ASUS has expedited a patch for a major bug impacting thousands of PCs that allowed an advanced persistent threat group to launch a supply-chain attack dubbed “Operation ShadowHammer.” The vulnerability targeted a range of new ASUS PCs with a backdoor injection technique tied to the PC-maker’s faulty software update mechanism. The flaw was used to infect thousands of PC and was found by researchers at Kaspersky Lab and revealed Monday.
The attack targeted users of the ASUS Live Update Utility. The China-backed BARIUM APT is suspected to have deployed the backdoor code, which would give it access to impacted systems, according to researchers.
ASUS for its part said in a Tuesday post that it has implemented a fix in the latest version (version 3.6.8) of the Live Update software.
In addition the manufacturer said it has “introduced multiple security verification mechanisms to prevent any malicious manipulation in the form of software updates or other means, and implemented an enhanced end-to-end encryption mechanism.”
“A small number of devices have been implanted with malicious code through a sophisticated attack on our Live Update servers in an attempt to target a very small and specific user group,” said ASUS. “ASUS customer service has been reaching out to affected users and providing assistance to ensure that the security risks are removed.”
Kaspersky Lab first contacted ASUS on Jan. 31, 2019, to inform it about the attack and share IOCs and descriptions of the malware.
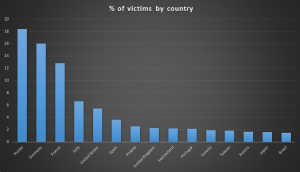
According to researchers, the campaign ran from June to November 2018. More than a million worldwide may have been impacted, with the cybercriminals targeting specific victims in Asia.
“The command and control server used in this attack has been shut down as of November 2018,” a Kaspersky Lab spokesperson told Threatpost. “It is currently unclear if it was shut down by the attackers themselves, or by the registrar. Nevertheless, this means that the backdoor, even if it is still present on victim’s machines, is unlikely to be activated again. To be safe, we recommend affected users to scan and clean their computers with a product capable of detecting this threat.”
Kaspersky Lab said that the adversaries first launched the attack via stolen digital certificates used by ASUS to sign legitimate binaries. They then altered older versions of ASUS software to inject their own malicious code.
Trojanized versions of the utility were then signed with legitimate certificates and were hosted on and distributed from official ASUS update servers – which made them mostly invisible to the vast majority of protection solutions, according to researchers.
While ASUS stressed that the attack impacted “only a very small number of specific user group were found to have been targeted by this attack,” the ASUS Live Update Utility is pre-installed in most new ASUS computers, for automatic BIOS, UEFI, drivers and applications updates.
ASUS ranks fifth in the laptop market, with a market share of 7.4 percent as of August 2018, according to TrendForce. With an estimated 41.08 million laptops shipped in that quarter, it means ASUS sold around 3 million during that time period.
If users have an impacted devices, they need to immediately run a backup of their files and restore their operating system to factory settings, said ASUS. “This will completely remove the malware from your computer. In order to ensure the security of your information, ASUS recommends that you regularly update your passwords,” it said.
Threatpost will continue to update as more information becomes available.