Bad actors are taking advantage of a recently-disclosed iOS bug with a fake website claiming to give iPhone users the ability to jailbreak their phones. In reality, researchers warn, the site ultimately enables attackers to conduct click fraud.
A jailbreak, a method to escape Apple’s limitations on what apps and code can run on the iPhone, is appealing to users who want to install custom code, add features or perform security research outside the purview of the Apple ecosystem.
The fake website centers around a vulnerability called “checkm8,” which affects hundreds of millions of iPhones and gives attackers system-level access to handsets via an unblockable hack. Specifically, the site purports to let users download checkra1n, a soon-to-be-released jailbreak that uses the checkm8 flaw.
The fake website for the jailbreak (checkrain[.]com) was registered within 24 hours of the jailbreak’s official website (checkra1n[.]com). However, unlike the real website, this fake website does not download the jailbreak but instead involves the end user in pay-per-click online advertising fraud.
“This new malicious actor Talos discovered claims to provide the checkra1n jailbreak,” said researchers with Cisco Talos in a Tuesday post. “The site even claims to be working with popular jailbreaking researchers such as ‘CoolStar’ and Google Project Zero’s Ian Beer. The page attempts to look legitimate, prompting users to seemingly download an application to jailbreak their phone. However, there is no application, this is an attempt to install malicious profile onto the end-user device.”
When users visit the fake website, they view a download button that purports to load the checkra1n jailbreak onto their phone (below is a video showing how the fake website operates).
The website contains some red flags that may tip off visitors that it is fake. For instance, the website says the jailbreak works for devices running on the A5 to A13 chipsets – however, checkm8 (and consequently the checkra1n jailbreak) only impacts iOS devices running on the A5 to A11 chipsets.
“Additionally, the website proposes the user can install the checkra1n jailbreak without a PC, when in reality, the checkm8 exploit requires the iOS device to be in DFU mode and is exploitable via the Apple USB cable,” said researchers.
In order to download the iOS jailbreak, the user is prompted to install a “mobileconfig” profile on their iOS device. A “mobileconfig” profile is a type of configuration profile, which are profiles created with Apple’s iPhone Configuration Utility intended for IT departments and cellular carriers.
When downloading a jailbreak (though it depends on the method used by the developer) generally speaking “you will be required to trust a profile/certificate to install unsigned code that is not signed from Apple,” Warren Mercer, Technical Lead at Cisco Talos told Threatpost.
The .mobileconfig files make it easy to distribute network settings to iOS devices – but can also be used for malicious purposes, such as pointing devices at malicious servers and installing malicious certificates. However, the configuration profile in this situation does not appear to be used for these malicious functions, researchers told Threatpost.
“We would also like to know the answer to this, this malicious profile only abused the Apple WebClip functionality and did not attempt to gain privileged access to the devices,” Mercer told Threatpost. “This method allows the attacker to force the web page transitions in a more aesthetically perfect way ie; no search bar, bookmarks or URL bar for the user to see their destinations.
This profile comes with an SSL certificate (which the real checkra1n website does not use): “This is another step the actor has most likely employed in an attempt to draw the user in,” researchers said.
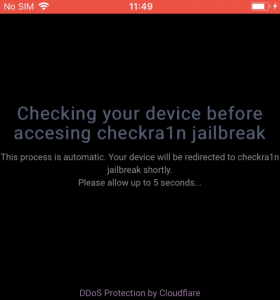
Once the “app” is downloaded and installed, a checkra1n icon appears on the user’s phone. The icon looks like an app to the user, but it is actually a bookmark to a web page clip. When the user clicks on the icon, a web page loads in full screen (with no search bar or URL bar, so that it still looks like an app) that says it is “Checking your device before accessing checkra1n jailbreak.”
Instead, multiple redirects occur on the user’s iOS device, which ultimately prompts users to download an iOS app from the Apple App Store called Pop!Slots (a slot gaming machine app). The web page then tells the users to “have fun” with the iOS gaming app for seven days to ensure their jailbreak unlock completes.
“This ultimately occurs in click-fraud, resulting in multiple verification chains and then finishing on an iOS game install, with in-app purchases available,” researchers said. “This is obviously nonsense — the user will merely provide more interactive sessions through the gameplay, which may result in additional revenue for this attacker.”
The campaign is targeting an array of potential victims globally, including in the U.S., U.K., France, Nigeria, Iraq, Vietnam, Venezuela, Egypt, Georgia, Australia, Canada, Turkey, Netherlands and Italy.
For researchers, the most dangerous part of the campaign is the “mobileconfig” profile download. While this campaign did not appear to make use of the profile in ways more malicious than click fraud, researchers stressed that internet users should never install an unknown profile from the internet.
“This malicious website simply leads to click fraud. But the same technique could be used for more malicious and critical actions. Instead of a ‘web clip’ profile, the attackers could implant their own MDM [mobile device management] enrollment,” they said.
What are the top cyber security issues associated with privileged account access and credential governance? Experts from Thycotic will discuss during our upcoming free Threatpost webinar, “Hackers and Security Pros: Where They Agree & Disagree When It Comes to Your Privileged Access Security.” Click here to register.