 Attackers are constantly changing their tactics and adapting to what the security community and researchers are doing, and it’s not unusual for the bad guys to adopt techniques used by their adversaries. The latest example of this is a malware gang that has deployed what amounts to a honeypot designed to monitor the activity of researchers or other attackers who try to access a command-and-control server.
Attackers are constantly changing their tactics and adapting to what the security community and researchers are doing, and it’s not unusual for the bad guys to adopt techniques used by their adversaries. The latest example of this is a malware gang that has deployed what amounts to a honeypot designed to monitor the activity of researchers or other attackers who try to access a command-and-control server.
While researching a piece of malware related to the Zeus botnet, a group of researchers at The Last Line of Defense gained access to a remote server used to help control the attack. This particular attack was sending out huge amounts of spam throughout October, specifically targeting business owners who file quarterly taxes. Known as the EFTPS malware, the spam included a link that sent victims to a site that loaded the Zeus Trojan on their machines and then forwarded them to the actual site at the Treasury Department that handles these payments.
But the interesting part is what the researchers found when the accessed the back end server: a fake administrative console. Many, if not most, large-scale malware campaigns now have some kind of admin interface on a remote server that enables the attackers to login and access statistics on infections, geographic distribution of compromised PCs and other measurements. And researchers have been able to access these consoles on a number of occasions, mining them for key intelligence on the attackers behind the malware and how the attack works.
But in this case, the attack crew apparently anticipated this and set up a phony login interface, complete with weak username and password and a simple SQL-injection vulnerability. The console clearly is meant to attract researchers, and perhaps other attackers, to poke around and allow the crew behind EFTPS to observe their movements and methods.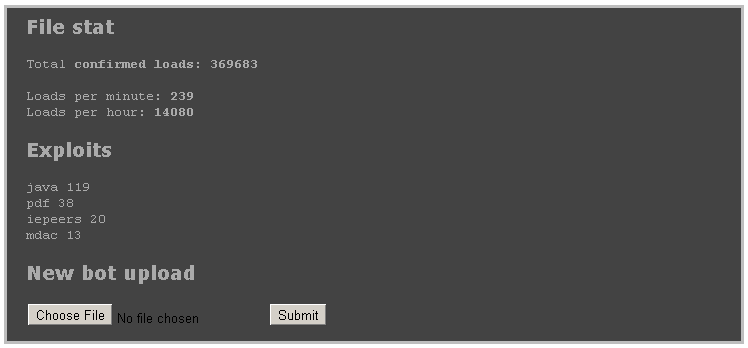
“This admin interface acts as a ‘hacker honeypot’ that records
detailed information about who attempted to access the admin console, as
well as who attempted to hack into it. The fake login system
conveniently accepts default/easily guessed credentials and common SQL
injection strings. After the researcher/hacker is ‘authenticated’, they are shown random exploit statistics,” the Last Line of Defense researchers said in a blog post.
The admin console also has a feature that allows remote users to upload new “bots,” a tactic evidently designed to entice other attackers to try and compromise the server so the EFTPS crew can get a read on what they’re up to.
Legitimate security researchers have been using honeypot systems for years now and they have become a key tool for gathering information on new exploits, attack techniques and botnet research. The most prominent example is The Honeynet Project, a network of volunteers around the world who maintain complex honeypots and publish a lot of research based on what they collect and observe.









