Researchers are warning users to delete a popular Android keyboard app that, once downloaded, makes unauthorized purchases of premium digital content. Google told Threatpost it has removed the app from its Google Play marketplace – but researchers say it was downloaded on at least 40 million phones worldwide and thus remains a threat.
The app, Ai.type, allows users to personalize their keyboard with various fonts and emojis and was developed by Israeli firm Ai.type Ltd., according to researchers with mobile tech company Upstream. Ai.type Ltd. did not respond to a request for comment from Threatpost.
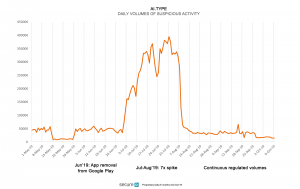
Once downloaded, researchers said the app makes “suspicious” requests to trigger the purchase of premium digital services in the background – so users are unaware of the activity. Upstream detected 14 million such transaction requests from 110,000 unique devices that downloaded the Ai.type keyboard. If these transactions had not been detected and blocked, the app could have cost victims as much as $18 million, researchers said.
“The app has been delivering millions of invisible ads and fake clicks, while delivering genuine user data about real views, clicks and purchases to ad networks,” said Upstream researchers on Thursday. “Ai.type carries out some of its activity hiding under other identities, including disguising itself to spoof popular apps such as Soundcloud. The app’s tricks have also included a spike in suspicious activity once removed from the Google Play store.”
In an email to Threatpost, a Google spokesperson confirmed that the app was removed from Google Play in June 2019 – but it is still available from other Android marketplaces, researchers warned. In addition, the app is also available on Apple’s App Store marketplace. An Apple spokesperson told Threatpost that they are currently looking into that app.
Shortly after the removal from Google Play, in fact, suspicious activity spiked exponentially beginning in July 2019 for a two-month period. The suspicious activity has been recorded across 13 countries, but was particularly high in Egypt and Brazil.
Researchers said that in testing, they reviewed the app’s impact on a Samsung SM-J500F and a Samsung GT-19500.
The Ai.type versions installed on each device contained SDK frameworks with obfuscated hard-coded links back to advertising trackers, used by mobile advertising networks to display ads. In addition, the app downloads additional JavaScript code that can be used to perform automated clicks.
The app then disguises itself as popular apps – such as Soundcloud – and subscribes users to premium services, which depletes mobile data and adds charges, as well as reduces the battery life and overall performance of the device.
In terms of how the victims’ payment information is used for the premium services, “These are digital services charged via direct carrier billing, i.e. using the mobile airtime of the users,” Upstream researchers told Threatpost. “No need to access any bank account number.”
The one red flag that might tip users off that something is amiss is subscription verification texts; these may be sent from premium digital services to victim devices to confirm their participation.
In addition to subscriptions, the app also requires a broad number of permissions from users that Upstream researchers classify as “dangerous” – including permissions to access and view text messages, photos, videos, contact data and on-device storage.
The official app stores both for iOS and Android continue to be plagued by apps that commit ad fraud. Earlier in October, for instance, researchers uncovered 17 apps on Apple’s official App Store that carried out ad-related malicious activity in the background, including continually opening web pages and clicking links without any user interaction.
And, earlier in 2019, Google Play removed least 85 fake apps harboring adware, disguised as game, TV and remote-control simulator apps. Once downloaded, the fake apps hide themselves on the victim’s device and continued to show a full-screen ad every 15 minutes.
Ai.type, for its part, has had security issues in the past– in 2017, over 31 million customers’ personal data was leaked via an exposed database. And, in 2011, the app found itself in hot water for sending users’ keystrokes to developers’ servers in plain text.
Researchers told Threatpost they haven’t reached out to Ai.Type LTD, but typically rather investigate and report their findings “which we always openly share with the public and the security community.”
“It has been the case that after the publication of our reports we are approached by developers for further insights and support,” they told Threatpost.
The researchers advised all consumers who have downloaded Ai.type to check their phones for unusual behavior.
“Users should regularly check their phones and remove any reported malware,” said Upstream researchers. “They should also check their bills for unwanted or unexpected charges for accessing premium data services and to look out for signs of increased data usage which could indicate a malicious app is consuming data in the background.”
What are the top mistakes leading to data breaches at modern enterprises? Find out: Join experts from SpyCloud and Threatpost senior editor Tara Seals on our upcoming free Threatpost webinar, “Trends in Fortune 1000 Breach Exposure.” Click here to register.