 A researcher at Qualys has released a new tool designed to allow users–even non-technical ones–to evaluate the security and behaviors of the apps installed on their Android devices. Known as the Android Security Evaluation Framework, the tool not only looks at the general security of an app, but also at what kind of data the app is collecting and what it’s doing with that information.
A researcher at Qualys has released a new tool designed to allow users–even non-technical ones–to evaluate the security and behaviors of the apps installed on their Android devices. Known as the Android Security Evaluation Framework, the tool not only looks at the general security of an app, but also at what kind of data the app is collecting and what it’s doing with that information.
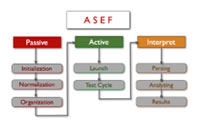
Parth Patel of Qualys unveiled ASEF at Black Hat last week, and the framework is now available for download from Google Code. Once installed, ASEF analyzes apps in an interesting way. It moves each app into a separate test environment, called the Android Virtual Device, and then sends the app a series of random gestures to see how it behaves. The ASEF tool also will gather a pre-determined set of data about the way that phone is working, through network logs and other data stores.
“Android Security Evaluation Framework (ASEF) performs this analysis while alerting you about other possible issues. It will make you aware of unusual activities of your apps, will expose vulnerable components and help narrow down suspicious apps for further manual research. The framework will take a set of apps (either pre-installed on a device or as individual APK files) and migrate them to the test suite where it will run it through test cycles on a pre-configured Android Virtual Device (AVD),” the ASEF documentation says.
Patel said that despite the somewhat technical nature of ASEF’s mission, the tool is designed for use by a wide variety of people, not just security researchers or engineers.
“It is intended to be used by both researchers and regular Android users and so I kept it very easy to use and user-friendly. One area of improvement as I mentioned in my presentation and which I am currently working on is to add a UI in order to make it even more accessible and represent the data in pictorial form to make the most sense out of it. This will be available in the next releases of upcoming versions of ASEF,” Patel said.
ASEF is open-source and Patel said it’s meant to be usable with other Android security tools. In addition to watching how apps react to certain gestures, ASEF also will look for odd behaviors that may indicate malicious or unwanted apps on the device.
“It will capture log events, network traffic, kernel logs, memory dump, running processes and other parameters at every stage which will later be utilized by the ASEF analyzer. The analyzer will try to determine the aggressive bandwidth usage, interaction with any command and control (C&C) servers using Google’s safe browsing API, permission mappings and known security flaws. ASEF can easily be integrated with other open source tools to capture sensitive information, such as SIM cards, phone numbers and others,” the documentation says.
ASEF is one of the new group of Android security apps, which also includes X-Ray, a free tool that users can install on their Android devices to scan for a group of known vulnerabilities.









