It’s been 13 months since Google began releasing Android security bulletins and software patches on a scheduled, monthly basis. So far, the benefits of the new strategy to shore up Android’s defenses are mixed at best. Compared to Apple’s patching track record, Google’s is significantly lacking.
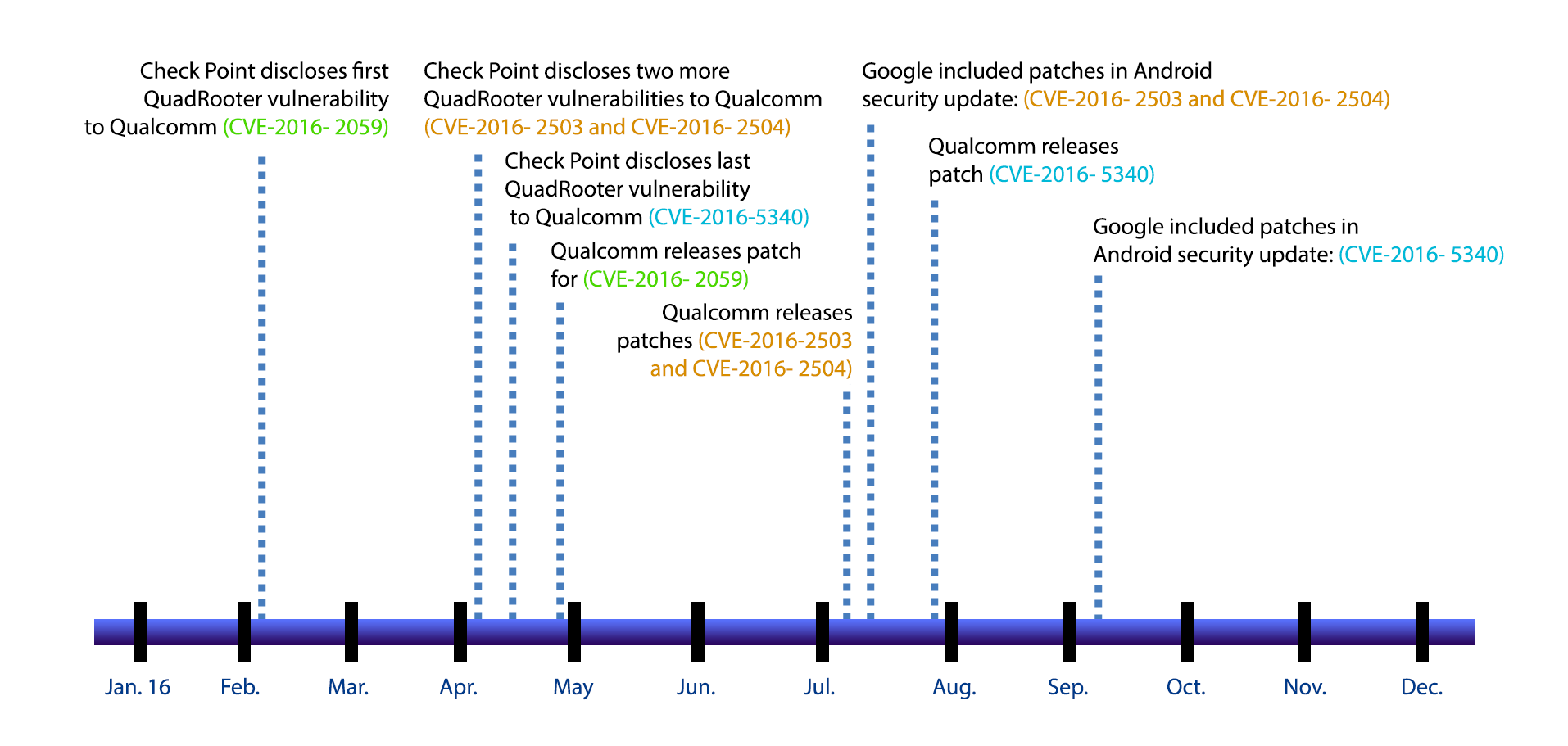
Security experts say look no further than to this past August and Google’s patching of the high-profile QuadRooter vulnerability that took 96 days for Google to go from vulnerability notification by Qualcomm to the release of the final patch for the critical flaws on Sept. 6. By comparison, it took Apple just 10 days from the time researchers tipped off the company to the notorious Trident vulnerabilities, which were publicly attacked unlike QuadRooter, to Apple releasing its iOS patch.
That stark difference in patch times, below, illustrates to many mobile security experts that despite security gains within the Android platform – from MediaServer hardening and file-level encryption – Google’s security efforts are still stymied by the nagging problem of fragmentation. For example, only a fraction of phones vulnerable to the QuadRooter vulnerability have received Google’s patches.
