A Microsoft Office vulnerability patched six months ago continues to be a valuable tool for APT gangs operating primarily in Southeast Asia and the Far East.
Researchers at Kaspersky Lab today published a report describing how attackers continue to flourish exploiting CVE-2015-2545, a remote code execution vulnerability where an attacker crafts an EPS image file embedded in an Office document designed to bypass memory protections on Windows systems.
Exploits have been used primarily to gain an initial foothold on targeted systems. Those targets are largely government and diplomatic agencies and individuals in India and Asia, as well as satellite offices of those agencies in Europe and elsewhere.
The Office flaw was patched in September in MS15-099 and updated again in November. Yet APT groups seem to be capitalizing on lax patching inside these high-profile organizations to carry out espionage. Some criminal organizations have also made use of exploits against this particular flaw, in particular against financial organizations in Asia, Kaspersky researchers said in their report.
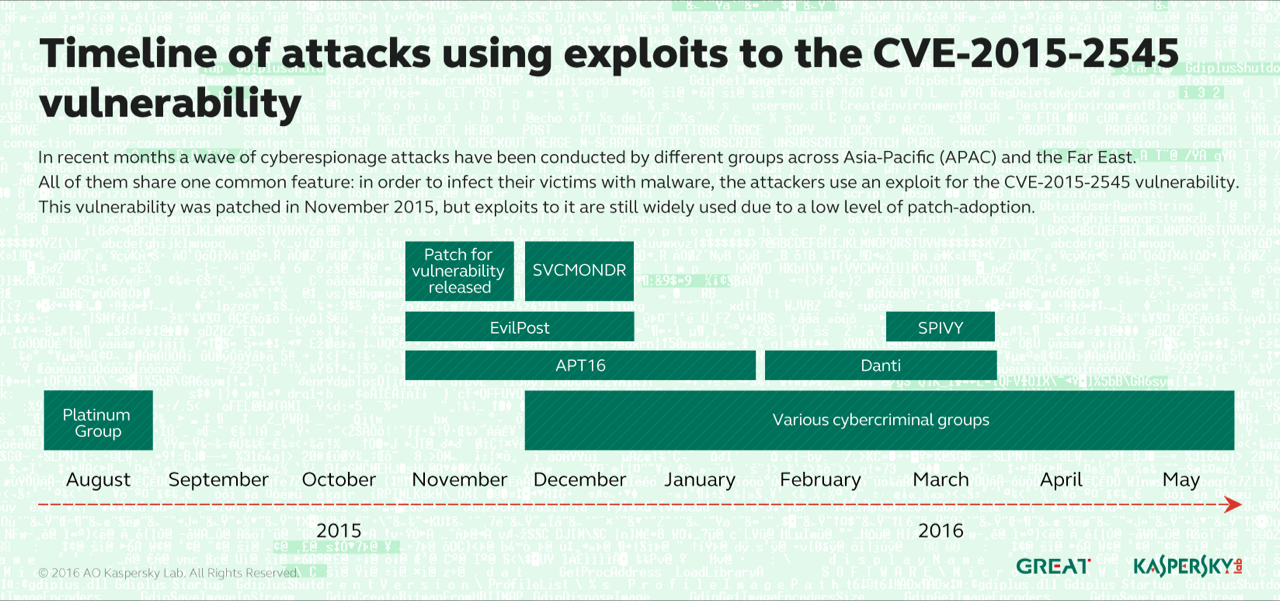
The APT groups, however, seem to be having the most ongoing success with CVE-2015-2545. Kaspersky Lab identified a half-dozen groups, including two new outfits, that have been using modified exploits for the flaw.
The new players are known as Danti and SVCMONDR. Danti is a relative newcomer operating since 2015 and primarily against Indian government organizations. It has recently branched out against targets in Kazakhstan, Kyrgyzstan, Uzbekistan, Myanmar, Nepal and the Philippines, Kaspersky said.
In February and March, researchers saw Danti attacks moving via spear-phishing emails laced with a .docx file that exploits the Microsoft flaw and drops custom shellcode on compromised machines.
“The exploit is based on a malformed embedded EPS (Encapsulated Postscript) object,” Kaspersky researchers wrote in their report. “This contains the shellcode that drops a backdoor, providing full access to the attackers.”
The February attacks were concentrated against the Indian Ministry of External Affairs starting Feb. 2 and concluding Feb. 29, the report says. Indian embassies in Hungary, Denmark and Colombia were also targeted.
The emails contained relevant subject lines to the targets and spoofed legitimate email addresses belonging to high-ranking officials, including the IT director of India’s Ministry of Communications and Information Technology.
In March, the Danti group struck again, in particular against a number of people inside the Cabinet Secretariat of Government India from an email spoofing a high-ranking government official. A modified version of previous EPS exploits dropped a backdoor and other capabilities that monitored system information and gave the attackers the ability to modify files, execute commands, terminate processes and gain a shell.
SVCMONDR used spear-phishing messages to hit targets in Taiwan with exploits that hint at a connection to the Danti group as well as APT 16, what is thought to be a separate APT gang. However, its emails came from the same domain as the SVCMONDR attackers, using different shellcode and dropping a new backdoor.
The EPS exploits drop a program called SVCMONDR.exe that embeds itself in the registry for persistence and that establishes a backdoor through which commands and stolen files are sent.
Kaspersky’s report also implicates the Platinum APT group as the first to exploit CVE-2015-2545. Platinum was identified by Microsoft; it used EPS exploits against targets in India as early as last August. A recent Microsoft reports described some of Platinum’s exploits, including its ability to abuse a hotpatching feature introduced in Windows in 2003 and available until it was removed in Windows 8. The abuse of hotpatching allows the attackers to inject malicious code into running processes without having to reboot the server. Hotpatching requires admin privileges, therefore the attackers have to already be on the box to make use of this technique.
Kaspersky also said in addition to APT 16, which targeted news agencies in Taiwan late last year, another APT group known as EvilPost has been exploiting the EPS flaw.
EvilPost used the EPS exploit to hit defense contractors in Japan; in one attack described by Kaspersky, EvilPost attackers used an embedded and maliciously crafted EPS object embedded in an Office document to run a shell on compromised machines and drop a separate DLL that exploited CVE-2015-1701, a privilege escalation vulnerability. With elevated permissions, the attackers were then able to backdoor systems and reach out to command servers to download more malware.
The Kaspersky report, however, said that the attackers no longer have access to a command server in Japan and theorize either it was compromised or the attackers abandoned their mission after researchers discovered it.
The remaining APT group outed by Kaspersky is called Spivy; it targeted organizations in Hong Kong and used a variant of the Poison Ivy backdoor to steal information.
Technical information and indicators of compromise are available on Securelist.com.