Malware authors have developed a new, and frighteningly effective, tactic that uses a feature built into all of the modern browsers to redirect users to malicious sites without their knowledge or action.
In a worrisome new twist, attackers have begun using proxy auto-config (PAC) files, which are designed to enable browsers to automatically select which proxy server to use to get a specific URL. It’s a useful technique for administrators interested in pushing their users through a particular proxy server on their way to the Web. But now, malware writers, particularly the creators of Brazilian banker Trojans, have latched onto PAC files as a way to push victims to phishing sites.
After being infected by a Trojan banker, if a user tries to access some
of the websites listed in the script, they will be redirected to a
phishing domain hosted at the malicious proxy server.
A lot of the Brazilian malware is using this trick nowadays. Not only
Internet Explorer users are affected, but also users of Firefox and
Chrome. The malware changes the file prefs.js, inserting the malicious
proxy in it:
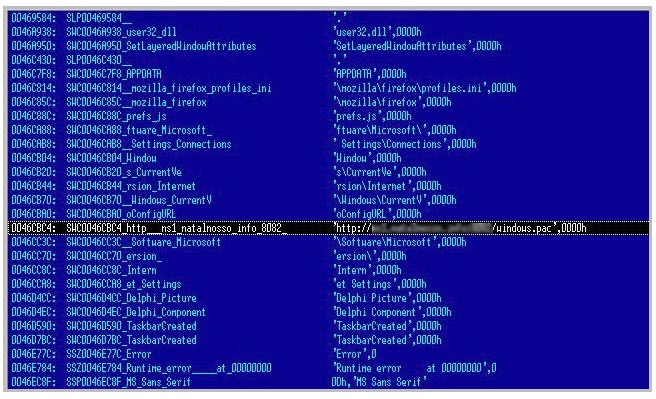
The banker Trojans also take the extra step of inserting a malicious DLL into the startup routine so that the user can’t overwrite or remove the malicious script.
As users have gotten savvier about the existing tactics of phishers–fake emails, fraudulent Web sites–it’s become more difficult for the attackers to attract victims. Less obvious tactics like the use of malicious PAC files, are becoming more useful and effective.









