 The exploit that is being used in the attacks against the latest zero-day vulnerability in Adobe Flash is a modified version of a harmless SWF file that is only one byte different from the original file. Researchers have seen the exploit being used in active attacks against the vulnerability in Flash, which Adobe is set to patch tomorrow.
The exploit that is being used in the attacks against the latest zero-day vulnerability in Adobe Flash is a modified version of a harmless SWF file that is only one byte different from the original file. Researchers have seen the exploit being used in active attacks against the vulnerability in Flash, which Adobe is set to patch tomorrow.
The malicious Flash file uses a bug that experts say is a boundary check error in pre-allocated memory, according to an analysis of the exploit by researchers at Websense. After analyzing the exploit, the researchers found that the bug is exploitable using heap spraying.
“So after a few calls to the ‘newfunction’ opcode, the EDI pointer above
exceeds the controlled memory and hits some pre-allocated memory with
heap-sprayed code, and will pass the execution flow to the sprayed
shellcode,” the researchers said. “Heap-spray makes a lot of vulnerabilities exploitable
that might previously have been thought useless. Code auditors should be
more careful in locating this kind of vulnerability.”
The vulnerability in Adobe Flash was disclosed late last week, and Adobe said at the time of the disclosure that it was aware of active attacks against the flaw. The vulnerability also affects Adobe Reader and Acrobat.
Flash is among the more widely deployed pieces of software worldwide on the Web, and it has become a favorite attack vector for malicious hackers, who have been using it of late as a way around the memory protections built into Windows and some browsers. The fact that researchers have found and analyzed an exploit is good news, but it’s likely that this isn’t the only one being used right now.
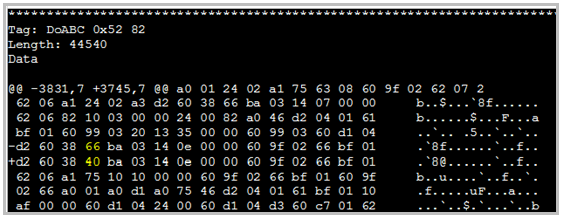
“Basically, this crash or exploit stems from either the SWF file, or a
file embedded inside a PDF that contains the DoABC Tag Record with
a ‘newfunction’ opcode that has an invalid argument,” Websense said in its analysis. “We thought
this bug might be an use-after-free, or is at least in the realm of
free-related bug classes. But when we ran through static and dynamic
analysis with the malicious file, we came to the conclusion that this is
a boundary check error in using pre-allocated memory.”









