 SQL injection has become perhaps the most widely used technique for compromising Web applications, thanks to both its relative simplicity and high success rate. It’s not often that outsiders get a look at the way these attacks work, but a well-known researcher is providing just that.
SQL injection has become perhaps the most widely used technique for compromising Web applications, thanks to both its relative simplicity and high success rate. It’s not often that outsiders get a look at the way these attacks work, but a well-known researcher is providing just that.
Rafal Los, a senior Web security specialist at HP, has put together a description of just how simple these attacks can be, including a look at the psychology behind their success. Talking to a group of executives about the problem of Web application security, Los found that many of them were skeptical about the extent of vulnerabilities in their code. So he decided to demonstrate the problem right in front of them.
“It’s often the case that the best teacher is experience – and I wish
for nothing more than my doubting Thomases to ask me to show them these
issues on their sites … without even asking this crowd
obliged. A fellow in the back of the room just yelled ‘Well, if these
issues are so prevalent, let’s see if they exist on one of our sites’.
I left auto-pilot and went into cautious attack mode,” Los wrote in a blog post describing the attack.
After a quick glance at the volunteer’s site, Los noticed an error that showed evidence that someone else had attacked the site. So he then appended a single tick mark to the end of the URL, which caused a SQL statement to fail and generate an error message explaining exactly what the problem was. And that was more than enough information for Los. He then added ” ‘ OR ‘1’ = ‘1 ” to the end of the original URL.
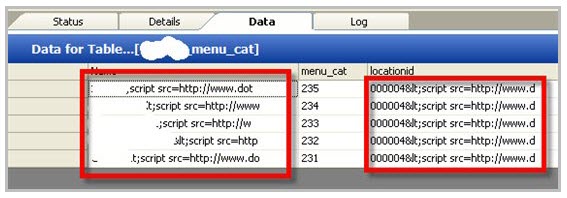
“First, there was an obvious error in the database, to me it meant I
wasn’t the first to hack at it and someone previous to me had messed
with it and broken it. Hopefully they broke it BEFORE they stole all
the information out of it. Next, the single-tick generating an error,
I hope that’s self-explanatory … I simply caused a SQL statement to
go awry and fail, and SQL politely and graciously told me all about it,” Los wrote. “Lastly, the ‘OR’1’=’1 statement append worked because it didn’t
cause an error… why? It’s because 1=1 evaluates to true and the
database won’t throw an error if the result is TRUE!”
With the permission of the site’s owner, Los exploited the vulnerability and was able to dump the entire contents of the back end database to his laptop. Looking through the tables, he found that the database had in fact been compromised previously and that the attacker had injected some strings that would serve malware from the site. The site was now trying to serve the Zeus Trojan to visitors.









