A series of targeted attacks are continuing to bully a signed Nvidia application into dropping a backdoor that lets attackers root their way through the systems of Tibetan sympathizers.
According to Sophos’ Gabor Szappanos, the multifaceted attack can install a backdoor on unsuspecting users’ machines to siphon off system information, including the computer’s name and OS version along with other bits of sensitive information.
First the campaign makes use of an old Microsoft Office vulnerability (CVE-2012-0158) that’s been used in multiple exploit vectors over the last six months. The vulnerability primarily exploits rich text file (RTF) documents to distribute malware and gained popularity last month when it was announced it was one of four exploits used in the Red October campaign.
While the vulnerability has been used in the past against Tibetan activists and other Asian military and energy targets, the way the attack leverages an authentic Nvidia tool is interesting.
The RTF document in this case is an article about the Tibetan Youth Congress that acts as a diversion while three files are dropped onto the system: Nv.exe, NvSmartMax.dll and NvSmartMax.dll.url. Nv.exe is a legitimate executable for Nvidia’s Smart Maximise Helper Host, a tool that helps manage properties for the company’s graphics cards. The DLL file is the malicious part of the equation here though, executing encrypted code in NvSmartMax.dll.url that ultimately compromises the computer and grants the attacker the following remote access functionality:
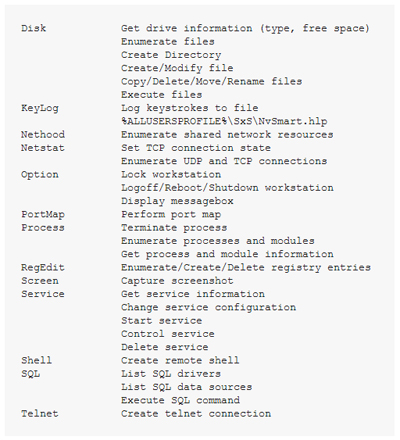
The whole campaign is awfully similar to one used by the remote access tool PlugX, spotted by TrendMicro last September. That attack relied on a different, older Microsoft RTF vulnerability (CVE-2010-3333) but also dropped a handful of Nvidia files, including NvSmartMax.dll, onto systems. Much like the most recent attack, in the 2012 attack NvSmartMax.dll boots up a backdoor (boot.ldr) that that can open and modify files on the infected system.
Sophos has a more detailed explanation of the attack, including its multi step process at Naked Security.









