Spam campaigns delivering Zyklon HTTP malware are attempting to exploit three relatively new Microsoft Office vulnerabilities. The attacks are targeting telecommunications, insurance and financial service firms.
According to FireEye researchers who identified the campaigns, attackers are attempting to harvest passwords and cryptocurrency wallet data along with recruiting targeted systems for possible future distributed denial of service attacks.
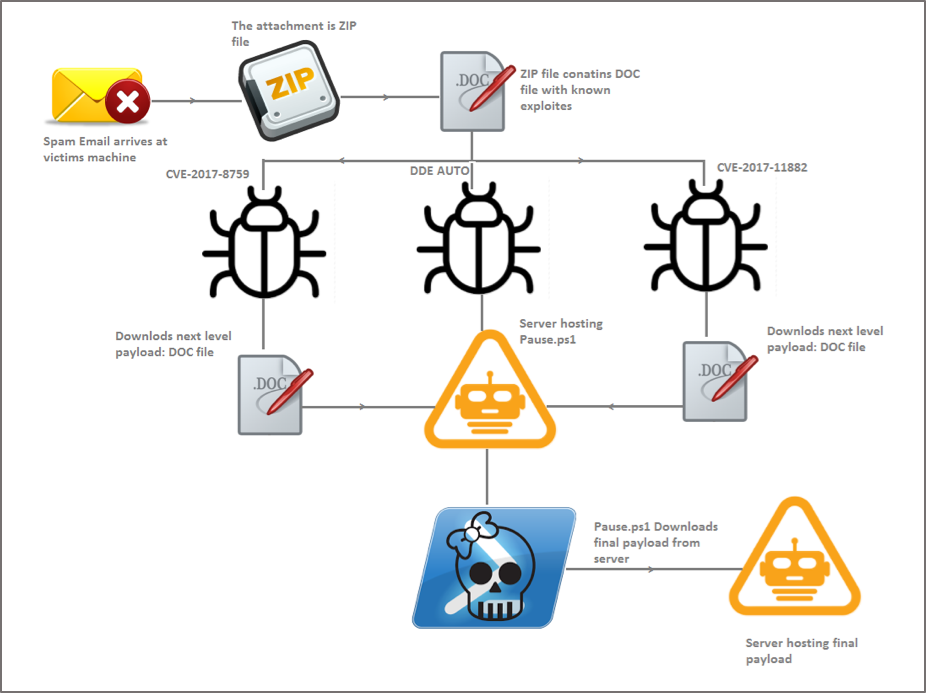
Researchers said attacks begin with spam campaigns delivering malicious ZIP archives that contain one of several type DOC files that ultimately exploit one of the three Microsoft Office vulnerabilities.
The first vulnerability is a .NET framework bug (CVE-2017-8759) patched by Microsoft last October. Targets that open an infected document allow attackers install programs, manipulate data and create new privileged accounts, Microsoft said. In the context of the attack described by FireEye, the infected DOC file contains an embedded OLE Object that, upon execution, triggers the download of an additional DOC file from a stored URL.
The second vulnerability (CVE-2017-11882) is 17-year-old remote code execution bug found in an Office executable called Microsoft Equation Editor. That bug was patched as part of Microsoft’s Nov. 2017 Patch Tuesday release. Similar to the previous vulnerability, victims that open a specially crafted DOC automatically download an additional DOC file that contains a PowerShell command used to download the final payload.
Microsoft doesn’t consider the third flaw, Dynamic Data Exchange (DDE) a vulnerability. Instead, it insists that DDE is a product feature. However, in November it released guidance to admins as to how to safely disable the feature via new registry settings for Office.
DDE is a protocol that establishes how apps send messages and share data through shared memory. However, attackers have found great success over the past year with macro-based malware exploiting DDE to launch droppers, exploits and malware.
In the case of the most recent attacks, FireEye said the DDE is also used to deliver a dropper.
“In all these techniques, the same domain is used to download the next level payload (Pause.ps1), which is another PowerShell script that is Base64 encoded,” researchers wrote. “The Pause.ps1 script is responsible for resolving the APIs required for code injection.” Ultimately, Pause.ps1 acts as another dropper to deliver the final “core payload”, the Zyklon malware.
“Zyklon is a publicly available, full-featured backdoor capable of keylogging, password harvesting, downloading and executing additional plugins, conducting distributed denial-of-service (DDoS) attacks, and self-updating and self-removal,” FireEye wrote. “The malware can download several plugins, some of which include features such as cryptocurrency mining and password recovery, from browsers and email software.”
In this case Zyklon is also configured to cloak communications with its command-and-control via the Tor network. “The Zyklon executable contains another encrypted file in its .Net resource section named tor. This file is decrypted and injected into an instance of InstallUtiil.exe, and functions as a Tor anonymizer,” researchers said.
From there the malware can be used by an attacker to carry out a number of different tasks, download new plugins, steal passwords or open a proxy to establish a reverse Socks5 proxy server on infected host machines, researchers said.
“These types of threats show why it is very important to ensure that all software is fully updated. Additionally, all industries should be on alert, as it is highly likely that the threat actors will eventually move outside the scope of their current targeting,” FireEye said.