Attackers didn’t wait long to capitalize on laggards slow in updating their WordPress sites to patch a critical content injection vulnerability addressed in WordPress 4.7.2.
The update was made public on Jan. 26 with WordPress disclosing six days later that the update also included a silent fix for an unauthenticated privilege escalation flaw in a REST API endpoint.
Researchers as Sucuri, who privately disclosed the vulnerability to WordPress, today said they’ve seen four different campaigns targeting sites still not patched. WordPress includes a default feature that automatically updates sites, but some users choose to disable this feature and test updates before they’re pushed to critical sites running on the platform.
The four campaigns are doing mass scans across the Internet looking for sites running vulnerable versions of WordPress and attempting to exploit the vulnerability. Most of the attacks started within two days of public disclosure, and are leading to website defacements.
“We see the same IP addresses and defacers hitting almost every one of our honeypots and network,” Sucuri researcher Daniel Cid wrote in a report published today. “If Google is correct, these defacers seem to be succeeding.”
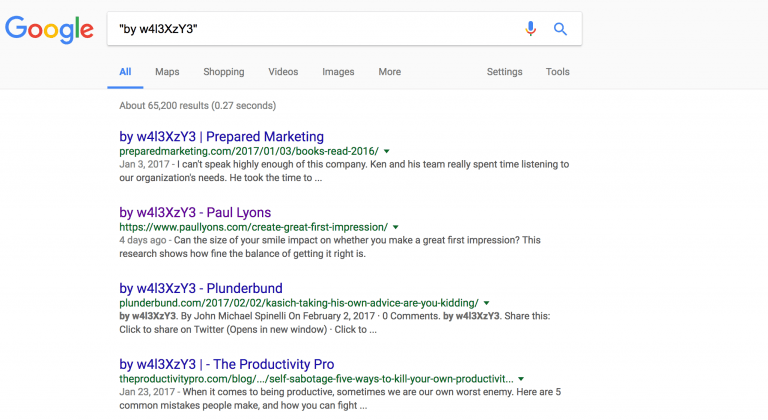
The largest campaign has already compromised more than 66,000 webpages running on WordPress, and that number could continue to spike as Google re-indexes pages. Sucuri identifies this group as w4l3XzY3 and has catalogued four IP addresses used in these defacements: 176[.]9[.]36[.]102, 185[.]116[.]213[.]71, 134[.]213[.]54[.]163, and 2a00[:]1a48[:]7808[:]104[:]9b57[:]dda6[:]eb3c[:]61e1.
The three other campaigns have compromised around 500 pages each with Sucuri identifying Cyb3r-Shia, By+NeT.Defacer, and By+Hawleri_hacker as the groups responsible; Sucuri said it publicly named the groups in case any of those names show up in a post, admins will known the REST API vulnerability was likely exploited.
“What we expect to see is a lot more SEO spam (Search Engine Poisoning) attempts moving forward,” Cid said. “There’s already a few exploit attempts that try to add spam images and content to a post. Due to the monetization possibilities, this will likely be the No. 1 route to abuse this vulnerability.”
A WordPress Core maintainer told Threatpost the initial delay in disclosure was an attempt to give sites time to patch. The vulnerability is trivial to exploit and an attacker could exploit the issue to modify content on the page, or create or delete posts. Technical details were published last week by Sucuri.
Site administrators are urged to patch immediately, or risk damaging their search engine reputation on Google should spammers successfully exploit the flaw.