number of companies that could produce patches and mitigations” – but said there are no known fixes at this time.
AMD did not respond to inquiries from Threatpost about any available fixes for the vulnerabilities. The company said in a statement:
“We have just received a report from a company called CTS Labs claiming there are potential security vulnerabilities related to certain of our processors. We are actively investigating and analyzing its findings. This company was previously unknown to AMD and we find it unusual for a security firm to publish its research to the press without providing a reasonable amount of time for the company to investigate and address its findings. At AMD, security is a top priority and we are continually working to ensure the safety of our users as potential new risks arise.”
Meanwhile, a Microsoft spokesperson told Threatpost “We were recently made aware of this report and are reviewing the information.”
Dan Guido, security researcher and CEO of Trail of Bits, independently verified the reports of the vulnerabilities and exploit code on Twitter.
Regardless of the hype around the release, the bugs are real, accurately described in their technical report (which is not public afaik), and their exploit code works.
— Dan Guido (@dguido) March 13, 2018
According to researchers, the flaws stem from the design of AMD’s “security gatekeeper” Secure Processor, which is the area of the processor where devices store sensitive data including passwords and encryption keys; and the design of AMD’s Ryzen chipset, which links the processor with hardware devices such as Wi-Fi and network cards.
“This integral part of most of AMD’s products, including workstations and servers, is currently being shipped with multiple security vulnerabilities that could allow malicious actors to permanently install malicious code inside the Secure Processor itself,” wrote CTS-Labs in a whitepaper outlining the flaws (PDF).
Researchers maintain there are four primary types vulnerability variants that can leveraged to attack the AMD processors.
One particularly nasty vulnerability, said researchers, is called Chimera which was discovered in Ryzen workstation and Ryzen Pro. CTS-Labs maintains, Chimera includes two sets of manufacturer backdoor flaws – one implemented in firmware, and the other in hardware – that allow malicious code to be injected into the Ryzen chipsets.
Through Chimera, “an attacker could leverage the chipset’s middleman position to launch sophisticated attacks,” according to CTS-Labs, and could install malware to leverage the Direct Memory Access engine to attack the operating system.
Another vulnerability impacts AMD’s Ryzen workstation, Pro and mobile lineups is Ryzenfall, they said. Ryzenfall allows malicious code to take complete control over the AMD Secure Processor and leverage the technology’s privileges to read and write protected memory areas (such as SMRAM and the Windows Credential Guard isolated memory).
“Attackers could use RYZENFALL in conjunction with MASTERKEY to install persistent malware on the Secure Processor, exposing customers to the risk of covert and long-term industrial espionage,” said CTS-Labs.
Fallout is the third vulnerability impacting AMD’s EPYC server chips, researchers said. Fallout also allow attackers to read from and write to protected memory areas including SMRAM and Windows Credential Guard isolated memory (VTL-1).
“An attacker could leverage these vulnerabilities to bypass BIOS flashing protections that are implemented in SMM,” said CTS-Labs.
Finally, the Masterkey flaw breaks down into three separate vulnerabilities found in AMD’s Secure Processor firmware, allowing hackers to infiltrate the Secure Processor in EPYC server, Ryzen workstation, Ryzen Pro and Ryzen mobile chips.
These variants “allows tampering with AMD’s firmware-based security features such as Secure Encrypted Virtualization (SEV) and Firmware Trusted Platform Module (fTPM),” according to CTS-Labs, and could lead to physical damage and bricking of hardware, particularly in hardware-based “ransomware” scenarios.”
The vulnerabilities enable attackers to bypass security measures like Microsoft’s latest Credential Guard technology or EPYC Secure Processor’s Secure Encrypted Virtualization security feature.
CTS-Labs said in its report that it didn’t know how long before a fix becomes available – but according to experts, firmware vulnerabilities take several months to fix, and the Chimera hardware vulnerabilities cannot be fixed. The company also said it didn’t know if the vulnerabilities are currently being exploited in the wild – but it is “concerned” about Chimera.
The vulnerability announcements come as another hit for the chip market after Spectre and Meltdown flaws were disclosed by Google Project Zero in early January.
These defects, which account for three variants of a side-channel analysis security issue in server and desktop processors, could potentially allow hackers to access users’ protected data through the design in chips. Meltdown breaks down the mechanism keeping applications from accessing arbitrary system memory, while Spectre tricks other applications into accessing arbitrary locations in their memory.
“In our opinion, the basic nature of some of these vulnerabilities amounts to complete disregard of fundamental security principles,” said CTS-Labs in the whitepaper. “This raises questions regarding security practices, auditing, and quality controls at AMD.”