The Apache Software Foundation today released an advisory warning that a patch issued in March for a zero-day vulnerability in Apache Struts did not fully patch the bug in question.
Officials said a new patch is in development and will be released likely within the next 72 hours, said Rene Gielen of the Apache Struts team.
“Once the release is available, all Struts 2 users are strongly recommended to update their installations,” the advisory said.
In the meantime, ASF provided a temporary mitigation that users are urged to apply.
On March 2, a patch was made available for a ClassLoader vulnerability in Struts up to version 2.3.16.1. An attacker would be able to manipulate the ClassLoader via request parameters. Apache said the fix was insufficient to repair the vulnerability.
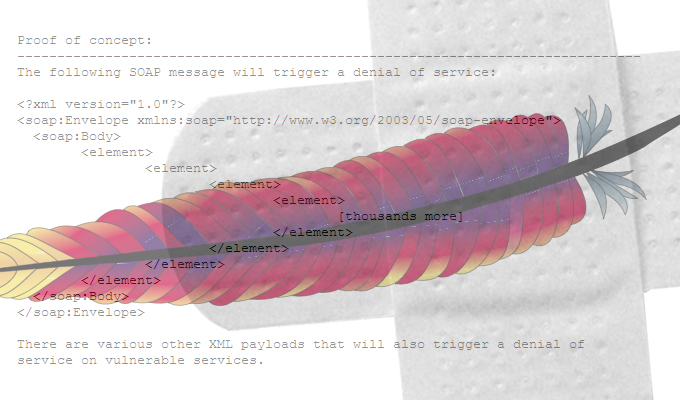
An attacker exploiting the vulnerability could also cause a denial-of-service condition on a server running Struts 2.
“The default upload mechanism in Apache Struts 2 is based on Commons FileUpload version 1.3 which is vulnerable and allows DoS attacks. Additional ParametersInterceptor allows access to ‘class’ parameter which is directly mapped to getClass() method and allows ClassLoader manipulation,” said the original release notes.
Struts is an extensible framework for creating enterprise Java Web applications.
The upcoming release will be the third security update of the year for Struts. In February, the Apache Struts team urged developers to upgrade Struts 2-based projects to use a patched version of the Commons FileUpload library to prevent denial-of-service attacks.