Any cut-and-paste data temporarily stored to an iPhone or iPad’s memory can be accessed by all apps installed on the specific device – even malicious ones. That data can then reveal private information such as a user’s GPS coordinates, passwords, banking data or a spreadsheet copied into an email.
Shedding light onto the potential harm of this scenario is German software engineer, Tommy Mysk, who is trying to raise awareness around what he believes is an Apple vulnerability. To illustrate his concerns, Mysk created a rogue proof-of-concept (PoC) app called KlipboardSpy and an iOS widget named KlipSpyWidget.
Both are designed to illustrate how any app installed on an iOS device can act maliciously and access clipboard data and use it to spy or steal sensitive personal information. To highlight and demonstrate his concerns, Mysk told Threatpost he focused on photos taken by a device’s camera that contain time and GPS metadata that could be used to pinpoint a user.

“A user may unwittingly expose their precise location to apps by simply copying a photo taken by the built-in Camera app to the general pasteboard,” the developer wrote in a technical blog post outlining his research on Monday.
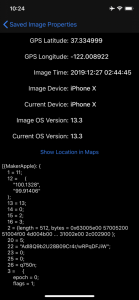 “Through the GPS coordinates contained in the embedded image properties, any app used by the user after copying such a photo to the pasteboard can read the location information stored in the image properties, and accurately infer a user’s precise location. This can happen completely transparently and without user consent,” he wrote.
“Through the GPS coordinates contained in the embedded image properties, any app used by the user after copying such a photo to the pasteboard can read the location information stored in the image properties, and accurately infer a user’s precise location. This can happen completely transparently and without user consent,” he wrote.
Apple, in response to his research, said it didn’t consider its implementation of cut-and-paste as a vulnerability, rather a basic function of most operating systems and applications that run on them, Mysk told Threatpsot.
Apple did not return Threatpost’s request for comment for this story.
Mysk said that any app that can constantly read a device’s clipboard can easily abuse the data.
One caveat to the developer’s research was that iOS can only allow apps to read clipboard data when the apps are active and in the foreground. The workaround was to create KlipSpyWidget, an Apple Widget visible in the iPhone’s Today View.
“A widget placed on top of the Today View can read the pasteboard every time the user swipes to the Today View, hence expanding the vulnerability window,” he wrote.
Apple is no strangers to clipboard concerns. Three years ago a Reddit user pleaded; “Apple should fix the clipboard on iOS to make accessing it require Permission. This is a massive opening for malicious apps.”
While some Reddit users defended Apple’s practice, others supported the poster’s opinion.
“The whole point of the clipboard is to copy/paste text between apps. You want text to stay inside the clipboard and only be accessed when you manually hit paste? Makes sense to me,” wrote a user that goes by the name of crushed_oreos.
For Mysk, he also believes Apple should put permissions around clipboard data the same way apps request permission to access an iPhone’s Contacts and Location Services. “Apps should not have unrestricted access to the pasteboard without user’s consent. The best fix for this exploit is by introducing a new permission that enables the user to grant access to the pasteboard by app, just like contacts, location services, and photos,” he wrote.
In the case of GPS-data leaking from photos, he suggests, “operating systems automatically delete location information from photos once they are copied to the pasteboard.”
Clipboard-related attacks have been a staple for years in Windows environments and on the Android platform. In 2018, cryptocurrency malware infected 2.3 million bitcoin addresses. The malware targeted clipboard data during bitcoin transactions. Once a transaction was initiated, and data was stored to the clipboard, the malware would switch account data in memory and redirect bitcoins into an attack’s wallet.










