Despite law-enforcement wins in the form of several high-profile arrests and indictments during 2018, nation-state adversaries have upped their games when it comes to speed.
That’s according to CrowdStrike’s 2019 Global Threat Report, which found that when analyzing how long it takes to go from initial compromise to the attacker’s first lateral movement within the network, Russian-speaking APTs (such as Fancy Bear) have the most chops, with an average time of just over 18 minutes. That’s almost eight times faster than second-ranked North Korea-linked threats (Lazarus Group/Chollima, for instance), which had a collective average time of two hours and 20 minutes.
Chinese nation-state actors like Deep Panda meanwhile averaged about four hours, and Iranian nation-state actors (i.e., Charming Kitten) came in around five hours.
This metric – which CrowdStrike calls “breakout time,” is a key indicator of agility, according to Dmitri Alperovitch, CrowdStrike co-founder and CTO.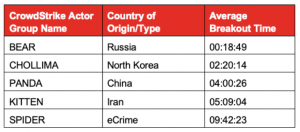
“Whether you are a defender or an attacker, you have to be faster than your opponent, or get inside of their OODA Loop, as the military strategists will tell you, in order to achieve success,” he explained in a Tuesday blog post. “The OODA Loop is a concept invented by U.S. Air Force Colonel John Boyd, initially applied to military combat operations, but since then expanded to cyber-conflict and even business strategy. One of the key ideas behind it is that all the opponents on a battlefield — physical or virtual — go through a four-stage rapid decision cycle: Observe, Orient, Decide and Act. The actor who can process this cycle the fastest, or get inside the other’s decision cycle, will prevail.”
For comparison’s sake, financial crime rings have the slowest average breakout time of all adversaries, at nine hours and 42 minutes, “although some of the eCrime actors can move very rapidly and rival even the fastest nation-states,” according to the report.
Of course, breakout time fluctuates depending on defenses, Alperovitch pointed out. “It can vary widely based on the capabilities of defenders — so if an adversary consistently targets networks with as many holes as Swiss cheese, moving laterally is much easier and can be done a lot faster,” he said.
Attack Techniques
A very high prevalence of scripting techniques, including PowerShell, command-line interface and related techniques tend to mark the initial intrusion activity, the report found. But tracking adversaries’ movements from there can be difficult to do.
“Once attackers obtain an initial foothold, the next steps of discovery, persistence and lateral movement often require a human touch,” according to the report. “After attackers obtain their initial foothold, their first order of business is to get oriented within their newly accessed environment before determining next steps toward their objective. This behavior very commonly shows itself via a wide range of discovery techniques.”
Actions involved in discovery are easy to miss, as the attacker is typically using the same standard commands and tools that are often used for legitimate administration purposes. However, watching for unusual clusters of discovery activities, at unusual times, can lead to success in early detection of malicious actors.
Adversaries are also frequently seen using valid account credentials across the attack lifecycle. Credentials are typically obtained via successful phishing, brute force or credential dumping methods.
Cyberattack Targets
Meanwhile, the report also found that China-linked APTs were the most active and prolific adversaries observed in 2018, with more targeted intrusions than both Russia and Iran combined, the report found. This accelerated over the course of the year, tied to geo-political activity. “CrowdStrike observed an increasing operational tempo from China-based adversaries, which is only likely to accelerate as U.S.-China relations continue to be strained,” according to the report.
In terms of targets, CrowdStrike said that APT originating from China, Iran and Russia each heavily targeted the data-rich telecommunications sector for intrusions. Subsequent lures to drive more effective social engineering campaigns also resulted in the compromise of telecom customers, including government entities.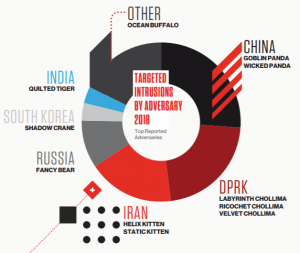
Other trends noted in the report include North Korean APTs remaining active in both intelligence collection and currency-generation schemes. Iranian APTs maintain a focus on operations against other Middle Eastern and North African (MENA) countries, particularly regional foes across the Gulf Cooperation Council (GCC).
“Additionally, it is suspected that Iranian adversaries are developing new mobile malware capabilities to target dissidents and minority ethnic groups,” the report noted.
Russian APTs meanwhile were active across the globe in a variety of intelligence collection and information operations.
Overall, CrowdStrike expects nation-state activity to continue along these same trend lines for 2019.











