Attackers were spotted targeting over one million WordPress websites in a campaign over the weekend. The campaign unsuccessfully attempted to exploit old cross-site scripting (XSS) vulnerabilities in WordPress plugins and themes, with the goal of harvesting database credentials.
The attacks were aiming to download wp-config.php, a file critical to all WordPress installations. The file is located in the root of WordPress file directories and contains websites’ database credentials and connection information, in addition to authentication unique keys and salts. By downloading the sites’ configuration files, an attacker would gain access to the site’s database, where site content and credentials are stored, said researchers with Wordfence who spotted the attack.
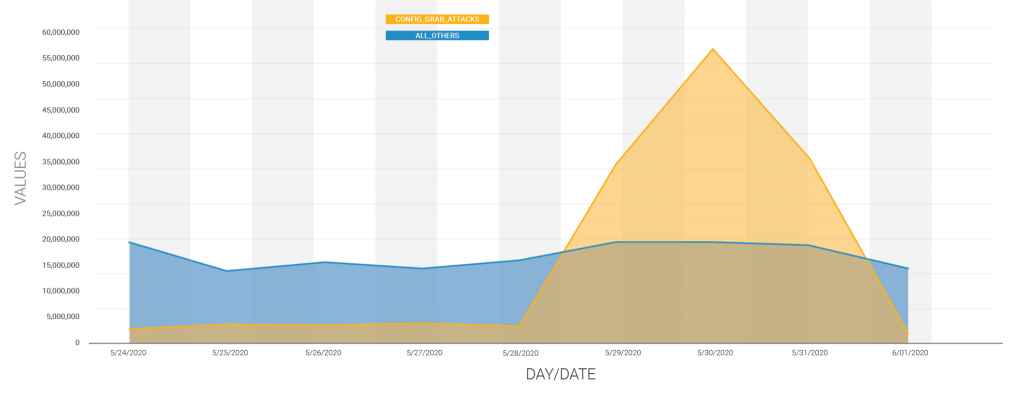
Between May 29 and May 31, researchers observed (and were able to block) over 130 million attacks targeting 1.3 million sites.
“The peak of this attack campaign occurred on May 30, 2020,” said Wordfence researchers on Wednesday. “At this point, attacks from this campaign accounted for 75 percent of all attempted exploits of plugin and theme vulnerabilities across the WordPress ecosystem.”
Researchers linked the threat actor in this incident to an attack earlier in May previously targeting XSS vulnerabilities. These previous campaigns, which began on April 28, attempted to inject a malicious JavaScript into websites, that would then redirect visitors and take advantage of an administrator’s session to insert a backdoor into the theme’s header.
“After further investigation, we found that this threat actor was also attacking other vulnerabilities, primarily older vulnerabilities allowing them to change a site’s home URL to the same domain used in the XSS payload in order to redirect visitors to malvertising sites,” researchers said at the time.
That campaign sent attacks from over 20,000 different IP addresses, said researchers. This most recent campaign is using the same IP addresses, which accounted for the majority of the attacks and sites targeted, leading researchers to link the two campaigns.
The more recent campaign has also expanded in its targeting, researchers said, now reaching nearly a million new sites that weren’t included in the previous XSS campaign. As with the XSS campaigns, almost all of the attacks are targeted at older vulnerabilities in outdated plugins or themes that allow files to be downloaded or exported.
While hundreds of exploits are being attempted, researchers told Threatpost that among the CVEs being most frequently used are CVE-2014-9734, CVE-2015-9406, CVE-2015-5468 and CVE-2019-9618. The attacker appears to be systematically scraping exploit-db.com and other sources for potential exploits – and then running them against a list of sites, researchers told Threatpost.
“Most of them are in themes or plugins designed to allow file downloads by reading the content of a file provided in a query string and then serving it up as a downloadable attachment,” said Ram Gall, with Wordfence.
Researchers said websites that may have been compromised must change their database password and authentication unique keys and salts immediately.
“If your server is configured to allow remote database access, an attacker with your database credentials could easily add an administrative user, exfiltrate sensitive data, or delete your site altogether. Even if your site does not allow remote database access, an attacker who knows your site’s authentication keys and salts may be able to use them to more easily bypass other security mechanisms.”
Researchers also urged users to ensure that their plugins are updated, as vulnerabilities in WordPress plugins and themes continue to be an issue. A few weeks ago, for instance, researchers disclosed two flaws in Page Builder by SiteOrigin, a WordPress plugin with a million active installs that’s used to build websites via a drag-and-drop function. Both security bugs can lead to cross-site request forgery (CSRF) and XSS.
In this recent campaign, many of the flaws had patches available – but users had not updated, leaving their websites vulnerable: “Nonetheless, we urge you to make sure that all plugins and themes are kept up to date, and to share this information with any other site owners or administrators you know,”said researchers. “Attacks by this threat actor are evolving and we will continue to share additional information as it becomes available.”