Spreading malware with a legitimate digital certificate is an adversary’s dream come true, with plenty of successful examples tracing back to nation-state attacks such as Stuxnet and Flame, and other misuse that crops up on a regular basis.
For a group of University of Maryland researchers, the nagging problems surrounding certificate abuse illustrate a shortcoming to the code-signing public key infrastructure. In an academic report released last week at the ACM Conference on Computer and Communications Security called Certified Malware: Measuring Breaches of Trust in the Windows Code-Signing PKI, the researchers highlighted three weaknesses.
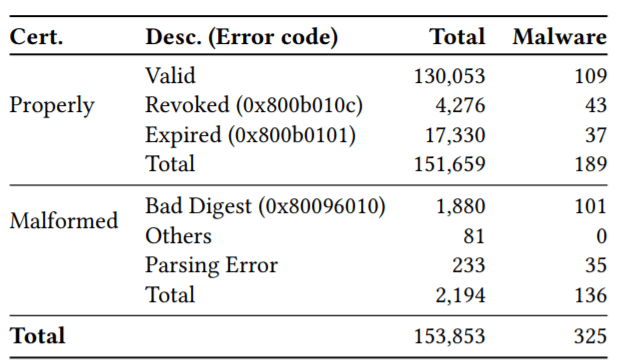
After reviewing more than a 150,000 malware samples from a 2014 data set, below, researchers found 325 malicious software programs signed with either a valid, revoked or malformed certificate.
“Digitally signed malware can bypass system protection mechanisms that install or launch only programs with valid signatures. It can also evade antivirus programs, which often forego scanning signed binaries,” wrote University of Maryland researchers Doowon Kim, Bum Jun Kwon and Tudor Dumitras.
Researchers said certificate abuse boils down to three types of weaknesses in the code signing PKI: inadequate client-side protections of certificates, publisher-side key mismanagement, and certificate authority-side verification failures.
In an example of the case of inadequate client-side protections of certificates, researchers said simply copying an Authenticode signature from a legitimate file can reduce AV detection by 20.7 percent.
In the case of publisher-side key mismanagement, the report found 72 likely compromised publisher certificates from its sample of 325. When researchers contacted eight of the publishers to notify them of the undermined certificates five were unaware of the abuse.
Researchers said 27 certificates it examined were issued to malicious actors impersonating legitimate companies, underscoring certificate authority-side verification failures.
Researcher Kim, in an interview with Threatpost, said that nagging problems with code-signing are systemic and PKI abuses are getting worse and not better. “We found that 80 percent of abusive certificates remain a threat for almost six years after they are fist used to sign malware,” Kim said.
The study identified revoking certificates was a major problem. “We found that only 27 certificates were revoked after they should have been. The remaining untrustworthy certificates may still be trusted today as long as they carry a trusted timestamp,” according to Kim.
Researchers explain, where previous research into abuses in the code-signing ecosystem have focused on potentially unwanted programs (PUPs) such as adware, their focus was on threats that breached the trust in the Windows code-signing PKI.
“While Windows operating systems have the ability to verify code-signing signatures, they often allow unsigned or improperly signed software to be installed and executed,” the report said. “If a program requires elevated privileges, UAC notifies the user and includes a message about the publisher’s identity (or lack thereof, if the signature is invalid). However, if the user chooses to grant the privilege, Windows does not take further enforcement actions.”
Part of the research also included tests against Google Chrome and Microsoft Internet Explorer 9 and their respective Safe Browsing and SmartScreen features which protect against malicious downloads. In a test using a malformed digital certificate, researchers found by remove the file extension (.exe), the browsers do not block the download and bypass the browser protections.
“Windows provides minimal protections against executables using forged signatures, while browser defenses apply only to files downloaded from the Web and can be bypassed. The last line of defense, therefore, is antivirus products,” according to researchers.
However researchers said that sometimes incorrect implementation of Authenticode signature checks in some AV products allow malware authors to evade detection. “We believe that this is due to the fact that AVs take digital signatures into account when filter and prioritize the list of files to scan, in order to reduce the overhead imposed on the user’s host,” researchers said.
Researchers said they have cautioned some AV companies of the potential for incorrect implementation of Authenticode signature checks. Kim said that AV vendors have been extremely responsive.