Researchers have discovered a new Android spyware, dubbed ActionSpy, targeting victims across Tibet, Turkey and Taiwan. The spyware is distributed either via watering-hole websites or fake websites.
Researchers believe ActionSpy is being used in ongoing campaigns to target Uyghur victims. The Uyghurs, a Turkic minority ethnic group affiliated with Central and East Asia, have previously been targeted in spyware attacks. Though they first discovered the spyware in April 2020, researchers believe ActionSpy has existed for at least three years based on its certificate sign time.
“ActionSpy, which may have been around since 2017, is an Android spyware that allows the attacker to collect information from the compromised devices,” said researchers with Trend Micro in a Thursday analysis. “It also has a module designed for spying on instant messages… and collecting chat logs from four different instant messaging applications.”
Researchers discovered ActionSpy being spread via several pages in April 2020. How these pages were distributed in the wild – whether via phishing emails or otherwise – is also unclear, researchers said.
Some of these websites were actually fake. For instance, one page replicated news pages from the World Uyghur Congress website. Others were legitimate websites that had been compromised.
Researchers identified a news website and political party website in Turkey that were compromised and used in the attack, for instance, as well as on a university website and travel agency site based in Taiwan that were also compromised and used as watering-hole websites.
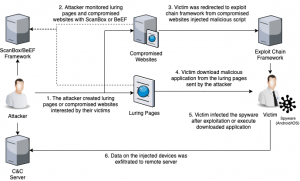
 In these cases, the attackers injected the websites with a script to load the cross-site scripting framework BeEF. BeEF (short for The Browser Exploitation Framework) is a penetration testing tool that focuses on the web browser.
In these cases, the attackers injected the websites with a script to load the cross-site scripting framework BeEF. BeEF (short for The Browser Exploitation Framework) is a penetration testing tool that focuses on the web browser.
Researchers say, they suspect the attacker used this framework to deliver their malicious script when a targeted victim browsed the malicious websites.
In late April 2020, researchers discovered another type of website that appeared to be copied from a third-party web store and purported to invite users to download an Uyghur video app that is popular with Tibetan Android users, called Ekran. The page was injected with two scripts to load the BeEF framework, as well as the ScanBox framework. ScanBox, a framework in the form of a JavaScript file, can collect information about the visitor’s system without infecting the system.
“The download link was modified to an archive file that contains an Android application,” said researchers. “Analysis then revealed that the application is an undocumented Android spyware we named ActionSpy.”
ActionSpy
Once downloaded, ActionSpy will connect to its Command and Control (Cs) server, which is encrypted by DES. Researchers said the decryption key is generated in native code – making static analysis of ActionSpy difficult. Then, every 30 seconds, the spyware would collect basic device information (including IMEI, phone number, manufacturer, battery status, etc.) which it sends to the C2 server.
 ActionSpy supports an array of modules, including ones allowing it to collect device location, contact info, call logs and SMS messages. The spyware also has capabilities to make a device connect or disconnect to Wi-Fi, take photos with the camera and screenshots of the device and get chat logs from messaging apps like WhatsApp, China messaging services like QQ and WeChat, and Japanese messaging tool Viber.
ActionSpy supports an array of modules, including ones allowing it to collect device location, contact info, call logs and SMS messages. The spyware also has capabilities to make a device connect or disconnect to Wi-Fi, take photos with the camera and screenshots of the device and get chat logs from messaging apps like WhatsApp, China messaging services like QQ and WeChat, and Japanese messaging tool Viber.
ActionSpy also prompts users to turn on the Android Accessibility service, using a prompt that purports to be a memory garbage cleaning service. The Accessibility Service, which has previously been leveraged by cybercriminals in Android attacks, assists users with disabilities. They run in the background and receive callbacks by the system when “AccessibilityEvents” run.
Once the user enables the Accessibility service, ActionSpy will monitor such “AccessibilityEvents” on the device, giving it the ability to parse the victims’ current activity and extract information like nicknames, chat contents, and chat time.
Earth Empusa
Researchers believe that the websites may have been created by a threat group called Earth Empusa. This is based on the fact that one of the malicious scripts injected on the page was hosted on a domain belonging to the group.
Earth Empusa, also known as POISON CARP/Evil Eye, is a threat group that’s previously been associated with cyberattacks targeting senior members of Tibetan groups. Researchers said that they found some news web pages, which appear to have been copied from Uyghur-related news sites, hosted on Earth Empusa’s server in March 2020.
Researchers warn that Earth Empusa is still very active in the wild, and that they have observed the BeEf framework injections on multiple Uyghur-related sites since the start of 2020.
“These developments have led us to believe that Earth Empusa is widening the scope of their targets,” researchers warn.











