A new email phishing scam is making use of a realistic-looking Apple login page in order to pilfer Apple ID usernames and passwords before moving on to steal user credit card information.
According to SANS Internet Storm Center forums member, Craig Cox, this phishing scam is particularly sophisticated because of its use of JavaScript code that purports to validate whether Apple IDs entered into the malicious field are legitimate. In other words, if a user falls for the trick, but enters the incorrect Apple ID, the site will come back and ask that the user “Double check that [he or she] typed a valid Apple ID.”
The malicious domain that the attackers are using here is appleidconfirm[dot]net.
It’s not clear whether the attackers have found a way to distinguish legitimate Apple ID email addresses from a non-existent one. However, once the victim has entered what is considered valid credentials, that person is redirected to another part of the malicious domain (ending in /?2).
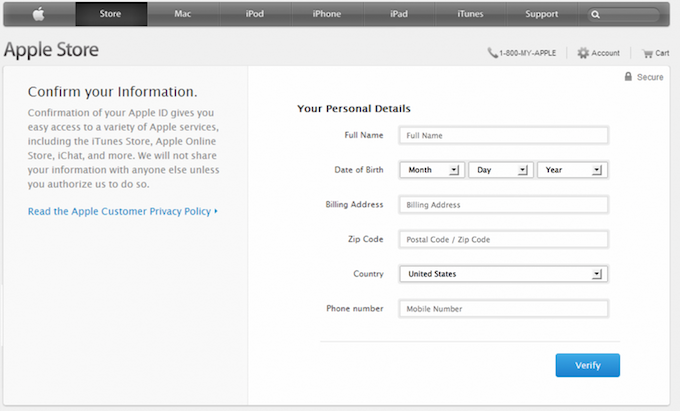
On this second page, users are presented with a convincing replica of the actual Apple website. The page requests various pieces of personal information, such as full names, dates of birth, billing addresses, and phone numbers. When and if a victim enters that information and clicks the “verify” button, a window then pops up asking for the user’s payment card information.
If the victim decides to enter payment information, he or she will be redirected to the actual Apple website.
According to a technical analysis posted in the ICS Diary write-up, the site responsible for all this tomfoolery was registered just three days ago. The reason the attackers were able to mimic Apple’s interface so accurately is because they didn’t copy its HTML or CSS, but rather overlaid their website with screenshots. Of course, because of this method, the scam becomes a bit of a dead giveaway when and if a user attempts to follow any links on the masquerading site. Another dead giveaway, the post notes, is the lack of HTTPS, which Apple would deploy if it were asking users to provide sensitive information.
A similar scam emerged last week when attackers compromised a server belonging to EA Games and modified it to look like an Apple log-in page, which they then used in a phishing attack designed to steal Apple ID credentials.