Malicious traffic stemming from exploits against the Apache Struts 2 vulnerability disclosed and patched this week has tapered off since Wednesday.
Researchers at Rapid7 published an analysis of data collected from its honeypots situated on five major cloud providers and a number of private networks that shows a couple of dozen sources have targeted this vulnerability, but only two, originating in China, have actually sent malicious commands.
Cisco Talos said on Thursday that attacks had risen sharply since word leaked of publicly available exploits and a Metasploit module. But it conceded that it was difficult to ascertain whether probes for vulnerable Apache servers could be carried out benignly.
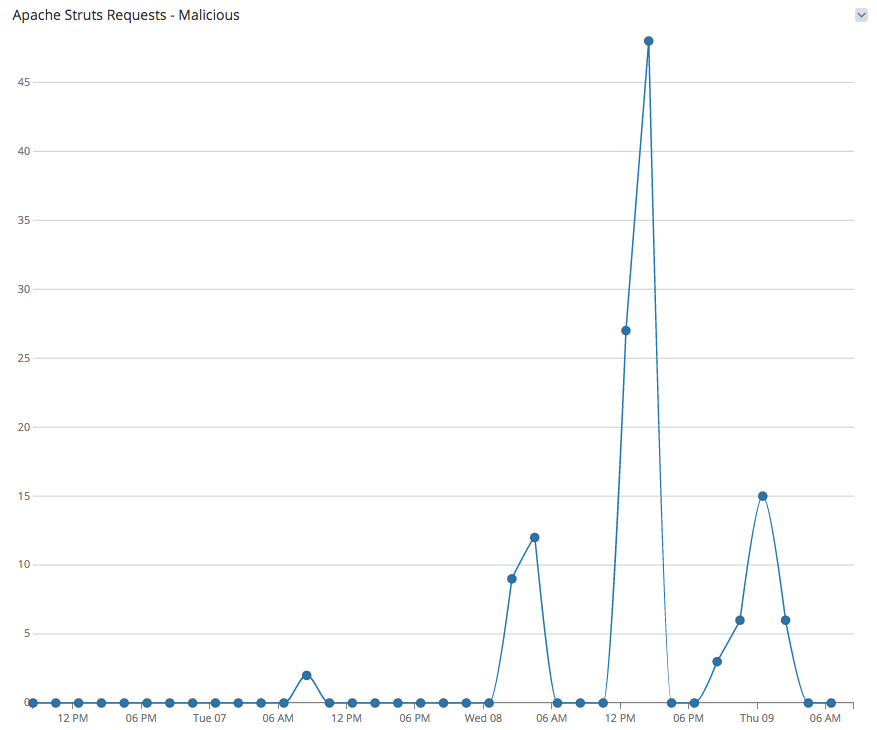
Rapid7 said that in a 72-hour period starting Tuesday, a handful of events cropped up peaking at fewer than 50 between 11 a.m. and 6 p.m. Wednesday.
“We are really seeing limited attempts to exploit the vulnerability,” said Tom Sellers, threat analyst and security researcher at Rapid7. “For context, please keep in mind that our data is from honeypots hosted in cloud providers and may not reflect what other sensors and organizations are seeing.”
Craig Williams, Cisco Talos senior technical lead, said researchers there are seeing attack traffic trending downward as well.
“Early indicators and past experiences were pointing to this being an ongoing issue with attackers continuing to seek out vulnerable machines. Interestingly, over the last couple days, we have seen a slowing of activity,” Williams said. “Because this is so unusual, we are continuing to monitor the situation in case the trend starts moving in the other direction. Again, this is not typical for this type of issue but great news all the same.”
The vulnerability is in the Jakarta Multipart parser that comes with Apache. An attacker can trivially exploit the vulnerability to gain remote code execution by sending a HTTP request that contains a crafted Content-Type value. The vulnerable software will throw an exception in such cases.
“When the software is preparing the error message for display, a flaw in the Apache Struts Jakarta Multipart parser causes the malicious Content-Type value to be executed instead of displayed,” Sellers wrote in an analysis published yesterday.
The vulnerability was disclosed and patched on Monday, and by Tuesday, Rapid7 was seeing two malicious requests from a host geo-located in Zhengzhou, China. The attacks arrived in HTTP GET requests and issued commands to the vulnerable webserver for it to download binaries from the attacker-controlled server on the internet. Sellers called it a standard command-injection attack against a webserver where the attacker is able to write code that instructs the server to reach out to an IP address and download code that executes on the server.
The second attack was spotted Wednesday when a host in Shanghai, China sent HTTP POST requests to servers instructing them to disable their firewall and grab code related to the XOR DDoS malware family.
“While we’ve seen a couple dozen sources exploiting the vulnerability, only those two issued malicious commands,” Sellers said. “We’ve actually seen a drop off in related traffic since Wednesday. The most active attacker stopped on Thursday around 4 a.m. U.S. Central time.”
Sellers said it’s unclear as to why there’s been a dropoff in malicious traffic.
“It could be caused by a number of factors. The malicious payload is pretty obvious and easy to filter if traffic is inspected,” Sellers said. “Attackers might be prioritizing other vulnerabilities such as the ones announced in cameras recently. The lull may be temporary and we may see activity rise again after attention moves on to efforts.”
Cisco raised the issue of IoT devices running the vulnerable Apache software as well, which could be an indicator of initial interest from DDoS bots.
“Given the low sample size it’s difficult for me to say.It’s possible that DDoS bots are the early adopters since infection would generate easy, repeatable income and the code was trivial to port to existing frameworks,” Sellers said. “Compare that to ransomware, where a new deployment mechanism may need to be written but would likely only result in a single payout per host.”
Researchers were also seeing a number of requests probing for additional vulnerable servers that included whoami and ifconfig, commands that are relatively benign but could return information about what context the server is running in. Servers running at root—an uncommon practice—are most at risk.