Kyle Lady, research and development engineer at Duo Labs, says issues tied to fragmentation are hurting the Android ecosystem on two fronts. One front is Google’s efforts to work with a myriad partners on identifying risks and prepping patches for Google’s monthly security updates. The second is making sure those patches are deployed by Android handset makers and wireless carriers to consumers in a timely manner.
Since Google released its last patch to fix the QuadRooter vulnerability, only 15 percent of Android phones capable of receiving the security update had done so, according to the most recent data available from Duo Labs collected Oct. 5.
Government Regulators Watching
Keeping handsets safe is crucial as the mobile industry faces growing scrutiny by government regulators. In May, both the Federal Communications Commission and the Federal Trade Commission issued orders to eight mobile phone companies – including Apple and Google – to answer questions about how they issue security updates to address vulnerabilities in smartphones. While the agencies say they have concluded their studies, both are mum on what they found – promising a full report in the months to come.
“To be balanced, there are lots of different Android devices and most Android devices still aren’t getting updates,” said Nick Kralevich, Android platform security team leader with Google, speaking at the Black Hat security conference in August. “We will continue to work with our OEM partners and carrier partners to make sure our updates are reaching an increasing number of devices at a faster pace,” he said.
Kralevich boasted that the majority of current Android flagship devices made by the top four smartphone makers have patches that are within a 30 day patch window. “A great percentage are within a 60 day (patch window). All of them are within a 90 day patch window,” according to Kralevich.
But security firms counter the total number of Android phones that have up-to-date patches is far less. Michael Shaulov, head of mobility product management, at Check Point Software Technologies, said there are a certain number of phones that can’t get patched because the OS used is no longer supported by Google; such as Android 4.1 Jelly Bean and earlier.
“Dealing with Android vulnerabilities is particularly challenging with the myriad of models, diverse sets of third-party components and unique software configurations,” Shaulov said. He estimates there are millions legacy Android phones used in secondary markets around the world that will never be updated with a QuadRooter or any other security patch.
Closer to home, Android fragmentation is a huge hurdle for wireless carriers and device makers. Developing and testing software security patches for even a handful of Android models can cost hundreds of thousands of dollars, he said.
According to Verizon Communications it limits development of security patches to only those models it actively sells. Albert Aydin, a Verizon spokesman, said that Verizon stops updating phone models 18 months after it stops selling them.
“There is no set timeframe for pushing out updates. It’s on a case-by-case basis,” Aydin said. “We move as fast as we can. We have no timeline for updating phones.”
Carriers Create Challenges in Maintaining Patching Levels
Building and pushing out security patches can sometimes take months, say experts. Each phone manufacturer first has to build updates for each specific model smartphone. Next, each hardware build has to go through carrier certification and a barrage of quality assurance tests that can take weeks to months. Then it’s up to the wireless carrier to push out the update to millions of users, said Andrew Blaich, a security researcher at the mobile security company Lookout.
