Apple has patched a major flaw in its Group FaceTime feature that allowed callers to eavesdrop on people they called even if they never picked up. It also said it would pay a reward to the teen that identified the bug. The update comes along with a slew of other fixes in its release of iOS 12.1.4.
The FaceTime bug, CVE-2019-6223, allowed anyone with iOS to FaceTime other iOS users and listen in on their private conversations – without the user on other end rejecting or accepting the call.
“Today’s software update fixes the security bug in Group FaceTime,” an Apple spokesperson told Threatpost. “We again apologize to our customers and we thank them for their patience. In addition to addressing the bug that was reported, our team conducted a thorough security audit of the FaceTime service and made additional updates to both the FaceTime app and server to improve security.”
According to a Thursday post detailing the update, this vulnerability stemmed from a “logic issue” existing in the handling of Group FaceTime calls.
“The issue was addressed with improved state management,” said the post, which added that the latest version of iOS is available for the iPhone 5s and later, iPad Air and later, and iPod touch 6thgeneration.
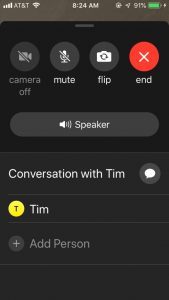
After the bug made headlines last week, Group FaceTime was temporarily disabled. The bug makes use of a new function presented in FaceTime as part of iOS 12.1, called Group FaceTime. In order to take advantage of the flaw, users can first start a FaceTime call with a contact in who also has iOS.
While the call is dialing, they can then swipe up at the bottom of the screen, which lifts the panel and gives them the option to “Add Person.” Users can then click “Add Person” and add their own phone number.
This then begins a FaceTime call that includes the phone user and the audio of the outgoing call – even if the person being called hasn’t accepted the call yet.
While it’s not clear how long the privacy bug has been around, one Twitter user on Jan. 20 said in a Tweet that the bug had been discovered and reported to Apple: “My teen found a major security flaw in Apple’s new iOS. He can listen in to your iPhone/iPad without your approval.”
That teenager, Grant Thompson of Catalina Foothills High School, was credited in Apple’s security update with discovering the bug, along with Daven Morris of Arlington, TX. Apple said it would compensate Thompson for finding the bug and make an unspecified contribution toward his education, according to a report by CNBC.
Other FaceTime Bugs Found
During its security audit of the FaceTime, Apple also found another FaceTime bug that had been previously unidentified, the spokesperson told Threatpost.
The bug was a “previously unidentified vulnerability in the Live Photos feature of FaceTime,” the spokesperson said. “To protect customers who have not yet upgraded to the latest software, we have updated our servers to block the Live Photos feature of FaceTime for older versions of iOS and macOS.”
Apple did not release further information about the vulnerability, CVE-2019-7288.
Other bugs that were addressed in the update include a memory corruption issue that could allow an application to gain elevated privileges (CVE-2019-7286) and a memory corruption issue that may allow an application to execute arbitrary code with kernel privileges(CVE-2019-7287).
Interested in learning more about mobile enterprise security threats and best practices? Don’t miss our free Threatpost webinar on Feb. 27 at 2 p.m. ET. Join Threatpost senior editor Tara Seals and a panel of mobile security experts, including Patrick Hevesi of Gartner, to discuss the top evolving threats and risks that are unique to this work-from-anywhere environment; best practices for addressing them; and new challenges on the horizon, such as 5G services.