An ongoing analysis of the Duqu malware by researchers at Kaspersky Lab finds many links between the two pieces of malicious code and casts doubt on the conventional wisdom about Stuxnet’s origins.
An analysis of software drivers used by both Stuxnet and the later Duqu malware has found that the both Stuxnet and Duqu are built on an identical platform, which Kaspersky has dubbed the “tilded” platform, for its use of the tilde (~) character in file names. Moreover, the researchers suggest that the origins of both pieces of malware date to late 2007 or early 2008, and that other pieces of malware may well have been built on the same platform, but were never released in large numbers or detected by mainstream security firms.
Duqu first came to light in September and was immediately dubbed a successor to the Stuxnet worm, which is credited with disabling uranium enrichment facilities within Iran. Though Duqu was not written to compromise industrial control systems, as Stuxnet was, it is widely believed to be a sophisitcated piece of malware targeted at a small population of potential victims.
Writing on the Securelist blog, Kaspersky Labs researcher Alex Gos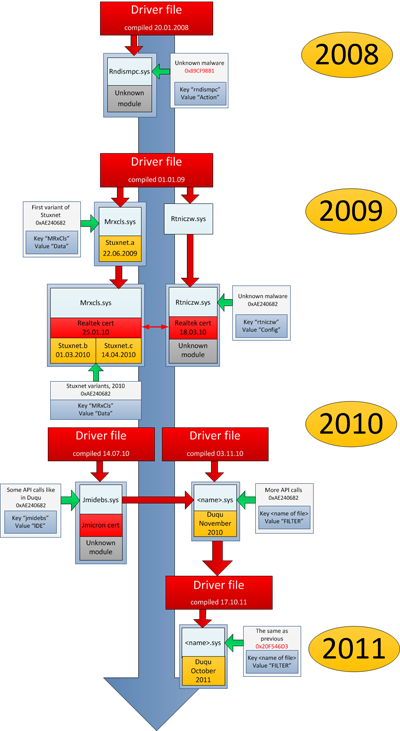 tev traced the development of two key drivers and variants that are used in both Stuxnet and Duqu, as well as two previously unknown drivers that were almost identical to the Stuxnet/Duqu drivers. Gostev suggests that the malware authors behind Stuxnet and Duqu were the same, and that – rather than working tirelessly on one malware creation, they worked simultaneously on multiple malware variants, tinkering and modifying existing code for use in new pieces of malware (and for different purposes) from 2007 through this year.
tev traced the development of two key drivers and variants that are used in both Stuxnet and Duqu, as well as two previously unknown drivers that were almost identical to the Stuxnet/Duqu drivers. Gostev suggests that the malware authors behind Stuxnet and Duqu were the same, and that – rather than working tirelessly on one malware creation, they worked simultaneously on multiple malware variants, tinkering and modifying existing code for use in new pieces of malware (and for different purposes) from 2007 through this year.
Describing the process that generated the drivers used by both Stuxnet and Duqu, Gostev wrote: “A few times a year the authors compile a new version of a driver file, creating a reference file. The primary purpose of this file is to load and execute a main module, which is created separately. It could be Stuxnet, or Duqu or something else…they tweak ready-made files and don’t create a new one from scratch. This means they can make as many different driver files as they like, each having exactly the same functionality and creation date. Depending on the aim of the attack and the Trojan’s victim, several driver files can then be signed with legitimate digital certificates whose origins remain unknown.”
Gostev postulates that other malware was built on the “tilded” Stuxnet platform in the period between 2007 and 2011. “Stuxnet and Duqu are two of them – there could have been others, which for now remain unknown. The platform continues to develop, which can only mean one thing – we’re likely to see more modifications in the future,” Gostev writes.
Read more of his analysis on the Securelist blog.