“Given the high costs that goes into developing each update, it’s hard to get OEMs and wireless carriers to spend money updating phones they no longer sell,” Blaich said.
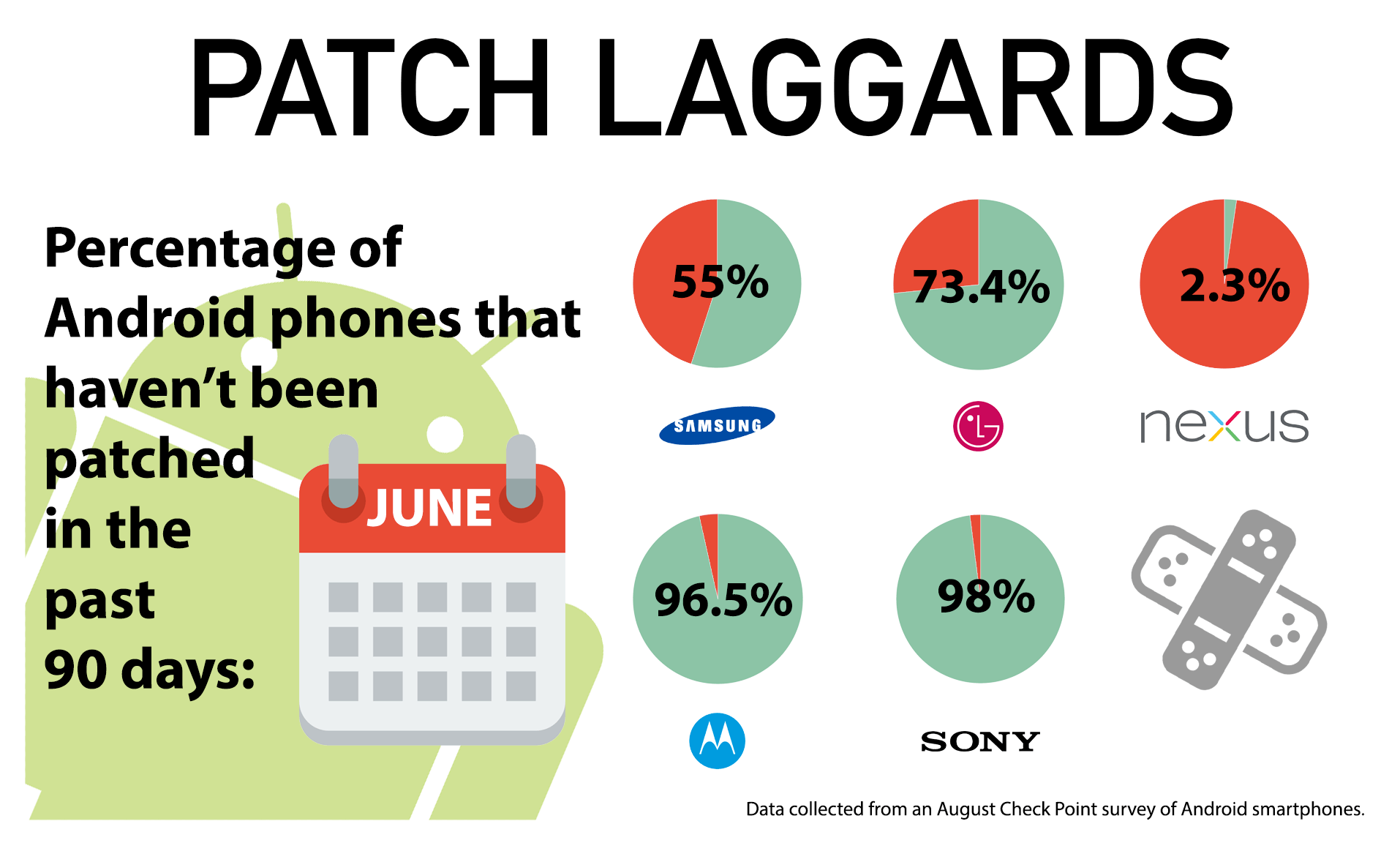
In August, when Check Point looked at the patching numbers it found more than 55 percent of Samsung devices were running patches older than June. With LG Electronics phones, 73.4 percent had patches older than June. Motorola came in with 96.5 percent having patches older than three months and Sony had 98 percent. Google’s Nexus brand phones were the exception, with only 2.3 percent of phones with patches older than June.
For Google’s part, it says it will provide support for its Nexus brand phones for at least three years from device availability, or 18 months after the last device is sold by Google. It says, including its own Nexus family of Android gear, there are 60,000 different Android device models.
Google declined to comment for this story. But reports by Bloomberg suggest that Google is frustrated by device makers dragging their feet to update their phones. As retaliation, the report said, Google was prepared to “shame some phone makers into better behavior.”
That shaming, according to the report, simply includes more monthly visibly when it comes to ranking top Google partners based on how up-to-date the security software is on their handsets.
When Threatpost reached out to Motorola to better understand the challenges in updating its handsets it declined a request for an interview. In a statement from David Yen, global software engineering lead, at Lenovo Mobile Business Group, he said:
“We understand that keeping phones up-to-date with security patches is important to our customers and strive to push security patches as quickly as we can. We work with our carrier partners, software providers and other partners to extensively test patches before they are delivered, which can be in various forms, such as pure Security Maintenance Releases, scheduled Maintenance Releases and OS Upgrades.”
In August, Motorola said it couldn’t promise its flagship Moto Z and Moto G4 would receive monthly Android security patches. Instead, Motorola said updates would be quarterly. Samsung and LG said they have committed to monthly security updates for their handsets. HTC did not respond to a request for comment on this story.
Nougat a Trick or Treat?
Lookout’s Blaich said that Google is fighting the patching battle on two fronts. On one hand Google is working hard with device OEMs and wireless carriers. On the other hand, Google is trying to make the Android OS easier to update directly – independent of OEMs and wireless carriers.
Blaich said starting with the Aug. 22 release of Android 7.0 (Nougat) Google is attempting to become more self-reliant by creating independent apps that might have otherwise been Android OS baked-in features. For example, Google recently introduced its Allo and Duo (formerly Hangouts) messaging features as standalone apps. Now, Google can push out software updates if needed to those apps, independent of device makers and carriers.
Another problem many security experts say Google and Apple face is that few consumers actually install patches and updates when they become available. According to Check Point, a great deal of Android and Apple phones are eligible for security updates and users just don’t update them.
“Unfortunately patches are not being installed,” Shaulov said. “This is becoming a significant problem. We have fixed the pipe in one place, but still we have leakage in other part of the pipe.” For that reason, it’s incumbent on mobile phone industry to raise consumer awareness on the importance of keeping their phones up-to-date, Shaulov said.
“Nobody wins when it comes to poor mobile security – not the user, Google, Apple, OEM or wireless carrier,” Shaulov said.